| Oracle® Enterprise Manager Advanced Configuration 10g Release 3 (10.2.0.3.0) Part Number B40002-02 |
|
|
View PDF |
| Oracle® Enterprise Manager Advanced Configuration 10g Release 3 (10.2.0.3.0) Part Number B40002-02 |
|
|
View PDF |
Firewalls protect a company's Information Technology (IT) infrastructure by providing the ability to restrict network traffic by examining each network packet and determining the appropriate course of action.
Firewall configuration typically involves restricting the ports that are available to one side of the firewall, for example the Internet. It can also be set up to restrict the type of traffic that can pass through a particular port such as HTTP. If a client attempts to connect to a restricted port (a port not covered by a security "rule") or uses a protocol that is incorrect, then the client will be disconnected immediately by the firewall. Firewalls can also be used within a company Intranet to restrict user access to specific servers.
You can deploy the components of Oracle Enterprise Manager on different hosts throughout your enterprise. These hosts can be separated by firewalls. This chapter describes how firewalls can be configured to allow communication between the Enterprise Manager components.
See Also:
Chapter 3 for more information about some of the ways you can configure the Grid Control components on your networkThis chapter contains the following topics:
Firewall Configurations for Enterprise Management Components
Viewing a Summary of the Ports Assigned During the Application Server Installation
Firewall configuration should be the last phase of Enterprise Manager deployment. Before you configure your firewalls, make sure you are able to log in to the Grid Control Console and that your Management Agents are up and monitoring targets.
If you are deploying Enterprise Manager in an environment where firewalls are already installed, open the default Enterprise Manager communication ports for all traffic until you have completed the installation and configuration processes and are certain that you are able to log in to the Oracle Enterprise Manager 10g Grid Control Console and that your Oracle Management Agents are up and monitoring targets.
The default communication ports for Enterprise Manager are assigned during the installation. If you modify the default ports, be sure to use the new port assignments when you configure the firewalls.
See Also:
Chapter 12, "Reconfiguring the Management Agent and Management Service" for information about locating and changing the default ports for the Oracle Management Service and the Oracle Management AgentIf you are enabling Enterprise Manager Framework Security for the Management Service, the final step in that configuration process is to restrict uploads from the Management Agents to secure channels only. Before completing that step, configure your firewalls to allow both HTTP and HTTPS traffic between the Management Agent and Management Repository and test to be sure that you can log in to Enterprise Manager and that data is being uploaded to the Management Repository.
After you have confirmed that the Management Service and Management Agents can communicate with both protocols enabled, complete the transition to secure mode and change your firewall configuration as necessary. If you incrementally configure your firewalls, it will be easier to troubleshoot any configuration problems.
Your main task in enabling Enterprise Manager to work in a firewall-protected environment is to take advantage of proxy servers whenever possible, to make sure only the necessary ports are open for secure communications, and to make sure that only data necessary for running your business is allowed to pass through the firewall.
The following sections describe the ports and types of data required by Enterprise Manager in a secure, firewall-protected environment:
Configuring the Management Agent on a Host Protected by a Firewall
Configuring the Management Service on a Host Protected by a Firewall
Firewalls Between the Management Service and the Management Repository
Firewalls Between the Grid Control and a Managed Database Target
Configuring Firewalls to Allow ICMP and UDP Traffic for Beacons
Configuring Firewalls When Managing Oracle Application Server
Figure 6–1 provides a topology of an Enterprise Manager grid environment that is using a firewall, and also illustrates the default ports that can be used.
The conventions used in the preceding illustration are as follows:
Table 6-1 Conventions Used
| Convention | Description |
|---|---|
|
C |
Is the entity that is making the call. |
|
* |
Enterprise Manager will default to the first available port within an Enterprise Manager set range. |
|
** |
Enterprise Manager will default to the first available port. |
|
*** |
Are the Database listener ports. |
Note:
The direction of the arrows specify the direction of ports.
Port 1159, 4898-4989 specify that 1159 is the default. If this port is not available, the Management Service will search in the range that is specified.
To clone between two target hosts separated by a firewall, the agents will need to communicate to each other on the agent ports. The initiating agent will make the call.
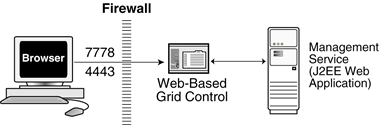
Connections from your browser to the Oracle Enterprise Manager 10g Grid Control Console are performed over the default port used for your Oracle HTTP Server.
For example, the default, non-secure port for the Oracle HTTP Server is usually port 7778. If you are accessing the Grid Control Console using the following URL and port, then you must configure the firewall to allow the Grid Control Console to receive HTTP traffic over port 7778:
http://mgmthost.acme.com:7778/em
On the other hand, if you have enabled security for your Oracle HTTP Server, you are likely using the default secure port for the server, which is usually port 4443. If you are accessing the Grid Control Console using the following URL and port, then you must configure the firewall to allow the Grid Control Console to receive HTTP traffic over port 4443:
https://mgmthost.acme.com:4443/em
Figure 6-1 shows the typical configuration of a firewall between your browser and the Grid Control Console Web-based console that is rendered by the Management Service.
Figure 6-1 Firewall Between Your Browser and the Grid Control Console
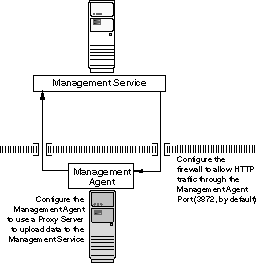
If your Management Agent is installed on a host that is protected by a firewall and the Management Service is on the other side of the firewall, you must perform the following tasks:
Configure the Management Agent to use a proxy server for its uploads to the Management Service.
Configure the firewall to allow incoming HTTP traffic from the Management Service on the Management Agent port. Regardless of whether or not Enterprise Manager Framework Security has been enabled, the default port is 3872. If this default port is not available, the default port range between 1830 - 1849 is used. Incoming traffic can be received only if the port corresponding to the Management Agent is open in the firewall.
Figure 6-2 illustrates the connections the Management Agent must make when it is protected by a firewall.
Figure 6-2 Configuration Tasks When the Management Agent Is Behind a Firewall
You can configure the Management Agent to use a proxy server for its communications with a Management Service outside the firewall, or to manage a target outside the firewall.
Use a text editor to open the following Management Agent configuration file:
AGENT_HOME/sysman/config/emd.properties (UNIX) AGENT_HOME\sysman\config\emd.properties (Windows)
Locate the following entry in the emd.properties file:
# If it is necessary to go through an http proxy server to get to the # repository, uncomment the following lines #REPOSITORY_PROXYHOST= #REPOSITORY_PROXYPORT=
To enable support for authenticating the proxy server, the following additional properties need to be specified.
#REPOSITORY_PROXYREALM= #REPOSITORY_PROXYUSER= #REPOSITORY_PROXYPWD=
Edit the following properties by removing the pound sign (#) at the start of each line and entering a value as follows:
# If it is necessary to go through an http proxy server to get to the # repository, uncomment the following lines REPOSITORY_PROXYHOST=proxyhostname.domain REPOSITORY_PROXYPORT=proxy_port REPOSITORY_PROXYREALM=realm REPOSITORY_PROXYUSER=proxyuser REPOSITORY_PROXYPWD=proxypassword
For example:
REPOSITORY_PROXYHOST=proxy42.acme.com REPOSITORY_PROXYPORT=80 REPOSITORY_PROXYREALM= REPOSITORY_PROXYUSER= REPOSITORY_PROXYPWD=
Save your changes and close the emd.properties file.
Stop and start the Management Agent.
Note:
The proxy password will be rewritten when you restart the Management Agent.While the Management Agents in your environment must upload data from your managed hosts to the Management Service, the Management Service must also communicate with the Management Agents. As a result, if the Management Agent is protected by a firewall, the Management Service must be able to contact the Management Agent through the firewall on the Management Agent port.
By default, the Enterprise Manager installation procedure assigns port 1830 to the Management Agent. However, if that port is occupied, the installation may assign an alternate port number.
Note:
The port number for the Management Agent does not change when you enable Enterprise Manager Framework Security. For more information, see "Configuring Security for Grid Control"In addition, administrators can change the Management Agent port after the installation.
See Also:
"Chapter 12, "Reconfiguring the Management Agent and Management Service" for information about locating and changing the default ports for the Oracle Management Service and the Oracle Management Agent.After you determine the port number assigned to the Management Agent, you must then configure the firewall to allow incoming HTTP or HTTPS traffic (depending upon whether or not you have enabled Enterprise Manager Framework Security) on that port.
See Also:
Your firewall documentation for more information about opening specific ports for HTTP or HTTPS traffic."Configuring Security for Grid Control" for information about Enterprise Manager Framework Security
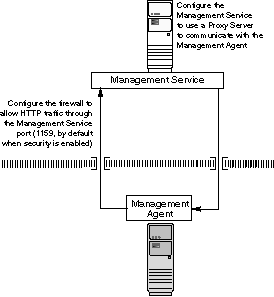
If your Management Service is installed on a host that is protected by a firewall and the Management Agents that provide management data are on the other side of the firewall, you must perform the following tasks:
Configure the Management Service to use a proxy server for its communications to the Management Agents.
Configure the firewall to allow incoming HTTP traffic from the Management Agents on the Management Repository upload port.
If you have enabled Enterprise Manager Framework Security, the upload URL uses port 1159 by default. If this port is not available, Enterprise Manager will default to first available port in the range 4898-4989. If you have not enabled Enterprise Manager Framework Security, the upload port is the first available port in the range 4889 - 4897.
Figure 6-3 illustrates the connections the Management Agent must make when it is protected by a firewall.
Figure 6-3 Configuration Tasks When the Management Service Is Behind a Firewall
This section describes how to configure the Management Service to use a proxy server for its communications with Management Agents outside the firewall.
Note:
The proxy configuration properties described in this section are the same Management Service properties you must modify if your network is protected by a firewall and you want Enterprise Manager to search automatically for critical patches and patch sets. For more information, see "Specifying Patching Credentials" in the Enterprise Manager online help.To configure the Management Service to use a proxy server:
Use a text editor to open the following configuration file in the Management Service home directory:
ORACLE_HOME/sysman/config/emoms.properties
Add the following entries to emoms.properties file:
proxyHost=proxyhost.domain proxyPort=proxy_port dontProxyFor=.domain1, .domain2, .domain3, ... proxyRealm=realm proxyUser=proxyuser proxyPwd=proxypassword
For example:
proxyHost=proxy42.acme.com proxyHost=80 dontProxyFor=.acme.com, .acme.us.com proxyRealm proxyUser proxyPwd
The dontProxyFor property identifies specific URL domains for which the proxy will not be used. The proxyRealm property indicates the protected space that requires authentication.
Save your changes and close the emoms.properties file.
Stop and start the Management Service:
$PROMPT> ORACLE_HOME/bin/emctl stop oms $PROMPT> ORACLE_HOME/bin/emctl start oms
Note:
The proxy password will be rewritten when you restart the Management Service.When you configure the Management Service to use a proxy server, it is important to understand the purpose of the dontProxyFor property, which identifies specific URL domains for which the proxy will not be used.
For example, suppose the following were true:
You have installed the Management Service and several Management Agents on hosts that are inside the company firewall. These hosts are in the internal .acme.com and .acme.us.com domains.
You have installed several additional Management Agents on hosts that are outside the firewall. These hosts are installed in the .acme.uk domain.
You have configured Enterprise Manager to automatically check for critical software patches on the OracleMetaLink Internet site.
In this scenario, you want the Management Service to connect directly to the Management Agents inside the firewall without using the proxy server. On the other hand, you want the Management Service to use the proxy server to contact the Management Agents outside the firewall, as well as the OracleMetaLink Internet site, which resides at the following URL:
http://metalink.oracle.com
The following entry in the emoms.properties file will prevent the Management Service from using the proxy server for connections to the Management Agents inside the firewall. Connections to OracleMetaLink and to Management Agents outside the firewall will be routed through the proxy server:
proxyHost=proxy42.acme.com proxyHost=80 dontProxyFor=.acme.com, .acme.us.com
While the Management Agents in your environment must contact the Management Agents on your managed hosts, the Management Service must also be able to receive upload data from the Management Agents. If the Management Service is behind a firewall, you must configure the firewall to allow the Management Agents to upload data on the upload port.
By default, the Enterprise Manager installation procedure assigns port 4889 as the Repository upload port. However, if that port is occupied, the installation will assign an alternate port number.
In addition, when you enable Enterprise Manager Framework Security, the upload port is automatically changed to the secure 1159 HTTPS port.
See Also:
"Configuring Security for Grid Control" for information about Enterprise Manager Framework SecurityAdministrators can also change the upload port after the installation.
See Also:
Chapter 12, "Reconfiguring the Management Agent and Management Service" for information about locating and changing the default ports for the Oracle Management Service and the Oracle Management Agent.After you determine the port number assigned to the Management Service upload port, you must then configure the firewall to allow incoming HTTP or HTTPS traffic (depending upon whether or not you have enabled Enterprise Manager Framework Security) on that port.
See Also:
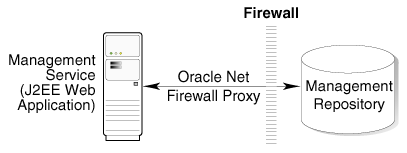
Your firewall documentation for more information about opening specific ports for HTTP or HTTPS trafficSecure connections between the Management Service and the Management Repository are performed using features of Oracle Advanced Security. As a result, if the Management Service and the Management Repository are separated by a firewall, you must configure the firewall to allow Oracle Net firewall proxy access.
See Also:
"Configuring Secure Sockets Layer Authentication" in the Oracle Database Advanced Security Administrator's GuideFigure 6-4 shows a typical configuration of a firewall between the Management Service and the Management Repository.
Figure 6-4 Firewall Between the Management Service and the Management Repository
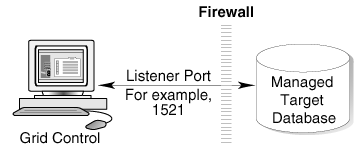
When you are using the Grid Control Console to manage a database, you must log in to the database from the Grid Control Console in order to perform certain monitoring and administration tasks. If you are logging in to a database on the other side of a firewall, you will need to configure the firewall to allow Oracle Net firewall proxy access.
Specifically, to perform any administrative activities on the managed database, you must be sure that the firewall is configured to allow the Oracle Management Service to communicate with the database through the Oracle Listener port.
You can obtain the Listener port by reviewing the Listener home page in the Grid Control Console.
Figure 6-5 shows a typical configuration of a firewall between the Management Service and the Management Repository.
Figure 6-5 Firewall Between the Grid Control and a Managed Database Target
Enterprise Manager supports the use of multiple Management Services that communicate with a common Management Repository. For example, using more than one Management Service can be helpful for load balancing as you expand your central management capabilities across a growing e-business enterprise.
When you deploy multiple Management Services in an environment protected by firewalls, be sure to consider the following:
Each Management Agent is configured to upload data to one Management Service. As a result, if there is a firewall between the Management Agent and its Management Service, you must configure the firewall to allow the Management Agent to upload data to the Management Service using the upload URL.
In addition, each Management Service must be able to contact any Management Agent in your enterprise so it can check for the availability of the Management Agent. As a result, you must be sure that your firewall is configured so that each Management Service you deploy can communicate over HTTP or HTTPS with any Management Agent in your enterprise.
Otherwise, a Management Service without access to a particular Management Agent may report incorrect information about whether or not the Management Agent is up and running.
See Also:
"About Availability" in the Enterprise Manager online help for information about how Enterprise Manager determines host and Management Agent availabilityOracle Beacons provide application performance availability and performance monitoring. They are part of the Application Performance Management features of Enterprise Manager.
See Also:
"About Application Performance Management" in the Enterprise Manager Online HelpEnterprise Manager uses the industry-standard Internet Control Message Protocol (ICMP) and User Datagram Protocol (UDP) to transfer data between Beacon and the network components you are monitoring. There may be situations where your Web application components and the Beacons you use to monitor those components are separated by a firewall. In those cases, you must configure your firewall to allow ICMP, UDP, and HTTP traffic.
If you are using Grid Control to manage instances of Oracle Application Server, there may be other ports that you need to access through a firewall, depending upon your configurations.
For example, when you are monitoring the performance of your Oracle Application Server instance from the Grid Control Console, you can click Administer on the Application Server Home page to display the Application Server Control Console. If the Oracle Application Server target you are monitoring is separated from the Grid Control Console by a firewall, you will need to configure the firewall to allow an HTTP or HTTPS connection through Application Server Control Console port (usually, 1810).
See Also:
Oracle Application Server Administrator's Guide for more information about configuring ports for Oracle Application ServerAs described in the previous sections of this chapter, it is important to understand and identify the ports used by each of the Oracle Enterprise Manager 10g components before you configure your firewalls.
When you install the Oracle Application Server 10g or the Oracle Enterprise Manager 10g Grid Control, you can view a list of the ports assigned during the application server installation by viewing the contents of the following file
ORACLE_HOME/install/portlist.ini
Note:
Theportlist.ini file lists the port numbers assigned during the installation. This file is not updated if port numbers are changed after the installation.In addition, you can use the Application Server Control Console to view a list of all the ports in use by the application server:
Navigate to the Application Server home page in the Application Server Control Console.
See Also:
"Viewing and Modifying Application Server Port Assignments" in the Enterprise Manager online helpFor secure agent install, ensure that the firewall settings are disabled for HTTP/HTTPS communication for Windows XP:
Go to Start, and then select Control Panel.
In Control Panel, click Windows Firewall.
In the Exceptions tab in the Windows Firewall dialog box, click Add Port.
In the Add a Port dialog box, specify the name and number of the port.
Click Change scope to specify the computers for which the port is unblocked.