| Oracle® XML DB Developer's Guide 11g Release 2 (11.2) Part Number E16659-03 |
|
|
PDF · Mobi · ePub |
| Oracle® XML DB Developer's Guide 11g Release 2 (11.2) Part Number E16659-03 |
|
|
PDF · Mobi · ePub |
This chapter describes how to access Oracle XML DB Repository data using FTP, HTTP(S)/WebDAV protocols.
This chapter contains these topics:
As described in Chapter 2, "Getting Started with Oracle XML DB" and Chapter 21, "Accessing Oracle XML DB Repository Data", Oracle XML DB Repository provides a hierarchical data repository in the database, designed for XML. Oracle XML DB Repository maps path names (or URLs) onto database objects of XMLType and provides management facilities for these objects.
Oracle XML DB also provides the Oracle XML DB protocol server. This supports standard Internet protocols, FTP, WebDAV, and HTTP(S), for accessing its hierarchical repository or file system. Note that HTTPS provides secure access to Oracle XML DB Repository.
These protocols can provide direct access to Oracle XML DB for many users without having to install additional software. The user names and passwords to be used with the protocols are the same as those for SQL*Plus. Enterprise users are also supported. Database administrators can use these protocols and resource APIs such as DBMS_XDB to access Oracle Automatic Storage Management (Oracle ASM) files and folders in the repository virtual folder /sys/asm.
See Also:
Chapter 21, "Accessing Oracle XML DB Repository Data" for more information about accessing repository information, and restrictions on that accessNote:
When accessing virtual folder /sys/asm using Oracle XML DB protocols, you must log in with the privileges of role DBA but as a user other than SYS.
Oracle XML DB protocols are not supported on EBCDIC platforms.
Oracle XML DB protocol server maintains a shared pool of sessions. Each protocol connection is associated with one session from this pool. After a connection is closed the session is put back into the shared pool and can be used to serve later connections.
Session pooling improves performance of HTTP(S) by avoiding the cost of re-creating session states, especially when using HTTP 1.0, which creates new connections for each request. For example, a couple of small files can be retrieved by an existing HTTP/1.1 connection in the time necessary to create a database session. You can tune the number of sessions in the pool by setting session-pool-size in Oracle XML DB xdbconfig.xml file, or disable it by setting pool size to zero.
Session pooling can affect users writing Java servlets, because other users can see session state initialized by another request for a different user. Hence, servlet writers should only use session memory, such as Java static variables, to hold data for the entire application rather than for a particular user. State for each user must be stored in the database or in a lookup table, rather than assuming that a session only exists for a single user.
Figure 28-1 illustrates the Oracle XML DB protocol server components and how they are used to access files in Oracle XML DB Repository and other data. Only the relevant components of the repository are shown
Figure 28-1 Oracle XML DB Architecture: Protocol Server
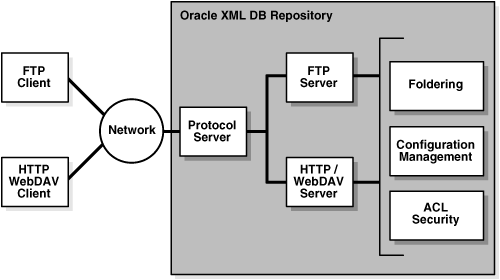
Oracle XML DB protocol server uses configuration parameters stored in /xdbconfig.xml to initialize its startup state and manage session level configuration. The following section describes the protocol-specific configuration parameters that you can configure in the Oracle XML DB configuration file. The session pool size and timeout parameters cannot be changed dynamically, that is, you must restart the database in order for these changes to take effect.
Figure 28-1 shows the parameters common to all protocols. All parameter names in this table, except those starting with /xdbconfig, are relative to the following XPath in the Oracle XML DB configuration schema:
/xdbconfig/sysconfig/protocolconfig/common
FTP-specific parameters – Table 28-2 shows the FTP-specific parameters. These are relative to the following XPath in the Oracle XML DB configuration schema:
/xdbconfig/sysconfig/protocolconfig/ftpconfig
HTTP(S)/WebDAV specific parameters, except servlet-related parameters – Table 28-3 shows the HTTP(S)/WebDAV-specific parameters. These parameters are relative to the following XPath in the Oracle XML DB configuration schema:
/xdbconfig/sysconfig/protocolconfig/httpconfig
See Also:
Chapter 34, "Administering Oracle XML DB" for more information about the configuration file xdbconfig.xml
"Configuring Default Namespace to Schema Location Mappings" for more information about the schemaLocation-mappings parameter
"Configuring XML File Extensions" for more information about the xml-extensions parameter
For examples of the usage of these parameters, see the configuration file, xdbconfig.xml.
Table 28-1 Common Protocol Configuration Parameters
| Parameter | Description |
|---|---|
|
|
Specifies the mapping of file extensions to mime types. When a resource is stored in Oracle XML DB Repository, and its mime type is not specified, this list of mappings is used to set its mime type. |
|
|
Specifies the mapping of file extensions to languages. When a resource is stored in Oracle XML DB Repository, and its language is not specified, this list of mappings is used to set its language. |
|
|
Specifies the mapping of file extensions to encodings. When a resource is stored in Oracle XML DB Repository, and its encoding is not specified, this list of mappings is used to set its encoding. |
|
|
Specifies the list of filename extensions that are treated as XML content by Oracle XML DB. |
|
|
Maximum number of sessions that are kept in the protocol server session pool |
|
|
If a connection is idle for this time (in hundredths of a second), then the shared server serving the connection is freed up to serve other connections. |
|
|
Time (in hundredths of a second) after which a session (and consequently the corresponding connection) is terminated by the protocol server if the connection has been idle for that time. This parameter is used only if the specific protocol session timeout is not present in the configuration |
|
|
Specifies the default schema location for a given namespace. This is used if the instance XML document does not contain an explicit |
|
|
Time period after which a WebDAV lock on a resource becomes invalid. This could be overridden by a Timeout specified by the client that locks the resource. |
Table 28-2 Configuration Parameters Specific to FTP
| Parameter | Description |
|---|---|
|
|
Size of the buffer, in bytes, used to read data from the network during an FTP |
|
|
Port on which FTP server listens. By default, this is |
|
|
Protocol over which the FTP server runs. By default, this is |
|
|
A user-defined welcome message that is displayed whenever an FTP client connects to the server. If this parameter is empty or missing, then the following default welcome message is displayed: "Unauthorized use of this FTP server is prohibited and may be subject to civil and criminal prosecution." |
|
|
Time (in hundredths of a second) after which an FTP connection is terminated by the protocol server if the connection has been idle for that time. |
Table 28-3 Configuration Parameters Specific to HTTP(S)/WebDAV (Except Servlet Parameters)
| Parameter | Description |
|---|---|
|
|
Port on which the HTTP(S)/WebDAV server listens, using protocol This parameter must be present, whether or not it is empty. Otherwise, validation of |
|
|
Port on which the HTTP(S)/WebDAV server listens, using protocol This parameter is optional, but, if present, then |
|
|
Protocol over which the HTTP(S)/WebDAV server runs on port This parameter must be present. Otherwise, validation of |
|
|
Protocol over which the HTTP(S)/WebDAV server runs on port This parameter is optional, but, if present, then |
|
|
Time (in hundredths of a second) after which an HTTP(S) session (and consequently the corresponding connection) is terminated by the protocol server if the connection has been idle for that time. |
|
|
Maximum size (in bytes) of an HTTP(S) header |
|
|
Maximum size (in bytes) of an HTTP(S) request body |
|
|
List of filenames that are considered welcome files. When an HTTP(S) |
|
|
The character set in which an HTTP(S) protocol server assumes incoming URL is encoded when it is not encoded in UTF-8 or the Content-Type field Charset parameter of the request. |
|
Indication of whether or not anonymous HTTP access to Oracle XML DB Repository data is allowed using an unlocked |
|
|
|
HTTP header that specifies the expiration date and time for a URL. See "Controlling URL Expiration Time". |
To enable Oracle XML DB Repository to use secure HTTP connections (HTTPS), a database administrator (DBA) must configure the database accordingly: configure parameters http2-port and http2-protocol, enable the HTTP Listener to use SSL, and enable launching of the TCPS Dispatcher. After doing this, the DBA must stop, then restart, the database and the listener.
See Also:
"Configuring Oracle XML DB using xdbconfig.xml" for information about configuring Oracle XML DB parametersA database administrator must carry out the following steps, to configure the HTTP Listener for SSL.
Note:
Configuring the HTTP Listener for SSL requires that you have the option Oracle Advanced Security.Create a wallet for the server and import a certificate – Use Oracle Wallet Manager to do the following:
Create a wallet for the server.
If a valid certificate with distinguished name (DN) of the server is not available, create a certificate request and submit it to a certificate authority. Obtain a valid certificate from the authority.
Import a valid certificate with the distinguished name (DN) of the server into the server.
Save the new wallet in obfuscated form, so that it can be opened without a password.
See Also:
Oracle Database Advanced Security Administrator's Guide for information about how to create a walletSpecify the wallet location to the server – Use Oracle Net Manager to do this. Ensure that the configuration is saved to disk. This step updates files sqlnet.ora and listener.ora.
Disable client authentication at the server, since most Web clients do not have certificates. Use Oracle Net Manager to do this. This step updates file sqlnet.ora.
Create a listening end point that uses TCP/IP with SSL – Use Oracle Net Manager to do this. This step updates file listener.ora.
See Also:
Oracle Database Advanced Security Administrator's Guide for detailed information regarding steps 1 through 4A database administrator must edit the database pfile to enable launching of a TCPS dispatcher during database startup. The following line must be added to the file, where SID is the SID of the database:
dispatchers=(protocol=tcps)(service=SIDxdb)
The database pfile location depends on your operating system, as follows:
MS Windows – PARENT/admin/orcl/pfile, where PARENT is the parent folder of folder ORACLE_HOME
UNIX, Linux – $ORACLE_HOME/admin/$ORACLE_SID/pfile
The protocol specifications, RFC 959 (FTP), RFC 2616 (HTTP), and RFC 2518 (WebDAV) implicitly assume an abstract, hierarchical file system on the server side. This is mapped to Oracle XML DB Repository. The repository provides:
Name resolution.
Security based on access control lists (ACLs). An ACL is a list of access control entries that determine which principals have access to a given resource or resources. See also Chapter 27, "Repository Access Control".
The ability to store and retrieve any content. The repository can store both binary data input through FTP and XML schema-based documents.
Oracle XML DB protocol server enhances the protocols by always checking if XML documents being inserted are based on XML schemas registered in Oracle XML DB Repository.
If the incoming XML document specifies an XML schema, then the Oracle XML DB storage to use is determined by that XML schema. This functionality is especially useful when you must store XML documents object-relationally in the database using simple protocols like FTP or WebDAV instead of using SQL statements.
If the incoming XML document is not XML schema-based, then it is stored as a binary document.
In certain cases, it may be useful to log the requests received and responses sent by a protocol server. This can be achieved by setting event number 31098 to level 2. To set this event, add the following line to your init.ora file and restart the database:
event="31098 trace name context forever, level 2"
The following sections describe FTP features supported by Oracle XML DB.
File Transfer Protocol (FTP) is one of the oldest and most popular protocols on the net. FTP is specified in RFC959 and provides access to heterogeneous file systems in a uniform manner. FTP works by providing well-defined commands (methods) for communication between the client and the server. The transfer of command messages and the return of status happens on a single connection. However, a new connection is opened between the client and the server for data transfer. With HTTP(S), commands and data are transferred using a single connection.
FTP is implemented by dedicated clients at the operating system level, file-system explorer clients, and browsers. FTP is typically session-oriented: a user session is created through an explicit logon, a number of files or directories are downloaded and browsed, and then the connection is closed.
Note:
For security reasons, FTP is disabled, by default. This is because the IETF FTP protocol specification requires that passwords be transmitted in clear text. Disabling is done by configuring the FTP server port as zero (0). To enable FTP, set theftp-port parameter to the FTP port to use, such as 2100.See Also:
RFC 959: FTP Protocol Specification – http://www.ietf.org/rfc/rfc959.txt
"Configuring Oracle XML DB using xdbconfig.xml" for information about configuring parameters
Oracle XML DB implements FTP, as defined by RFC 959, with the exception of the following optional features:
Record-oriented files, for example, only the FILE structure of the STRU method is supported. This is the most widely used structure for transfer of files. It is also the default specified by the specification. Structure mount is not supported.
Append.
Allocate. This pre-allocates space before file transfer.
Account. This uses the insecure Telnet protocol.
Abort.
For access to the repository, Oracle XML DB supports the following FTP client methods.
cdup – change working directory to parent directory
cwd – change working directory
dele – delete file (not directory)
list, nlst – list files in working directory
mkd – create directory
noop – do nothing (but timeout counter on connection is reset)
pasv, port – establish a TCP data connection
pwd – get working directory
quit – close connection and quit FTP session
retr – retrieve data using an established connection
rmd – remove directory
rnfr, rnto – rename file (two-step process: from file, to file)
stor – store data using an established connection
syst – get system version
type – change data type: ascii or image binary types only
user, pass – user login
See Also:
"FTP Quote Methods" for supported FTP quote methods
"Using FTP with Oracle ASM Files" for an example of using FTP method proxy
Oracle Database supports several FTP quote methods, which provide information directly to Oracle XML DB.
rm_r – Remove file or folder <resource_name>. If a folder, recursively remove all files and folders contained in <resource_name>.
quote rm_r <resource_name>
rm_f – Forcibly remove a resource.
quote rm_f <resource_name>
rm_rf – Combines rm_r and rm_f: Forcibly and recursively removes files and folders.
quote rm_rf <resource_name>
set_nls_locale – Specify the character-set encoding (<charset_name>) to be used for file and directory names in FTP methods (including names in method responses).
quote set_nls_locale {<charset_name> | NULL}
Only IANA character-set names can be specified for <charset_name>. If nls_locale is set to NULL or is not set, then the database character set is used.
set_charset – Specify the character set of the data to be sent to the server.
quote set_charset {<charset_name> | NULL}
The set_charset method applies to only text files, not binary files, as determined by the file-extension mapping to MIME types that is defined in configuration file xdbconfig.xml.
If the parameter provided to set_charset is <charset_name> (not NULL), then it specifies the character set of the data.
If the parameter provided to set_charset is NULL, or if no set_charset command is given, then the MIME type of the data determines the character set for the data.
If the MIME type is not text/xml), then the data is not assumed to be XML. The database character set is used.
If the MIME type is text/xml, then the data represents an XML document.
If a byte order markFoot 1 (BOM) is present in the XML document, then it determines the character set of the data.
If there is no BOM, then:
If there is an encoding declaration in the XML document, then it determines the character set of the data.
If there is no encoding declaration, then the UTF-8 character set is used.
Oracle Automatic Storage Management (Oracle ASM) organizes database files into disk groups for simplified management and added benefits such as database mirroring and I/O balancing. Database administrators can use protocols and resource APIs to access Oracle ASM files in the Oracle XML DB repository virtual folder /sys/asm. All files in /sys/asm are binary.
Typical uses are listing, copying, moving, creating, and deleting Oracle ASM files and folders. Example 28-1 is an example of navigating the Oracle ASM virtual folder and listing the files in a subfolder.
The structure of the Oracle ASM virtual folder, /sys/asm, is described in Chapter 21, "Accessing Oracle XML DB Repository Data". In Example 28-1, the disk groups are DATA and RECOVERY; the database name is MFG; and the directories created for aliases are dbs and tmp. This example navigates to a subfolder, lists its files, and copies a file to the local file system.
Example 28-1 Navigating Oracle ASM Folders
ftp> open myhost 7777
ftp> user system
Password required for SYSTEM
Password: password
ftp> cd /sys/asm
ftp> ls
DATA
RECOVERY
ftp> cd DATA
ftp> ls
dbs
MFG
ftp> cd dbs
ftp> ls
t_dbl.f
t_axl.f
ftp> binary
ftp> get t_dbl.f, t_axl.f
ftp> put my_db2.f
In Example 28-1, after connecting to and logging onto database myhost (first four lines), FTP methods cd and ls are used to navigate and list folders, respectively. When in folder /sys/asm/DATA/dbs, FTP command get is used to copy files t_db1.f and t_ax1.f to the current folder of the local file system. Then, FTP command put is used to copy file my_db2.f from the local file system to folder /sys/asm/DATA/dbs.
Database administrators can copy Oracle Automatic Storage Management (Oracle ASM) files from one database server to another or between the database and a local file system. Example 28-2 shows copying between two databases. For this, the proxy FTP client method can be used, if available. The proxy method provides a direct connection to two different remote FTP servers.
Example 28-2 copies an Oracle ASM file from one database to another. Terms with the suffix 1 correspond to database server1. Terms with the suffix 2 correspond to database server2. Note that, depending on your FTP client, the passwords you type might be echoed on your screen. Take the necessary precautions so that others do not see these passwords.
Example 28-2 Transferring Oracle ASM Files Between Databases with FTP proxy Method
1 ftp> open server1 port1 2 ftp> user username1 3 Password required for USERNAME1 4 Password: password-for-username1 5 ftp> cd /sys/asm/DATAFILE/MFG/DATAFILE 6 ftp> proxy open server2 port2 7 ftp> proxy user username2 8 Password required for USERNAME2 9 Password: password-for-username2 10 ftp> proxy cd /sys/asm/DATAFILE/MFG/DATAFILE 11 ftp> proxy put dbs2.f tmp1.f 12 ftp> proxy get dbs1.f tmp2.f
In Example 28-2:
Line 1 opens an FTP control connection to the Oracle XML DB FTP server, server1.
Lines 2–4 log the database administrator onto server1 as USERNAME1.
Line 5 navigates to /sys/asm/DATAFILE/MFG/DATAFILE on server1.
Line 6 opens an FTP control connection to the second database server, server2. At this point, the FTP command proxy ? could be issued to see the available FTP commands on the secondary connection. (This is not shown.)
Lines 7–9 log the database administrator onto server2 as USERNAME2.
Line 10 navigates to /sys/asm/DATAFILE/MFG/DATAFILE on server2.
Line 11 copies Oracle ASM file dbs2.f from server2 to Oracle ASM file tmp1.f on server1.
Line 12 copies Oracle ASM file dbs1.f from server1 to Oracle ASM file tmp2.f on server2.
You can use the Oracle XML DB configuration file, /xdbconfig.xml, to configure FTP to listen on any port. By default, FTP listens on a nonstandard, unprotected port. To use FTP on the standard port, 21, your database administrator must do the following:
(UNIX only) Use this shell command to ensure that the owner and group of executable file tnslsnr are root:
% chown root:root $ORACLE_HOME/bin/tnslsnr
(UNIX only) Add the following entry to the listener file, listener.ora, where hostname is your host name:
(DESCRIPTION = (ADDRESS = (PROTOCOL = TCP) (HOST = hostname) (PORT = 21)) (PROTOCOL_STACK = (PRESENTATION = FTP) (SESSION = RAW)))
(UNIX only) Use shell command id to determine the user_id and group_id that were used to install Oracle Database. oracle_installation_user is the name of the user who installed the database.
% id oracle_installation_user uid=user_id(oracle_installation_user) gid=group_id(dba)
(UNIX only) Stop, then restart the listener, using the following shell commands, where user_id and group_id are the UNIX user and group identifiers obtained in step 3.
% lsnrctl stop % tnslsnr LISTENER -user user_id -group group_id &
Use the ampersand (&), to execute the second command in the background. Do not use lsnrctl start to start the listener.
Use PL/SQL procedure DBMS_XDB.setftpport with SYS as SYSDBA to set the FTP port number to 21 in the Oracle XML DB configuration file /xdbconfig.xml.
SQL> exec DBMS_XDB.setFTPPort(21);
Force the database to reregister with the listener, using this SQL statement:
SQL> ALTER SYSTEM REGISTER;
Check that the listener is correctly configured, using this shell command:
% lsnrctl status
See Also:
Oracle Database Net Services Reference for information about listener parameters and file listener.ora
Oracle Database Net Services Reference, section "Port Number Limitations" for information about running on privileged ports
Starting with 11g Release 2 (11.2), Oracle Database supports the use of Internet Protocol Version 6, IPv6 (in addition to Internet Protocol Version 4). Example 28-3 shows how to make an FTP connection with the IPv6 address 2001::0db8:ffff:ffff:ffff.
Example 28-3 FTP Connection Using IPv6
ftp> open 2001::0db8:ffff:ffff:ffff 1521 Connected to 2001::0db8:ffff:ffff:ffff. 220- xmlhost.example.com Unauthorized use of this FTP server is prohibited and may be subject to civil and criminal prosecution. 220- xmlhost.example.com FTP server (Oracle XML DB/Oracle Database) ready. User (2001::0db8:ffff:ffff:ffff:(none)): username 331 pass required for USERNAME Password: password-for-username 230 USERNAME logged in ftp>
See Also:
Oracle Database Net Services Reference for information about IPv6Oracle XML DB protocol server also provides session management for this protocol. After a short wait for a new command, FTP returns to the protocol layer and the shared server is freed up to serve other connections. The duration of this short wait is configurable by changing parameter call-timeout in the Oracle XML DB configuration file. For high traffic sites, call-timeout should be shorter, so that more connections can be served. When new data arrives on the connection, the FTP server is re-invoked with fresh data. So, the long running nature of FTP does not affect the number of connections which can be made to the protocol server.
See Also:
"Configuring Oracle XML DB using xdbconfig.xml" for information about configuring Oracle XML DB parametersIf you are frequently disconnected from the server and must reconnect and traverse the entire directory before doing the next operation, you may need to modify the default timeout value for FTP sessions. If the session is idle for more than this period, it gets disconnected. You can increase the timeout value (default = 6000 centiseconds) by modifying the configuration document as follows and then restart the database:
Do not use FTP in passive mode to connect remotely to a server that has HOSTNAME configured in listener.ora as localhost or 127.0.0.1. If the HOSTNAME specified in server file listener.ora is localhost or 127.0.0.1, then the server is configured for local use only. If you try to connect remotely to the server using FTP in passive mode, the FTP client fails. This is because the server passes IP address 127.0.0.1 (derived from HOSTNAME) to the client, which makes the client try to connect to itself, not to the server.
Oracle XML DB implements HyperText Transfer Protocol (HTTP), HTTP 1.1 as defined in the RFC2616 specification.
The Oracle XML DB HTTP(S) component in the Oracle XML DB protocol server implements the RFC2616 specification with the exception of the following optional features:
gzip and compress transfer encodings
byte-range headers
The TRACE method (used for proxy error debugging)
Cache-control directives (these require you to specify expiration dates for content, and are not generally used)
TE, Trailer, Vary & Warning headers
Weak entity tags
Web common log format
Multi-homed Web server
See Also:
RFC 2616: HTTP 1.1 Protocol Specification—http://www.ietf.org/rfc/rfc2616.txtDigest Authentication (RFC 2617) is not supported. Oracle XML DB supports Basic Authentication, where a client sends the user name and password in clear text in the Authorization header.
For access to the repository, Oracle XML DB supports the following HTTP(S) client methods.
OPTIONS – get information about available communication options
GET – get document/data (including headers)
HEAD – get headers only, without document body
PUT – store data in resource
DELETE – delete resource
The semantics of these HTTP(S) methods is in accordance with WebDAV. Servlets and Web services may support additional HTTP(S) methods, such as POST.
See Also:
"Supported WebDAV Client Methods" for supported HTTP(S) client methods involving WebDAVYou can use the Oracle XML DB configuration file, /xdbconfig.xml, to configure HTTP(S) to listen on any port. By default, HTTP(S) listens on a nonstandard, unprotected port. To use HTTP or HTTPS on a standard port (80 for HTTP, 443 for HTTPS), your database administrator must do the following:
(UNIX only) Use this shell command to ensure that the owner and group of executable file tnslsnr are root:
% chown root:root $ORACLE_HOME/bin/tnslsnr
(UNIX only) Add the following entry to the listener file, listener.ora, where hostname is your host name, and port_number is 80 for HTTP or 443 for HTTPS:
(DESCRIPTION = (ADDRESS = (PROTOCOL = TCP) (HOST = hostname) (PORT = port_number)) (PROTOCOL_STACK = (PRESENTATION = HTTP) (SESSION = RAW)))
(UNIX only) Use shell command id to determine the user_id and group_id that were used to install Oracle Database. oracle_installation_user is the name of the user who installed the database.
% id oracle_installation_user uid=user_id(oracle_installation_user) gid=group_id(dba)
(UNIX only) Stop, then restart the listener, using the following shell commands, where user_id and group_id are the UNIX user and group identifiers obtained in step 3.
% lsnrctl stop % tnslsnr LISTENER -user user_id -group group_id &
Use the ampersand (&), to execute the second command in the background. Do not use lsnrctl start to start the listener.
Use PL/SQL procedure DBMS_XDB.sethtpport with SYS as SYSDBA to set the HTTP(S) port number to port_number in the Oracle XML DB configuration file /xdbconfig.xml, where port_number is 80 for HTTP or 443 for HTTPS:
SQL> exec DBMS_XDB.setHTTPPort(port_number);
Force the database to reregister with the listener, using this SQL statement:
SQL> ALTER SYSTEM REGISTER;
Check that the listener is correctly configured:
% lsnrctl status
See Also:
Oracle Database Net Services Reference for information about listener parameters and file listener.ora
Oracle Database Net Services Reference, section "Port Number Limitations" for information about running on privileged ports
Starting with 11g Release 2 (11.2), Oracle Database supports the use of Internet Protocol Version 6, IPv6 (in addition to Internet Protocol Version 4). IPv6 addresses in URLs are enclosed in brackets ([]). Here is an example:
http://[2001::0db8:ffff:ffff:ffff]:8080/
See Also:
Oracle Database Net Services Reference for information about IPv6If properly configured, you can access Oracle XML DB Repository in a secure fashion, using HTTPS. See "Configuring Secure HTTP (HTTPS)" for configuration information.
Note:
If Oracle Database is installed on Microsoft Windows XP with Service Pack 2 (SP2), then you must use HTTPS for WebDAV access to Oracle XML DB Repository, or else you must make appropriate modifications to the Windows XP Registry. For information about the latter, seehttp://www.microsoft.com/technet/prodtechnol/winxppro/maintain/sp2netwk.mspx#XSLTsection129121120120Optional configuration parameter expire specifies an HTTP Expires header. This header acts as a directive to the HTTP client, to specify the expiration date and time for a URL.
If cached, the document targeted by a URL can be fetched from the client cache rather than from the server, until this expiration time has passed. After that time, the cache copy is out-of-date and a new copy must be obtained from the source (server).
The Oracle XML DB syntax for the Expires header, which is used in the expire configuration element, is a subset of the so-called alternate syntax defined for the ExpiresDefault directive of the Apache module mod_expires. See http://httpd.apache.org/docs/2.0/mod/mod_expires.html#AltSyn for that syntax.
These are the Oracle XML DB restrictions to the ExpiresDefault syntax:
You cannot use access as the <base>. Only now and modification are allowed.
The <type> values must appear in order of decreasing time period. For example, year must appear before, not after, month, since a year is a longer time period than a month.
You can use at most one occurrence of each of the different <type> values. For example, you cannot have multiple year entries or multiple day entries.
Optional configuration parameter allow-repository-anonymous-access controls whether or not anonymous HTTP access to Oracle XML DB Repository data is allowed using an unlocked ANONYMOUS user account. The default value is false, meaning that unauthenticated access to repository data is blocked. To allow anonymous HTTP access to the repository, you must set this parameter to true, and unlock the ANONYMOUS user account.
Caution:
There is an inherent security risk associated with allowing anonymous access to the repository.Parameter allow-repository-anonymous-access does not control anonymous access to the repository using servlets. Each servlet has its own security-role-ref parameter value to control its access.
See Also:
Table 28-3 for information about parameter allow-repository-anonymous-access
"Configuring Oracle XML DB using xdbconfig.xml" for information about configuring Oracle XML DB parameters
"Configuring Oracle XML DB Servlets" for information about parameter security-role-ref
Oracle XML DB supports Java servlets. To use a Java servlet, it must be registered with a unique name in the Oracle XML DB configuration file, along with parameters to customize its action. It should be compiled, and loaded into the database. Finally, the servlet name must be associated with a pattern, which can be an extension such as *.jsp or a path name such as /a/b/c or /sys/*, as described in Java servlet application program interface (API) version 2.2.
While processing an HTTP(S) request, the path name for the request is matched with the registered patterns. If there is a match, then the protocol server invokes the corresponding servlet with the appropriate initialization parameters. For Java servlets, the existing Java Virtual Machine (JVM) infrastructure is used. This starts the JVM if need be, which in turn invokes a Java method to initialize the servlet, create response, and request objects, pass these on to the servlet, and run it.
You can use the PL/SQL gateway to implement a Web application entirely in PL/SQL. There are two implementations of the PL/SQL gateway:
mod_plsql – a plug-in of Oracle HTTP Server that lets you invoke PL/SQL stored procedures using HTTP(S). Oracle HTTP Server is a component of both Oracle Application Server and Oracle Database. Do not confuse Oracle HTTP Server with the HTTP component of the Oracle XML DB protocol server.
the embedded PL/SQL gateway – a gateway implementation that runs in the Oracle XML DB HTTP listener.
With the PL/SQL gateway (either implementation), a Web browser sends an HTTP(S) request in the form of a URL that identifies a stored procedure and provides it with parameter values. The gateway translates the URL, calls the stored procedure with the parameter values, and returns output (typically HTML) to the Web-browser client.
Using the embedded PL/SQL gateway simplifies installation, configuration, and administration of PL/SQL based Web applications. The embedded gateway uses the Oracle XML DB protocol server, not Oracle HTTP Server. Its configuration is defined by the Oracle XML DB configuration file, /xdbconfig.xml. However, the recommended way to configure the embedded gateway is to use the procedures in PL/SQL package DBMS_EPG, not to edit file /xdbconfig.xml.
See Also:
Oracle Database Advanced Application Developer's Guide for information on using and configuring the embedded PL/SQL gateway
Chapter 34, "Administering Oracle XML DB" for information on the configuration definition of the embedded gateway in /xdbconfig.xml
Oracle Fusion Middleware Administrator's Guide for Oracle HTTP Server for conceptual information about using the PL/SQL gateway
Oracle HTTP Server mod_plsql User's Guide for information about mod_plsql
When a client sends multibyte data in a URL, RFC 2718 specifies that the client should send the URL using the %HH format, where HH is the hexadecimal notation of the byte value in UTF-8 encoding. The following are URL examples that can be sent to Oracle XML DB in an HTTP(S) or WebDAV context:
http://urltest/xyz%E3%81%82%E3%82%A2 http://%E3%81%82%E3%82%A2 http://%E3%81%82%E3%82%A2/abc%E3%81%86%E3%83%8F.xml
Oracle XML DB processes the requested URL, any URLs within an IF header, any URLs within the DESTINATION header, and any URLs in the REFERRED header that contains multibyte data.
The default-url-charset configuration parameter can be used to accept requests from some clients that use other, nonconforming, forms of URL, with characters that are not ASCII. If a request with such characters fails, try setting this value to the native character set of the client environment. The character set used in such URL fields must be specified with an IANA charset name.
default-url-charset controls the encoding for nonconforming URLs. It is not required to be set unless a nonconforming client that does not send the Content-Type charset is used.
See Also:
RFC 2616: HTTP 1.1 Protocol Specification, http://www.ietf.org/rfc/rfc2616.txt
"Configuring Oracle XML DB using xdbconfig.xml" for information about configuring Oracle XML DB parameters
Characters that are not ASCII that appear in URLs passed to an HTTP server should be converted to UTF-8 and escaped in the %HH format, where HH is the hexadecimal notation of the byte value. For flexibility, the Oracle XML DB protocol server interprets the incoming URLs by testing whether it is encoded in one of the following character sets in the order presented here:
UTF-8
Charset parameter of the Content-Type field of the request, if specified
Character set, if specified, in the default-url-charset configuration parameter
Character set of the database
See Also:
"Configuring Oracle XML DB using xdbconfig.xml" for information about configuring Oracle XML DB parametersThe following sections describe how character sets are controlled for data transferred using HTTP(S).
The character set of the HTTP(S) request body is determined with the following algorithm:
The Content-Type header is evaluated. If the Content-Type header specifies a charset value, the specified charset is used.
The MIME type of the document is evaluated as follows:
If the MIME type is "*/xml", the character set is determined as follows:
- If a BOM is present, then UTF-16 is used.
- If an encoding declaration is present, the specified encoding is used.
- If neither a BOM nor an encoding declaration is present, UTF-8 is used.
If the MIME type is text, ISO8859-1 is used.
If the MIME type is neither "*/xml" nor text, the database character set is used.
There is a difference between HTTP(S) and SQL or FTP. For text documents, the default is ISO8859-1, as specified by the IETF.org RFC 2616: HTTP 1.1 Protocol Specification.
The response generated by Oracle XML DB HTTP Server is in the character set specified in the Accept-Charset field of the request. Accept-Charset can have a list of character sets. Based on the q-value, Oracle XML DB chooses one that does not require conversion. This might not necessarily be the charset with the highest q-value. If Oracle XML DB cannot find one, then the conversion is based on the highest q-value.
Web Distributed Authoring and Versioning (WebDAV) is an IETF standard protocol used to provide users with a file-system interface to Oracle XML Repository over the Internet. The most popular way of accessing a WebDAV server folder is through WebFolders using Microsoft Windows.
WebDAV is an extension to the HTTP 1.1 protocol that lets an HTTP server act as a file server. It lets clients perform remote Web content authoring through a coherent set of methods, headers, request body formats and response body formats. For example, a DAV-enabled editor can interact with an HTTP/WebDAV server as if it were a file system. WebDAV provides operations to store and retrieve resources, create and list contents of resource collections, lock resources for concurrent access in a coordinated manner, and to set and retrieve resource properties.
Oracle XML DB supports the following WebDAV features:
Foldering, specified by RFC2518
Access Control
WebDAV is a set of extensions to the HTTP(S) protocol that allow you to edit or manage your files on remote Web servers. WebDAV can also be used, for example, to:
Share documents over the Internet
Edit content over the Internet
See Also:
RFC 2518: WebDAV Protocol Specification,http://www.ietf.org/rfc/rfc2518.txtOracle XML DB supports the contents of RFC2518, with the following exceptions:
Lock-NULL resources create zero-length resources in the file system, and cannot be converted to folders.
Methods COPY, MOVE and DELETE comply with section 2 of the Internet Draft titled 'Binding Extensions to WebDAV'.
Depth-infinity locks
Only Basic Authentication is supported.
For access to the repository, Oracle XML DB supports the following HTTP(S)/WebDAV client methods.
PROPFIND (WebDAV-specific) – get properties for a resource
PROPPATCH (WebDAV-specific) – set or remove resource properties
LOCK (WebDAV-specific) – lock a resource (create or refresh a lock)
UNLOCK (WebDAV-specific) – unlock a resource (remove a lock)
COPY (WebDAV-specific) – copy a resource
MOVE (WebDAV-specific) – move a resource
MKCOL (WebDAV-specific) – create a folder resource (collection)
See Also:
"Supported HTTP(S) Client Methods" for additional supported HTTP(S) client methods
"Privileges" for information about WebDAV privileges
If Oracle Database is installed on Microsoft Windows XP with Service Pack 2 (SP2), then you must use a secure connection (HTTPS) for WebDAV access to Oracle XML DB Repository, or else you must make appropriate modifications to the Windows XP Registry.
See Also:
http://www.microsoft.com/technet/prodtechnol/winxppro/maintain/sp2netwk.mspx#XSLTsection129121120120 for information about making necessary modifications to the Windows XP registry
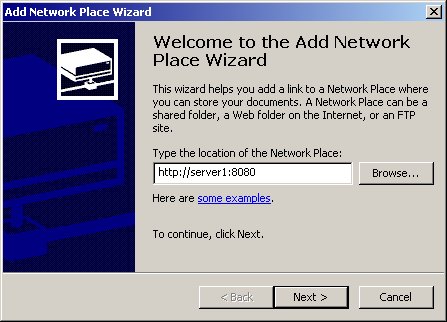
To create a WebFolder in Windows 2000, follow these steps:
Start > My Network Places.
Double-click Add Network Place.
Click Next.
Type the location of the folder, for example:
http://Oracle_server_name:HTTP_port_number
See Figure 28-2.
Click Next.
Enter any name to identify this WebFolder
Click Finish.
You can access Oracle XML DB Repository the same way that you access any Windows folder.
Figure 28-2 Creating a WebFolder in Microsoft Windows
Footnote Legend
Footnote 1: BOM is a Unicode-standard signature that indicates the order of the stream of bytes that follows it.