14 Using Oracle Database with Microsoft Active Directory
This chapter describes how to configure and use Microsoft Active Directory as the LDAP directory.
This chapter contains these topics:
-
Overview of Oracle Components That Integrate with Active Directory
-
Overview of Requirements for Using Oracle Database with Active Directory
-
Configuring Client Computers and Oracle Database to Use Active Directory
-
Overview of Access Control List Management for Oracle Directory Objects
Overview of Microsoft Active Directory Support
This section describes how Microsoft Active Directory is used as an LDAP directory server by Oracle Database.
This section contains these topics:
About Microsoft Active Directory
Active Directory is the LDAP-compliant directory server included with Windows server operating systems. Active Directory stores all Windows operating system information, including users, groups, and policies. Active Directory also stores information about network resources (such as databases) and makes this information available to application users and network administrators. Active Directory enables users to access network resources with a single login. The scope of Active Directory can range from storing all the resources of a small computer network to storing all the resources of several wide areas networks (WANs).
About Accessing Active Directory
When using Oracle features that support Active Directory, ensure that the Active Directory computer can be successfully reached using all possible TCP/IP host name forms to reach the domain controller. For example, if the host name of the domain controller is server1 in the domain example.com, then ensure that you can ping that computer using all of the following:
-
server1.example.com -
example.com -
server1
Active Directory often issues referrals back to itself in one or more of these forms, depending upon the operation being performed. If any of the forms cannot reach the Active Directory computer, then some LDAP operations may fail.
Overview of Oracle Components That Integrate with Active Directory
The following Oracle Database features support or have been specifically designed to integrate with Active Directory:
About Directory Naming
Oracle Database provides Oracle Net Services directory naming, which makes use of a directory server. This feature has been enabled to work with Microsoft Active Directory. Directory Naming enables clients to connect to the database making use of information stored centrally in an LDAP-compliant directory server such as Active Directory. For example, any net service name previously stored in the tnsnames.ora file can now be stored in Active Directory.
About Automatic Discovery of Directory Servers
Oracle Net Configuration Assistant provides automatic discovery of directory servers. When you select Active Directory as the directory server type, Oracle Net Configuration Assistant automatically discovers the directory server location and performs related tasks.
See Also:
"Configuring Client Computers and Oracle Database to Use Active Directory" for more information about Active Directory configurationAbout Integration with Windows Tools
Oracle Database services, net service names, and enterprise role entries in Active Directory can be displayed and tested in two Windows tools:
-
Windows Explorer
-
Active Directory Users and Computers
Windows Explorer displays the hierarchical structure of files, directories, and local and network drives on your computer. It can display and test Oracle Database service and net service name objects.
Active Directory Users and Computers is an administrative tool installed on Windows servers configured as domain controllers. This tool enables you to add, modify, delete, and organize Windows accounts and groups, and publish resources in the directory of your organization. Like Windows Explorer, it can display and test Oracle Database service and net service name objects. Additionally, it can manage access control.
About User Interface Extensions for Oracle Net Directory Naming
The property menus of Oracle Database service and net service name objects in Windows Explorer and Active Directory Users and Computers have been enhanced. When you right-click these Oracle directory objects, you now see two new options for testing connectivity:
-
Test
-
Connect with SQL*Plus
The Test option tests whether the user name, password, and net service name you initially entered can actually connect to Oracle Database. The Connect with SQL*Plus option starts SQL*Plus, which enables you to perform database administration, run scripts, and so on.
About Enhancement of Directory Object Type Descriptions
Oracle directory object type descriptions in Active Directory have been enhanced to make them easier to understand. In the right pane of Figure 14-1, for example, the Type column reveals that sales is an Oracle Net Service name.
About Integration with Windows Login Credentials
Oracle database and configuration tools can use the login credentials of the Windows user currently logged on to connect to Active Directory without having to re-enter the login credentials. This feature has the following benefits:
-
Oracle clients and databases can securely connect to Active Directory and retrieve the net service name.
-
Oracle configuration tools can connect automatically to Active Directory and configure Oracle Database and net service name objects. The enabled tools include Oracle Net Configuration Assistant and Database Configuration Assistant.
-
Oracle clients can make secure access over the internet to avoid anonymous binds to the directory. The enhanced security enables the sites to restrict access to Database Service by setting access control (ACL) on Database Service DN in Directory Server. The enhancement gives clients the option to use authenticated binds for LDAP name lookup. Clients will have access to Database Service object if the object (DN of Database Service Entry) has been configured with restrictive access control.
Configuration on machines that require authenticated name lookups
Add the following entry in sqlnet.ora to enable authenticated name lookup:
names.ldap_authenticate_bind = TRUE
Overview of Oracle Directory Objects in Active Directory
If Oracle Database and Oracle Net Services are installed and configured to access Active Directory, then Active Directory Users and Computers displays Oracle directory objects, as illustrated in Figure 14-1:
Figure 14-1 Oracle Directory Objects in Active Directory Users and Computers
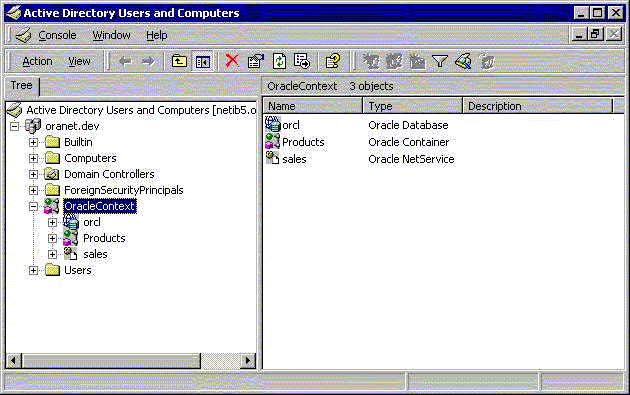
Description of "Figure 14-1 Oracle Directory Objects in Active Directory Users and Computers"
Table 14-1 describes the Oracle directory objects appearing in Figure 14-1.
Table 14-1 Oracle Directory Objects
| Object | Description |
|---|---|
|
|
The domain in which you created your Oracle Context. This domain (also known as the administrative context) contains various Oracle entries to support directory naming. Oracle Net Configuration Assistant automatically discovers this information during Oracle Database integration with Active Directory. |
|
|
The top-level Oracle entry in the Active Directory tree. It contains Oracle Database service and net service name object information. All Oracle software information is placed in this folder. |
|
|
The Oracle Database service name used in this example. |
|
|
Folder for Oracle product information. |
|
|
The net service name object used in this example. |
|
|
Folder for the Oracle security groups. See "Overview of Access Control List Management for Oracle Directory Objects" for more information. Enterprise users and roles created with Oracle Enterprise Security Manager also appear in this folder. |
Overview of Requirements for Using Oracle Database with Active Directory
To use Net Directory Naming with Active Directory, you must have supported Windows operating system and Oracle software releases, and you must create Oracle schema objects and an Oracle Context. These requirements are discussed in the following sections:
Note:
-
The Oracle schema objects and Oracle Context can both be created by running Oracle Net Configuration Assistant.
-
Regardless of the Oracle Database Client and Oracle Database releases you are using, you must be running in a Windows Server domain to integrate Net Directory Naming with Active Directory.
Creating Oracle Schema Objects
You must create Oracle schema objects to use net directory naming features with Active Directory. Schema objects are sets of rules for Oracle Net Services and Oracle Database entries and their attributes stored in Active Directory. The following restrictions apply to creating Oracle schema objects to use with Active Directory:
-
Only one Oracle schema object can be created for each forest.
-
The Windows server domain controller must be the operations master that allows schema updates. See your operating system documentation for instructions.
To create an Oracle schema object:
-
Log in as a member of Schema Administrator group or as a member who has rights to update the schema into schema master domain. The logged in client computer must be a part of the schema master domain. Schema master domain administrators are schema administrators by default.
-
Use Oracle Net Configuration Assistant to create the Oracle schema object. You can create your schema object during or after database installation.
If the Active Directory display is not configured to accept all 24 default languages, then Oracle schema object creation can fail while Oracle Net Configuration Assistant is configuring Active Directory as the directory server. Before running Oracle Net Configuration Assistant to complete directory access configuration, verify that the display specifiers for all 24 languages are populated by entering the following at the command prompt:
ldifde -p OneLevel -d cn=DisplaySpecifiers,cn=Configuration,domain context -f temp file
For this command, note the following:
-
domaincontextis the domain context for this Active Directory server.For example,
dc=example,dc=com. -
tempfileis a file where you want to put the output.
If the command reports that fewer than 24 entries were found, then you can still use Oracle Net Configuration Assistant. However, the report will indicate that Oracle schema object creation failed, rather than simply reporting that display specifiers for some languages were not created.
When the Oracle Net Configuration Assistant report shows failure due to less than 24 entries found, create display specifiers manually.
Creating Display Specifiers Manually
When Oracle Net Configuration Assistant creates the Oracle schema object in Active Directory, the display specifiers for Oracle entries are not created. This means you cannot view Oracle database entries in Active Directory interfaces.
You can manually add these entries into Active Directory after the Oracle schema object has been created by doing the following, using the same Windows user identification you used when creating the Oracle schema object with Net Configuration Assistant:
-
Open a command shell.
-
Change directory to
ORACLE_HOME\ldap\schema\ad. -
Copy
adDisplaySpecifiers_us.sbstoadDisplaySpecifiers_us.ldif. -
Copy
adDisplaySpecifiers_other.sbstoadDisplaySpecifiers_other.ldif. -
Edit each of these
.ldiffiles, replacing all occurrences of%s_AdDomainDN%with the domain DN for the specific Active Directory into which you want to load the display specifiers (for example,dc=example,dc=com). -
Run the following commands:
ldapmodify -h ad hostname -Z -f adDisplaySpecifiers_us.ldif ldapmodify -h ad hostname -Z -f adDisplaySpecifiers_other.ldif
where
ad hostnameis the host name of the Active Directory domain controller to which you want to load the display specifiers.
Creating an OracleContext
You must create an Oracle Context to use net directory naming features with Active Directory. Oracle Context is the top-level Oracle entry in the Active Directory tree. It contains Oracle Database service and Oracle Net service name object information.
-
You can create only one Oracle Context for each Windows server domain (administrative context).
-
You must have the right to create domain and enterprise objects to create the Oracle Context in Active Directory with Oracle Net Configuration Assistant.
-
Use Oracle Net Configuration Assistant to create your Oracle Context. You can create the Oracle Context during or after Oracle Database Custom installation.
See Also:
-
Oracle Database Installation Guide for Microsoft Windows for installation procedures
-
Oracle Database Net Services Administrator's Guide for configuration procedures
Running Oracle Network Configuration Assistant
Oracle Net Configuration Assistant is a graphical, wizard-based tool used to configure and manage Oracle Network configurations.
To start Oracle Net Configuration Assistant:
-
Click Start, then click All Programs.
-
Click Oracle - HOMENAME, Configuration and Migration Tools, then Net Configuration Assistant.
-
Select the Directory Usage Configuration option, then click Next.
-
Select Directory Type Microsoft Active Directory, then click Next.
Note:
The Microsoft Active Directory configuration option is only available in the Windows version of Oracle Net Configuration Assistant. -
Select the option to configure the directory server for Oracle usage and to create or upgrade the Oracle Schema and Context, then click Next.
-
Enter the Active Directory host name, then click Next.
-
Select the option to upgrade the Oracle Schema, then click Next.
The next page should denote successful Directory configuration.
Directory usage configuration complete! The distinguished name of your default Oracle Context is: cn=OracleContext,DC=home,DC=com
-
Click Next, then click Finish.
-
The earlier message may only denote partial success:
The Assistant is unable to create or upgrade the Oracle Schema for the following reason: ConfigException: Oracle Schema creation was successful, but Active Directory Display Specifier creation failed.oracle.net.config.ConfigException; TNS-04420: Problem running LDAPMODIFY
Click OK, then click Finish.
-
If you receive the preceding error, disregard the message and re-run Oracle Net Configuration Assistant using the originally supplied values.
The wizard should complete denoting successful Directory configuration:
Directory usage configuration complete! The distinguished name of your default Oracle Context is: cn=OracleContext,DC=home,DC=com
Click Next, then click Finish.
About Directory Naming Software Requirements
Directory naming method maps connect identifiers to connect descriptors contained in Microsoft Active Directory server. A directory server provides central administration of database services and net service names, making it easier to add or relocate services.
Use Oracle Enterprise Manager or Oracle Net Manager to create net service names. To use Microsoft Active Directory naming method, the Oracle Database Client must run on supported Windows operating systems. While you must have Oracle Database that is required for registering the database service as an object in Active Directory. The database server can run on any of the supported operating system, not necessarily Windows operating system.
By default, directory naming adaptor connects anonymously to active directory. Authenticated naming method requires client computer to be a part of the active directory domain to resolve a database service or net service name to a connect descriptor stored in a central directory server of its domain.
NAMES.LDAP_AUTHENTICATE_BIND=true parameter in sqlnet.ora file enables authenticated naming method.
See Also:
"Configuring the Directory Naming Method" in Oracle Database Net Services Administrator's Guide for more informationConfiguring Client Computers and Oracle Database to Use Active Directory
Oracle Net Configuration Assistant enables you to configure client computers and Oracle Database to access a directory server. When you choose directory access configuration from Oracle Net Configuration Assistant, it then prompts you to specify a directory server type to use. When you select Active Directory as the directory server type, the Automatic Discovery of Directory Servers feature of Oracle Net Configuration Assistant automatically:
-
Discovers the Active Directory server location
-
Configures access to the Active Directory server
-
Creates the Oracle context (also known as your domain)
Note:
Oracle Net Configuration Assistant does not configureDIRECTORY_SERVERS parameter in ldap.ora, in which case, clients automatically discover the Active Directory server for Net Naming.If the Active Directory server already has an Oracle Context, then select the following nondefault option:
Select the directory server you want to use, and configure the directory server for Oracle usage. (Create or upgrade Oracle schema objects and Oracle Context as necessary.)
Oracle Net Configuration Assistant will report that the Oracle Context does not exist. Ignore this and choose to create the Oracle Context anyway. Directory access configuration will complete without trying to re-create the existing Oracle Context.
Note:
Regardless of the Oracle Database Client and Oracle Database releases you are using, you must be running in a Windows Server domain to take advantage of the automatic directory server discovery features of Oracle Net Configuration Assistant. Oracle Net Configuration Assistant does not automatically discover your directory server, and instead prompts you for additional information, such as the Active Directory location.See Also:
-
"Creating Oracle Schema Objects" for information about possible failures during configuration
-
"Overview of Requirements for Using Oracle Database with Active Directory"
-
Oracle Database Net Services Administrator's Guide for configuration procedures
About Testing Connectivity
This section describes how to connect to an Oracle Database server through Active Directory.
This section contains these topics:
Testing Connectivity from Client Computers
When using Oracle Net directory naming, client computers connect to a database by specifying the database or net service name entry that appears in the Oracle Context. For example, if the database entry under the Oracle Context in Active Directory is orcl, and the client and the database are in the same domain, then a user connects to the database through SQL*Plus by entering the following connect string:
SQL> CONNECT username@orcl Enter password: password
If the client and the database are in different domains, then a user connects to the database through SQL*Plus by entering:
SQL> CONNECT username@orcl.domain Enter password: password
where domain is the domain in which the Oracle Database server is located.
The LDAP naming adapter has an internal function which we call simplified naming, which will attempt to translate a DNS-style name into an x500 (LDAP) style name (DN) based on the naming convention used in ldap.ora:DEFAULT_ADMIN_CONTEXT.
It relies on ldap.ora:default_admin_context using either an org form or a domain component (dc) form. This cues the mechanism to use either of the following conventions to convert the domain name to an x500 DN:
-
'dc=, dc='
-
'ou=, o='
-
'ou=, o=, c='
For example,
SQL> CONNECT SMITH@hr.example.com
Enter password: password
The following values for default_admin_context will result in the associated DN:
DEFAULT_ADMIN_CONTEXT="o=stdev"
The resulting DN is
cn=HR,cn=OracleContext,ou=EXAMPLE,o=COM DEFAULT_ADMIN_CONTEXT="dc=oracle, dc=com"
The resulting DN is
cn=HR,cn=OracleContext,dc=EXAMPLE,dc=COM DEFAULT_ADMIN_CONTEXT="o=oracle,c=us"
The resulting DN is
cn=HR,cn=OracleContext,o=EXAMPLE,c=COM
Note:
The value of thedefault_admin_context is not used literally, since the queried-name is given in a fully qualified form. The default_admin_context determines which style DN is produced, or which left-hand-side to use when converting each domain in the given DN component.DNS-style conventions enable client users to access an Oracle Database server through a directory server by entering minimal connection information, even when the client computer and Oracle Database server are in separate domains. Names following the X.500 convention are longer, especially when the client and Oracle Database server are located in different domains (also known as administrative contexts).
See Also:
-
"Configuration Management Concepts" in Oracle Database Net Services Administrator's Guide for more information about X.500 naming conventions
-
"Minimum Requirements for Passwords" in Oracle Database Installation Guide for Microsoft Windows
Testing Connectivity from Microsoft Tools
Oracle directory objects in Active Directory are integrated with two Microsoft tools:
-
Windows Explorer
-
Active Directory Users and Computers
You can test connectivity to an Oracle Database server from within these Microsoft tools by connecting to it, or you can just test the connection with actually connecting. To test connectivity:
-
Start Windows Explorer or Active Directory Users and Computers.
To start Windows Explorer:
-
From the Start menu, select All Programs, then select Accessories, and then select Windows Explorer.
-
Expand Network.
-
Expand Directory.
To start Active Directory Users and Computers:
From the Start menu, select All Programs, then select Administrative Tools, and then select Active Directory Users and Computers.
Note:
All clients accessing an Oracle Database server through Active Directory require read access on all net service name objects in the Oracle Context. If Oracle Net will not be configured to require authentication for name lookup, then clients must be able to authenticate anonymously with Active Directory. With Windows Server domain, this will require changing the Active Directory default setting so that anonymous access will be allowed. If anonymous access is not going to be allowed to this directory the clients must be configured to authenticate and net service objects must have access control definitions which allow clients to read them as appropriate.See also:
Oracle Database Net Services Administrator's Guide for more information -
-
Expand the domain in which your Oracle Context is located.
-
Expand your Oracle Context.
-
Right-click a database service or Oracle Net Service name object.
A menu appears with several options. This section covers only the Test and Connect with SQL*Plus options.
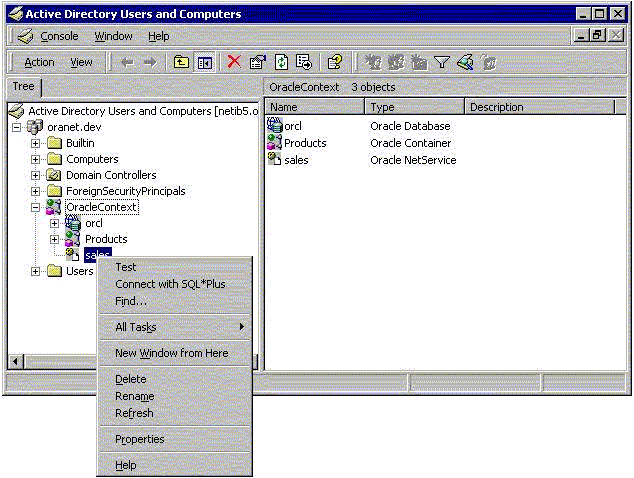
Description of the illustration adtest.gif
-
If you want to test the database connection without actually connecting to it, then choose Test. A status message appears describing the status of your connection attempt.
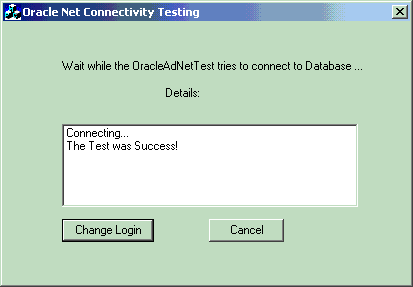
Description of the illustration adtstcon.gif
-
If you want to test the database connection by actually connecting to it, then choose Connect with SQL*Plus. The Oracle SQL*Plus Logon dialog appears.
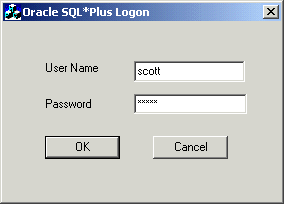
Description of the illustration adsqlpls.gif
-
Enter your user name and password, then click OK. A status message appears describing the status of your connection attempt.
Overview of Access Control List Management for Oracle Directory Objects
This section identifies security groups specific to Oracle directory objects within Active Directory and explains how to add and delete security group members.
This section contains these topics:
Overview of Security Groups
Security groups are automatically created when the Oracle Context is created in Active Directory. The user configuring access (and thus creating the Oracle Context) is automatically added to each group. Following are a list of relevant groups:
About OracleDBCreators
The OracleDBCreators group is for the person registering the Oracle Database server. The domain administrator is automatically a member of this group. Users in this group can:
-
Create new Oracle Database objects in the Oracle Context.
-
Modify the Oracle Database objects that they create.
-
Read, but not modify, the membership for this group.
About OracleNetAdmins
Users in the OracleNetAdmins group can:
-
Create, modify, and read Oracle Net Services objects and attributes.
-
Read the group membership of this group.
About Oracle Net Services Objects
In Oracle Database Client 11g or later, directory clients may optionally be configured to authenticate with the directory while resolving DB names to connect strings. This makes it possible for Oracle Net Services objects to be protected using ACLs.
There are many ways in which the identities of users may be defined in the directory, and how those users or certain groups of users may be given access to some or all Net Services. Oracle Database supplies no predefined groups, and has no procedures in the config tools for defining read-access restrictions on this data, so administrators must use standard object management tools from their directory system to manually create any necessary groups and ACLs. Existing identity structures may be referred to by Net Service ACLs.
Because the access definitions for objects are complex and may involve security properties which are inherited from parent nodes in the Directory Information Tree (DIT), Oracle recommends that the administrators should refer to the relevant tools and documentation for the directory system they are using, and formulate or integrate access management for Oracle Net Services objects into a directory-wide policy and security implementation.
Note:
Pre-11g clients can only bind to the directory as anonymous, so any ACL protection on Net Services will disable older clients. Access Control can only be implemented if all clients requiring access to these objects are 11g or later.Setting ACLs on Net Service Entries
Use the Dsacls tool to set ACLs on Directory Object.
The Dsacls.exe command-line displays and changes permissions (access control entries) in the Access Control List (ACL) of objects in Active Directory. This command-line tool will be included in Support Tools on the product media.
Examples:
To enable an anonymous generic read on the orcl service, run the following command:
dsacls "CN=orcl,CN=OracleContext,OU=Example,O=Com" /G "anonymous logon":GR
To enable a generic read on the orcl service for the user smith in EXAMPLE domain, run the following command:
dsacls "CN=orcl,CN=OracleContext,OU=Example,O=Com" /G example\smith:GR
To disable an anonymous generic read on the orcl service, run the following command:
dsacls "CN=orcl,CN=OracleContext,OU=Example,O=Com" /R "anonymous logon"
To disable a generic read on the orcl service for the user smith in EXAMPLE domain, run the following command:
dsacls "CN=orcl,CN=OracleContext,OU=Example,O=com" /R example\smith
See Also:
http://support.microsoft.com/kb/281146 for complete description of the Dsacls.exe command-line tool.Adding and Deleting Security Group Members
You can add or remove users in the security groups with Active Directory Users and Computers.
Note:
Use Active Directory Users and Computers to perform the procedures described in this section. Windows Explorer does not provide the necessary functionality.To add or remove users:
-
From the Start menu, select All Programs, then select Administrative Tools, and then select Active Directory Users and Computers.
-
Choose Advanced Features from the View main menu.
This enables you to view and edit information that is usually hidden.
-
Expand the domain (administrative context) in which your Oracle Context is located.
-
Expand Users.
The security groups appear in the right window pane.
Description of the illustration adsecgrp.gif
-
Right-click the Oracle security group that you want to view or modify.
A menu appears with several options.
-
Choose Properties.
-
Choose the Members tab.
The Properties dialog for the group you selected appears (in this example,
OracleDBCreators).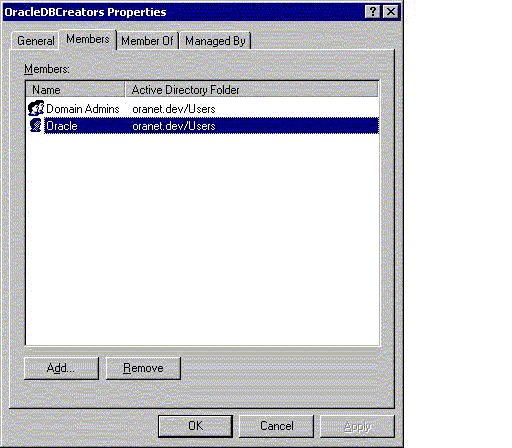
Description of the illustration admembrs.gif
-
To add users, click Add.
The Select Users, Computers, Service Accounts, or Groups dialog appears.
-
Select the users or groups you want to add and click Add.
Your selections appear in the Select Users, Computers, Service Accounts, or Groups dialog.
-
To remove a user, select the user name from the Members list and click Remove.
-
When you are finished adding and removing users, click OK.