| Oracle® Enterprise Manager Application Configuration Console PCI Compliance Release 5.3.2 Part Number E14654-02 |
|
|
PDF · Mobi · ePub |
| Oracle® Enterprise Manager Application Configuration Console PCI Compliance Release 5.3.2 Part Number E14654-02 |
|
|
PDF · Mobi · ePub |
This chapter describes how to perform and reconcile compliance audits, and how to set up tracking to ensure continued compliance.
To check for PCI compliance, you run audits on the assets that were created based on the supplied resource specifications. The purpose of an audit is to determine the degree of compliance of your computing systems vis-a-vis the standards set forth by the Security Standards Council. There are two ways to run audits:
In the Navigator view, on a single asset
In Web Reports, on a collection of assets
The first is a method of expedience. It's a convenient way to take a pulse on a particular asset; that is, to get a sense of how close to compliance the configuration is.
Web Reports is the preferred method for a variety of reasons. You can report on multiple assets. It presents the information in a visually pleasing format. You can schedule the audit to run automatically on a recurring basis. You can distribute the output in a variety of formats.
To run an audit on a PCI asset in the Navigator view:
Right-click the asset you want to audit and select PCI Auditing > Audit Asset. The PCI icon denotes assets that are auditable.
In the confirmation dialog that opens, click OK to run the job. Click Advanced Settings if you want to enter a comment or schedule job execution for a later time.
The audit job appears in the Jobs view (lower right portion of the Client window). You may have to click the Jobs tab to display the view.
When Completion Status says audit complete, right-click anywhere in the line and select Show Details.
The Output log denotes success or failure of the audit, and describes the findings as to missing properties and unmatched property values. This record of the audit is available in the Scripting Jobs view until purged as part of regular housekeeping, or deleted by the owner.
Web Reports is Application Configuration Console's browser-based reporting tool. (A URL to access Web Reports is installed on a Windows host as part of Client installation.) You can access Web Reports from a shortcut on the Client Start menu.
To run an audit on PCI assets in Web Reports:
Start up Web Reports. You can use the Client Start menu shortcut or point your browser at the following URL:
https://mVserverHost:9943/mvwebreports/index.jsp
On the Audit menu, select PCI Compliance.
Select a Source in the report criteria column on the left. The source can be any combination of projects or other containers, or of selected assets. Only assets denoted by the PCI icon are auditable.
Click Generate Report.
After a moment, the results of the audit appear in the reporting page.
Notice the legend at the bottom of the last page of a report. The implications are as follows:
Passed–an asset and its configurations are in compliance with the properties and values in the auditing dictionary.
Failed–some or all of an asset's configurations are not in compliance, either because properties in the dictionary are missing from the configuration or there are discrepancies in configuration and dictionary property values.
Skipped–an asset's configuration was not audited because there is no referenced auditing dictionary; an asset that has a mix of passed and skipped configurations is considered to be in compliance.
The report lists configurations within assets that are arranged alphabetically. The last update refers to when external data was last written to Application Configuration Console. This can reflect the initial asset load, a manual update performed within Application Configuration Console, or the result of a tracking event with auto-update. Actual value is the property value in the asset configuration; expected value derives from the auditing dictionary. Path identifies the origin of the property in the external resource. This is useful for resolving like-named properties.
You should have no reasonable expectation that your environment is in compliance when you first audit your PCI assets. The task faced by your security experts is to evaluate the results and draw up a plan of redress. When is it prudent to follow the council's recommendations and when is there an acceptable risk to deviate from those recommendations. Obviously this will be an evolving process, but the clearly defined objective is to eventually establish a baseline at which your operating system security settings reflect your desired level of compliance.
If your security team decides to follow the recommendations to the letter, then the process is straightforward: change your configurations at their source to match the properties and values in the dictionaries.
More likely, though, your team will choose to override or ignore any number of property values in various configurations. Oracle feels that best practice in this case is to preserve the installed environment by making modifications to copies of product dictionaries. In brief, these are the steps you would take:
In Application Configuration Console, export the auditing dictionary whose settings you want to customize.
Edit the XML file by changing the dictionary name and the definition URI of each property. Rename the file when you save it.
Import into Application Configuration Console the renamed version of the auditing dictionary.
Open the imported dictionary in the Application Configuration Console Editor area. Delete the properties you want to ignore, and otherwise change property values to the settings you want to validate against.
In the associated resource specification, edit the command resource definition metadata to reference the imported auditing dictionary.
Add a new asset, based on the revised resource specification and dictionary.
Perform an audit on the asset to ensure compliance under the revised standards.
Step 1: Export the Auditing Dictionary
In the Property Dictionaries folder in the Navigator view, right-click the dictionary you want to customize and select Export.
Select a Host/Endpoint and Authentication Pack where you can write the XML file.
Click Browse to indicate the directory location where you want to write the file.
Click OK to complete the export operation.
Step 2: Change the Dictionary Name
Edit the exported XML file to change the dictionary name and URI dictionary references:
In an XML or a text editor, open the exported dictionary XML file.
Change the dictionary name to your custom name in the mvDictionary name tag and in the URI value immediately following.
Change the dictionary name as specified in the URI value in each definition tag that appears in the file. Effectively, there is a tag for each property name value pair.
Save the file in XML format as the same name of your custom dictionary.
The graphic below illustrates which values (circled in green) to edit:
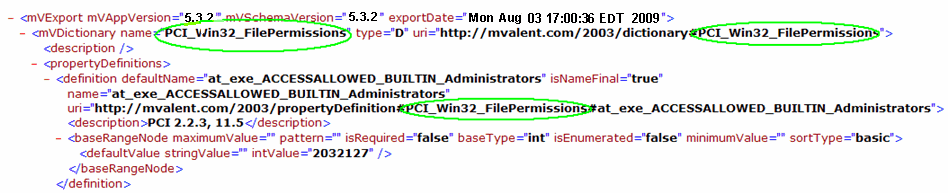
Step 3: Import the Edited Auditing Dictionary
Right-click the Property Dictionaries folder in the Navigator view and select Import.
Select the same Host/Endpoint and Authentication Pack where you exported the auditing dictionary.
Click Browse to indicate the directory location where you wrote the XML file.
Click OK to complete the import operation.
Step 4: Edit the Properties in the Custom Dictionary
Customize the contents of your dictionary:
In the Property Dictionaries folder in the Navigator view, right-click the custom dictionary you imported and select Open.
In the Editor area, click the Edit button.
In the Name column, select those properties you want to remove. Use Ctrl-Click and Shift-Click to select multiple properties.
Click Delete to remove the selected properties.
Edit individual property values by selecting the property in the Name column and changing the Default Value for the property on the right.
Click Save to complete customization of your dictionary.
Note that if you want add new properties to your custom dictionary, as opposed to deleting or changing them, you can do this as well in the Editor area.
Step 5: Edit the Resource Specification Command Definition Metadata
Change the command resource specification to reference the correct dictionary:
In the Navigator view under the Resource Specifications folder, open the PCI_AUDIT_AUTOMATION_MODULE folder.
Right-click the appropriate resource specification and select Open.
In the Editor area, click the Edit button.
Select the row in the Command Definitions section and double-click the value in the Metadata column.
In the Edit Metadata dialog, click in the dictionary name row. This populates the name and value edit boxes.
Change the Value to the custom dictionary name.
Click Apply to confirm the change; click OK to close the dialog.
Click Save to complete the operation.
Add new assets based on the revised resource specification and dictionary. See Chapter 3 for information on loading assets.
Audit the new assets you loaded. See Section 4.1, "The Audit Process," at the beginning of this chapter.
The property name value pairs in an auditing dictionary drive the auditing process. Metadata on the configuration controls which dictionary to use to perform auditing. The configuration dictionary metadata derives from the value of the AUDIT_PROPERTY_DICTIONARY_NAME metadata set in the resource specification command definition. Table 4-1 breaks down the various options with respect to working with dictionaries.
Table 4-1 Product Dictionary Options
| Option | Action |
|---|---|
|
Use a custom dictionary to create PCI assets |
Change the dictionary metadata in the resource specification command definition to the name of the custom dictionary |
|
Use a custom dictionary to perform an audit of the asset |
Change the dictionary metadata in the asset configuration to the name of the custom dictionary |
|
Create PCI assets that ignore certain configurations |
Remove or rename the dictionary metadata in the resource specification command definition |
|
Perform an audit of an asset that ignores certain configurations |
Remove or rename the dictionary metadata in the asset configuration |
Step 5 under "Reconciling an Audit" describes where and how to edit dictionary metadata in a resource specification command definition. The other option referenced in Table 4-1 is to edit dictionary metadata in the asset configuration. Here's how:
In the Navigator view, expand the PCI container to expose the appropriate asset view (Resource View, by default).
Open the asset configuration whose auditing dictionary you want to edit.
In the Editor area, click the Metadata tab, then click the Edit button.
Under User defined, look for AUDIT_PROPERTY_DICTIONARY_NAME. Edit the value as appropriate.
Click Save to complete the operation.
Note:
When you rename a dictionary, due diligence dictates that you investigate any configuration flagged as skipped in the audit report, to ensure dictionary names are correct. For example, a typo in the metadata name would cause the configuration to be skipped.The winnowing process should eventually yield a set of assets that the security team deems compliant. This is the baseline against which to track for changes that might indicate a security risk or breach.
A likely scenario takes the following approach:
All PCI assets are organized as part of a single project
Tracking on PCI assets occurs daily; alerts are e-mailed to the security team
The PCI audit report runs weekly; the generated report is e-mailed to the security team
Security team meets as necessary to reconcile detected differences
You schedule tracking on asset views. The default is the Resource View.
Expand the PCI project in the Navigator view to expose the PCI asset views.
Right-click an asset view and select Open.
In the Editor area, click the Tracking Schedule tab at the bottom.
Click the Edit button and enable tracking for assets.
Select all configurations in the asset view.
Select all configurations in the asset view.
Enter the e-mail address of the security team.
For the Update option, select Replace.
Click Save to complete the scheduling operation.
Note:
The Replace update option causes the Application Configuration Console data to be overwritten with the external configuration data whenever tracking detects a difference. In other words, the operating system files are assumed to be correct unless the security team overrules this assumption.The security team can decide the frequency of PCI auditing. Running the PCI Audit report once a week might be a reasonable starting point. Remember that it can be scheduled to run automatically during off-peak hours.
To schedule the PCI Audit report:
Start Web Reports in your browser.
On the Audit menu, select PCI Compliance.
In the report criteria column, select the project containing the PCI assets to audit as the Source.
Click the Schedule Report button.
Fill in the dialog with appropriate scheduling information.
For example, you might schedule auditing to be performed on all PCI assets within the selected project at midnight every Sunday, with the resulting report to be e-mailed in PDF format to all members of the security team for their review.
Click OK to schedule the report.