Enterprise User Security Configuration Overview
Configuring Enterprise User Security means creating shared schemas and global roles in databases that you want accessible to enterprise users. You configure the identity management realm in the directory to reflect those database roles and schemas, and then associate directory users with them. These steps apply regardless of the authentication method you choose: password, Kerberos, or SSL.
The primary configuration differences among the authentication types are in network connection configuration. You must consider the following three connection types:
-
Client-to-database
-
Database-to-directory
-
Database-to-database (current user database links can be secured by SSL only)
Enterprise User Security supports many combinations of authentication types between databases, directories, and clients. The three most common implementations of Enterprise User Security, described in this chapter, use the following authentication methods for client-database and database-directory connections:
-
Passwords for both connections
-
SSL for both connections
-
Kerberos for client-database connections and passwords for database-directory connections
You decide which of these to choose based primarily on your network environment, because the security and integrity of your enterprise data depend on creating secure network connections. Typical network environments can have all clients, databases, and directories residing within the same network behind a firewall, or distributed across several networks and perhaps exposed to the Internet. Different environments can dictate what authentication types you choose, in order to secure your Enterprise User Security network connections.
A second consideration in making such choices is the fact that more rigorous authentication types, such as SSL and Kerberos, require greater configuration complexity, additional software, and ongoing maintenance.
Figure 4-1 shows the configuration process for Enterprise User Security. It is a step-by-step process with decision points based on your implementation and how your users are authenticated. The configuration steps represented with broken lines are optional.
Figure 4-1 Enterprise User Security Configuration Flow Chart
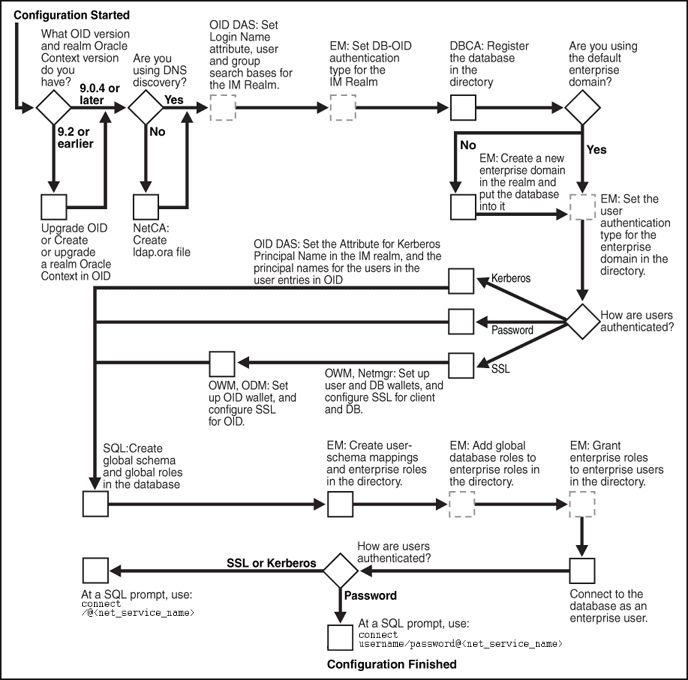
Description of "Figure 4-1 Enterprise User Security Configuration Flow Chart"
For brevity, some product names and features have been abbreviated in this flow chart. The following table lists the abbreviations used and the meaning of each:
| Abbreviation | Meaning |
|---|---|
|
DBCA |
Database Configuration Assistant |
|
EM |
Oracle Enterprise Manager |
|
IM Realm |
Identity Management Realm |
|
Netmgr |
Oracle Net Manager |
|
ODM |
Oracle Directory Manager |
|
OID |
Oracle Internet Directory |
|
OID DAS |
Oracle Internet Directory Delegated Administration Services |
|
OWM |
Oracle Wallet Manager |
|
SQL |
SQL*Plus |
See Also:
Introducing Enterprise User Security for information about the realm Oracle Context, its administrative groups, and entries that pertain to Enterprise User Security