22 Configuring Audit Policies
You can configure unified auditing by creating custom unified audit policies, using predefined unified auditing policies, or using fine-grained auditing.
Topics:
-
Auditing Activities with Unified Audit Policies and the AUDIT Statement
-
Auditing Activities with the Predefined Unified Audit Policies
Selecting an Auditing Type
You must perform a specific set of steps depending on the type of auditing that you want to perform: general activities (such as SQL statement actions), commonly used auditing activities, or fine-grained auditing.
In addition to these types of auditing, remember that Oracle Database mandatorily audits some activities. See "Activities That Are Mandatorily Audited" for more information.
Topics:
Auditing SQL Statements, Privileges, and Other General Activities
You can audit SQL statements, privileges, schema objects, functions, procedures, packages, triggers, and application context value activity. You can add conditions to the unified audit policy, as well as audit behavior from other Oracle Database components, such as Oracle Database Real Application Security. However, if you want to audit specific columns or use event handlers, use fine-grained auditing.
The general steps for performing this type of auditing are as follows:
-
In most cases, use the
CREATE AUDIT POLICYstatement to create an audit policy. If you must audit application context values, then use theAUDITstatement.See the relevant categories under "Auditing Activities with Unified Audit Policies and the AUDIT Statement".
-
If you are creating an audit policy, then use the
AUDITstatement to enable it and optionally apply (or exclude) the audit settings to one or more users, including administrative users who log in with theSYSDBAadministrative privilege (for example, theSYSuser).AUDITalso enables you to create an audit record upon an action's success, failure, or both.See "Enabling and Applying Unified Audit Policies to Users".
-
Query the
UNIFIED_AUDIT_TRAILview to find the generated audit records.See also "Audit Policy Data Dictionary Views" for additional views.
-
Periodically archive and purge the contents of the audit trail.
Auditing Commonly Used Security-Relevant Activities
Oracle Database provides a set default unified audit policies that you can choose from for commonly used security-relevant audits.
The general steps for performing this type of auditing are as follows:
-
See "Auditing Activities with the Predefined Unified Audit Policies" to learn about the default audit policies.
-
Use the
AUDITstatement enable the policy and optionally apply (or exclude) the audit settings to one or more users.See "Enabling and Applying Unified Audit Policies to Users".
-
Query the
UNIFIED_AUDIT_TRAILview to find the generated audit records.See also "Audit Policy Data Dictionary Views" for additional views.
-
Periodically archive and purge the contents of the audit trail.
Auditing Specific, Fine-Grained Activities
Use fine-grained auditing if you want to audit individual columns and use event handlers. This type of auditing provides all the features available in unified audit policies.
The general steps for performing this type of auditing are as follows:
-
See "Auditing Specific Activities with Fine-Grained Auditing" to understand more about auditing specific activities.
-
Use the
DBMS_FGAPL/SQL package to configure fine-grained auditing policies. See "Using the DBMS_FGA PL/SQL Package to Manage Fine-Grained Audit Policies". -
Query the
UNIFIED_AUDIT_TRAILview to find the generated audit records.See also "Audit Policy Data Dictionary Views" for additional views.
-
Periodically archive and purge the contents of the audit trail.
Auditing Activities with Unified Audit Policies and the AUDIT Statement
You can use the CREATE AUDIT POLICY and AUDIT statements to use unified auditing policies.
Topics:
-
About Auditing Activities with Unified Audit Policies and the AUDIT Statement
-
Auditing SELECT and the READ ANY TABLE or SELECT ANY TABLE Privilege
-
How Auditing Works for SQL Statements and Privileges in a Multitier Environment
-
Using the Unified Audit Policies or AUDIT Settings in a Multitenant Environment
See Also:
"Auditing SQL Statements, Privileges, and Other General Activities" for general steps for performing this type of auditingAbout Auditing Activities with Unified Audit Policies and the AUDIT Statement
You can audit the several types of activities.
-
User accounts (including administrative users who log in with the
SYSDBAadministrative privilege), roles, and privileges -
Object actions, such as dropping a table or a running a procedure
-
Application context values
-
Activities from Oracle Database Real Application Security, Oracle Recovery Manager, Oracle Data Mining, Oracle Data Pump, Oracle SQL*Loader direct path events, Oracle Database Vault, and Oracle Label Security
To accomplish this, depending on what you want to audit, use the following:
-
Unified audit policies. A unified audit policy is a named group of audit settings that enable you to audit a particular aspect of user behavior in the database. To create the policy, you use the
CREATE AUDIT POLICYstatement. The policy can be as simple as auditing the activities of a single user or you can create complex audit policies that use conditions. You can have more than one audit policy in effect at a time in a database. An audit policy can contain both system-wide and object-specific audit options. Most of the auditing that you will do for general activities (including standard auditing) requires the use of audit policies. -
AUDIT and NOAUDIT SQL statements. The
AUDITandNOAUDITSQL statements enable you to, respectively, enable and disable an audit policy. TheAUDITstatement also lets you include or exclude specific users for the policy. TheAUDITandNOAUDITstatements also enable you to audit application context values. -
For Oracle Recovery Manager, you do not create unified audit policies. The
UNIFIED_AUDIT_TRAILview automatically captures commonly audited Recovery Manager events.
Best Practices for Creating Unified Audit Policies
You can have multiple policies enabled at a time in the database, but ideally, limit the number of enabled policies.
The unified audit policy syntax is designed so that you can write one policy that covers all the audit settings that your database needs. A good practice is to group related options into a single policy instead of creating multiple small policies. This enables you to manage the policies much easier. As an example, the default audit policies described in "Auditing Activities with the Predefined Unified Audit Policies" each contain multiple audit settings within one unified audit policy.
Limiting the number of enabled audit policies for a user session has the following benefits:
-
It reduces the logon overhead that is associated with loading the audit policy's details into the session's UGA memory. If the enabled policy count is less, then less time is spent in loading the policy information.
-
It reduces the session's UGA memory consumption, because a fewer number of policies are required to be cached in UGA memory.
-
It makes the internal audit check functionality more efficient, which determines whether to generate an audit record for its associated event.
Syntax for Creating a Unified Audit Policy
To create a unified audit policy, you must use the CREATE AUDIT POLICY statement. When you create a unified audit policy, Oracle Database stores it in a first class object that is owned by the SYS schema, not in the schema of the user who created the policy.
Example 22-1 shows the syntax for the CREATE AUDIT POLICY statement.
Example 22-1 Syntax for the CREATE AUDIT POLICY Statement
CREATE AUDIT POLICY policy_name { {privilege_audit_clause [action_audit_clause ] [role_audit_clause ]} | { action_audit_clause [role_audit_clause ] } | { role_audit_clause } } [WHEN audit_condition EVALUATE PER {STATEMENT|SESSION|INSTANCE}] [CONTAINER = {CURRENT | ALL}];
In this specification:
-
privilege_audit_clausedescribes privilege-related audit options. See "Auditing System Privileges" for details. The detailed syntax for configuring privilege audit options is as follows:privilege_audit_clause := PRIVILEGES privilege1 [, privilege2]
-
action_audit_clauseandstandard_actionsdescribe object action-related audit options. See "Auditing Object Actions". The syntax is as follows:action_audit_clause := {standard_actions | component_actions} [, component_actions ] standard_actions := ACTIONS action1 [ ON {schema.obj_name | DIRECTORY directory_name | MINING MODEL schema.obj_name } ] [, action2 [ ON {schema.obj_name | DIRECTORY directory_name | MINING MODEL schema.obj_name } ]
-
component_actionsenables you to create an audit policy for Oracle Label Security, Oracle Database Real Application Security, Oracle Database Vault, Oracle Data Pump, or Oracle SQL*Loader. See the appropriate section under "Auditing Activities with Unified Audit Policies and the AUDIT Statement" for more information. The syntax is:component_actions := ACTIONS COMPONENT=[OLS|XS] action1 [,action2 ] | ACTIONS COMPONENT=DV DV_action ON DV_object_name | ACTIONS COMPONENT=DATAPUMP [ EXPORT | IMPORT | ALL ] | ACTIONS COMPONENT=DIRECT_LOAD [ LOAD | ALL ]
-
role_audit_clauseenables you to audit roles. See "Auditing Roles". The syntax is:role_audit_clause := ROLES role1 [, role2]
-
WHENaudit_conditionEVALUATE PERenables you to specify a function to create a condition for the audit policy and the evaluation frequency. You must include theEVALUATE PERclause with theWHENcondition. See "Creating a Condition for a Unified Audit Policy". The syntax is:WHEN 'audit_condition := function operation value_list' EVALUATE PER {STATEMENT|SESSION|INSTANCE}
-
CONTAINER, used for multitenant environments, enables you to create an audit policy as either a local audit policy (for the local pluggable database (PDB)) or as a common audit policy. See "Using the Unified Audit Policies or AUDIT Settings in a Multitenant Environment".
This syntax is designed to audit any of the components listed in the policy. For example, suppose you create the following policy:
CREATE AUDIT POLICY table_pol PRIVILEGES CREATE ANY TABLE, DROP ANY TABLE ROLES emp_admin, sales_admin;
The audit trail will capture SQL statements that require the CREATE ANY TABLE system privilege or the DROP ANY TABLE system privilege or any system privilege directly granted to the role emp_admin or any system privilege directly granted to the role sales_admin. (Be aware that it audits privileges that are directly granted, not privileges that are granted recursively through a role.)
After you create the policy, you must enable it by using the AUDIT statement. Optionally, you can apply the policy to one or more users, exclude one or more users from the policy, and designate whether an audit record is written when the audited action succeeds, fails, or both succeeds or fails. See "Enabling and Applying Unified Audit Policies to Users".
Auditing Roles
You can use the CREATE AUDIT POLICY statement to audit database roles.
Topics:
About Role Auditing
When you audit a role, Oracle Database audits all system privileges that are directly granted to the role. You can audit any role, including user-defined roles.
If you create a common unified audit policy for roles with the ROLES audit option, then you must specify only common roles in the role list. When such a policy is enabled, Oracle Database audits all system privileges that are commonly and directly granted to the common role. The system privileges that are locally granted to the common role will not be audited. To find if a role was commonly granted, query the DBA_ROLES data dictionary view. To find if the privileges granted to the role were commonly granted, query the ROLE_SYS_PRIVS view.
See Also:
Table 4-3, "Oracle Database Predefined Roles" for a list of predefined rolesConfiguring Role Unified Audit Policies
To create a unified audit policy to capture role use, you must include the ROLES clause in the CREATE AUDIT POLICY statement.
-
Use the following syntax to create a unified audit policy that audits roles:
CREATE AUDIT POLICY policy_name ROLES role1 [, role2];
For example:
CREATE AUDIT POLICY audit_roles_pol ROLES IMP_FULL_DATABASE, EXP_FULL_DATABASE;
You can build more complex role unified audit policies, such as those that include conditions. Remember that after you create the policy, you must use the AUDIT statement to enable it.
Example: Role Unified Audit Policy
Example 22-2 shows how to audit a predefined common role DBA in a multitenant environment.
Auditing System Privileges
You can use the CREATE AUDIT POLICY statement to audit system privileges.
Topics:
-
Configuring a Unified Audit Policy to Capture System Privilege Use
-
How System Privilege Unified Audit Policies Appear in the Audit Trail
About System Privilege Auditing
System privilege auditing audits activities that use a system privilege, such as READ ANY TABLE. In this kind of auditing, SQL statements that require the audited privilege to succeed are recorded.
A single unified audit policy can contain both privilege and action audit options. Do not audit the privilege use of administrative users such as SYS. Instead, audit their object actions. See "Auditing Object Actions" for more information.
Note:
You can audit system privileges, objects, database events, and so on. However, if you must find database privilege usage (for example, which privileges that have been granted to a given role are used), and generate a report of the used and unused privileges, then you can create a privilege capture. See Oracle Database Vault Administrator's Guide for more information.System Privileges That Can Be Audited
You can audit the use of almost any system privilege. To find a list of auditable system privileges, you can query the SYSTEM_PRIVILEGE_MAP table.
For example:
SELECT NAME FROM SYSTEM_PRIVILEGE_MAP; NAME ------------- ALTER ANY CUBE BUILD PROCESS SELECT ANY CUBE BUILD PROCESS ALTER ANY MEASURE FOLDER ...
Similar to action audit options, privilege auditing audits the use of system privileges that have been granted to database users. If you set similar audit options for both SQL statement and privilege auditing, then only a single audit record is generated. For example, if two policies exist, with one auditing EXECUTE PROCEDURE specifically on the HR.PROC procedure and the second auditing EXECUTE PROCEDURE in general (all procedures), then only one audit record is written.
Privilege auditing does not occur if the action is already permitted by the existing owner and object privileges. Privilege auditing is triggered only if the privileges are insufficient, that is, only if what makes the action possible is a system privilege. For example, suppose that user SCOTT has been granted the SELECT ANY TABLE privilege and SELECT ANY TABLE is being audited. If SCOTT selects his own table (for example, SCOTT.EMP), then the SELECT ANY TABLE privilege is not used. Because he performed the SELECT statement within his own schema, no audit record is generated. On the other hand, if SCOTT selects from another schema (for example, the HR.EMPLOYEES table), then an audit record is generated. Because SCOTT selected a table outside his own schema, he needed to use the SELECT ANY TABLE privilege.
System Privileges That Cannot Be Audited
Several system privileges cannot be audited.
These privileges are:
Configuring a Unified Audit Policy to Capture System Privilege Use
To create a unified audit policy to capture system privilege use, you should include the PRIVILEGES clause in the CREATE AUDIT POLICY statement.
-
Use the following syntax to create a unified audit policy that audits privileges:
CREATE AUDIT POLICY policy_name PRIVILEGES privilege1 [, privilege2];
For example:
CREATE AUDIT POLICY my_simple_priv_policy PRIVILEGES SELECT ANY TABLE, CREATE LIBRARY;
You can build more complex privilege unified audit policies, such as those that include conditions. Remember that after you create the policy, you must use the AUDIT statement to enable it.
Example: Auditing a User Who Has ANY Privileges
Example 22-3 shows how to audit several ANY privileges of the user HR_MGR.
Example: Using a Condition to Audit a System Privilege
Example 22-4 shows how to use a condition to audit privileges that are used by two operating system users, psmith and jrawlins.
How System Privilege Unified Audit Policies Appear in the Audit Trail
If necessary, you should run the DBMS_AUDIT_MGMT.FLUSH_UNIFIIED_AUDIT_TRAIL procedure to write the audit records to disk.
EXEC DBMS_AUDIT_MGMT.FLUSH_UNIFIED_AUDIT_TRAIL;
See "Manually Flushing Audit Records to the Audit Trail in Queued-Write Mode" for more information.
The following example, based on the unified audit policy os_users_priv_pol that was created in Example 22-4, shows a list of privileges used by the operating system user psmith.
SELECT SYSTEM_PRIVILEGE_USED FROM UNIFIED_AUDIT_TRAIL WHERE OS_USERNAME = 'PSMITH' AND UNIFIED_AUDIT_POLICIES = 'OS_USERS_PRIV_POL'; SYSTEM_PRIVILEGE_USED ---------------------- SELECT ANY TABLE DROP ANY TABLE
Note:
If you have created an audit policy for theSELECT ANY TABLE system privilege, whether the user has exercised the READ object privilege or the SELECT object privilege will affect the actions that the audit trail captures. See Auditing SELECT and the READ ANY TABLE or SELECT ANY TABLE Privilege for more information.Auditing Administrative Users
Oracle Database provides a set of default administrative user accounts, such as SYS. You can create unified audit policies to capture the actions of these users.
Topics:
Administrative User Accounts That Can Be Audited
Oracle Database provides several administrative user accounts that are associated with administrative privileges.
Table 22-1 lists default administrative user accounts and the administrative privileges with which they are typically associated.
Table 22-1 Administrative Users and Administrative Privileges
| Administrative User Account | Administrative Privilege |
|---|---|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Footnote 1 PUBLIC refers to the user PUBLIC, which is the effective user when you log in with the SYSOPER administrative privilege. It does not refer to the PUBLIC role.
Configuring a Unified Audit Policy to Capture Administrator Activities
You can use the CREATE AUDIT POLICY statement to audit administrative users.
-
To audit administrative users, create a unified audit policy and then apply this policy to the user, the same as you would for non-administrative users. Note that top-level statements by administrative users are mandatorily audited until the database opens.
Example: Auditing the SYS User
Example 22-5 shows how to audit grants of the DBMS_FGA PL/SQL package by user SYS.
Auditing Object Actions
You can use the CREATE AUDIT POLICY statement to audit object actions.
Topics:
About Auditing Object Actions
You can audit actions performed on specific objects, such as SELECT or UPDATE statements on the HR.EMPLOYEES table.
The audit can include both DDL and DML statements that were used on the object. A single unified audit policy can contain both privilege and action audit options, as well as audit options set for multiple objects.
Object Actions That Can Be Audited
Auditing object actions can be broad or focused, for example, by auditing the activities of all database users or of only a select list of activities.
Table 22-2 lists the object-level standard database action options. Audit policies for the SELECT SQL statement will capture READ actions as well as SELECT actions.
Table 22-2 Object-Level Standard Database Action Audit Option
| Object | SQL Action That Can Be Audited |
|---|---|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Configuring an Object Action Unified Audit Policy
To create a unified audit policy that captures object actions, you can include the ACTIONS clause in the CREATE AUDIT POLICY statement.
-
Use the following syntax to create a unified audit policy that audits object actions:
CREATE AUDIT POLICY policy_name ACTIONS action1 [, action2 ON object1] [, action3 ON object2];
For example:
CREATE AUDIT POLICY my_simple_obj_policy ACTIONS SELECT ON OE.ORDERS, UPDATE ON HR.EMPLOYEES;
Note that you can audit multiple actions on multiple objects, as shown in this example.
You can build complex object action unified audit policies, such as those that include conditions. Remember that after you create the policy, you must use the AUDIT statement to enable it.
Example: Auditing Actions on SYS Objects
Example 22-6 shows how to create an audit policy that audits SELECT statements on the SYS.USER$ system table. The audit policy applies to all users, including SYS and SYSTEM.
Example: Auditing Multiple Actions on One Object
Example 22-7 shows how to audit multiple SQL statements performed by users jrandolph and phawkins on the app_lib library.
Example: Auditing Both Actions and Privileges on an Object
Example 22-8 shows a variation of Example 22-7, in which all EXECUTE and GRANT statements on the app_lib library using the CREATE LIBRARY privilege are audited.
Example 22-8 Auditing Both Actions and Privileges on an Object
CREATE AUDIT POLICY actions_on_hr_emp_pol2 PRIVILEGES CREATE LIBRARY ACTIONS EXECUTE, GRANT ON app_lib; AUDIT POLICY actions_on_hr_emp_pol2 BY jrandolph, phawkins;
You can audit directory objects. For example, suppose you create a directory object that contains a preprocessor program that the ORACLE_LOADER access driver will use. You can audit anyone who runs this program within this directory object.
Example: Auditing All Actions on a Table
You can use the keyword ALL to audit all actions. Example 22-9 shows how to audit all actions on the HR.EMPLOYEES table, except actions by user pmulligan.
Example: Auditing All Actions in the Database
Example 22-10 shows how to audit all actions in the entire database.
How Object Action Unified Audit Policies Appear in the Audit Trail
If necessary, you should run the DBMS_AUDIT_MGMT.FLUSH_UNIFIIED_AUDIT_TRAIL procedure to write the audit records to disk.
EXEC DBMS_AUDIT_MGMT.FLUSH_UNIFIED_AUDIT_TRAIL;
See "Manually Flushing Audit Records to the Audit Trail in Queued-Write Mode" for more information.
SELECT ACTION_NAME, OBJECT_SCHEMA, OBJECT_NAME FROM UNIFIED_AUDIT_TRAIL WHERE DBUSERNAME = 'SYS'; ACTION_NAME OBJECT_SCHEMA OBJECT_NAME ----------- ------------- ------------ SELECT HR EMPLOYEES
Auditing Functions, Procedures, Packages, and Triggers
You can audit functions, procedures, PL/SQL packages, and triggers.
The areas that you can audit are as follows:
-
You can individually audit standalone functions, standalone procedures, and PL/SQL packages.
-
If you audit a PL/SQL package, Oracle Database audits all functions and procedures within the package.
-
If you enable auditing for all executions, Oracle Database audits all triggers in the database, as well as all the functions and procedures within PL/SQL packages.
-
You cannot audit individual functions or procedures within a PL/SQL package.
Auditing Oracle Virtual Private Database Policy Functions
If you want to audit functions that are associated with Oracle Virtual Private Database policies, be aware of the affect this type of auditing has on dynamic VPD policies, static VPD policies, and context-sensitive VPD policies.
-
Dynamic policies: Oracle Database evaluates the policy function twice, once during SQL statement parsing and again during execution. As a result, two audit records are generated for each evaluation.
-
Static policies: Oracle Database evaluates the policy function once and then caches it in the SGA. As a result, only one audit record is generated.
-
Context-sensitive policies: Oracle Database executes the policy function once, during statement parsing. As a result, only one audit record is generated.
Using Unified Auditing with Editioned Objects
When an editioned object has a unified audit policy, it applies in all editions in which the object is visible.
When an editioned object is actualized, any unified audit policies that are attached to it are newly attached to the new actual occurrence. When you newly apply a unified audit policy to an inherited editioned object, this action will actualize it.
You can find the editions in which audited objects appear by querying the OBJECT_NAME and OBJ_EDITION_NAME columns in the UNIFIED_AUDIT_TRAIL data dictionary view.
See Also:
Oracle Database Development Guide for detailed information about editionsAuditing SELECT and the READ ANY TABLE or SELECT ANY TABLE Privilege
You can use the CREATE AUDIT POLICY statement to audit the SELECT statement and the READ ANY TABLE or SELECT ANY TABLE privilege.
Topics:
-
About Auditing the SELECT Statement and READ ANY TABLE System Privilege
-
Creating a Unified Audit Policy to Capture READ Object Privilege Operations
-
How the Unified Audit Trail Captures READ ANY TABLE and SELECT ANY TABLE
About Auditing the SELECT Statement and READ ANY TABLE System Privilege
You can create unified audit policies that capture the use of the READ ANY TABLE system privilege.
Based on the action that the user tried to perform and the privilege that was granted to the user, the SYSTEM_PRIVILEGE_USED column of the UNIFIED_AUDIT_TRAIL data dictionary view will record either the READ ANY TABLE system privilege or the SELECT ANY TABLE system privilege. For example, suppose the user has been granted the SELECT ANY TABLE privilege and then performs a query on a table. The audit trail will record that the user used the SELECT ANY TABLE system privilege. If the user was granted READ ANY TABLE and performed the same query, then the READ ANY TABLE privilege is recorded.
Creating a Unified Audit Policy to Capture READ Object Privilege Operations
You can create unified audit policies that capture READ object privilege operations.
How the Unified Audit Trail Captures READ ANY TABLE and SELECT ANY TABLE
Table 22-3 describes how the unified audit trail captures SELECT behavior, based on whether a user was granted the READ ANY TABLE or the SELECT ANY TABLE system privilege.
Table 22-3 Auditing Behavior for the READ ANY TABLE and SELECT ANY TABLE System Privileges
| Statement User Issues | Privilege Granted to User | System Privilege Being Audited | Expected UNIFIED_AUDIT_TRAIL Behavior |
|---|---|---|---|
|
|
|
|
Record inserted into
|
|
|
No record |
||
|
Both |
Record inserted into
|
||
|
Neither |
No record |
||
|
|
|
|
No record |
|
|
Record inserted into
|
||
|
Both |
Record inserted into
|
||
|
Neither |
No record |
||
|
|
Both |
|
No record, because |
|
|
Record inserted into
|
||
|
Both |
Record inserted into
|
||
|
Neither |
No record |
||
|
|
Neither |
|
No record |
|
|
No record |
||
|
Both |
No record |
||
|
Neither |
No record |
||
|
|
|
|
Record inserted into
|
|
|
No record |
||
|
Both |
Record inserted into
|
||
|
Neither |
No record |
||
|
|
|
|
No record |
|
|
No record |
||
|
Both |
No record |
||
|
Neither |
No record |
||
|
|
Both |
|
Record inserted into
|
|
|
No record, because |
||
|
Both |
Record inserted into
|
||
|
Neither |
No record |
||
|
|
Neither |
|
No record |
|
|
No record |
||
|
Both |
No record |
||
|
Neither |
No record |
How Auditing Works for SQL Statements and Privileges in a Multitier Environment
You can create a unified audit policy to audit the activities of a client in a multitier environment.
In a multitier environment, Oracle Database preserves the identity of a client through all tiers. Thus, you can audit actions taken on behalf of the client by a middle-tier application, by using the BY user clause in the AUDIT statement for your policy. The audit applies to all user sessions, including proxy sessions.
The middle tier can also set the user client identity in a database session, enabling the auditing of end-user actions through the middle-tier application. The end-user client identity then shows up in the audit trail.
Example 22-11 shows how to audit SELECT TABLE statements issued by the user jackson.
Example 22-11 Using AUDIT to Audit a SQL Statement for a User
CREATE AUDIT POLICY tab_pol PRIVILEGES CREATE ANY TABLE ACTIONS CREATE TABLE; AUDIT tab_pol BY jackson;
You can audit user activity in a multitier environment. Once audited, you can verify these activities by querying the UNIFIED_AUDIT_TRAIL data dictionary view.
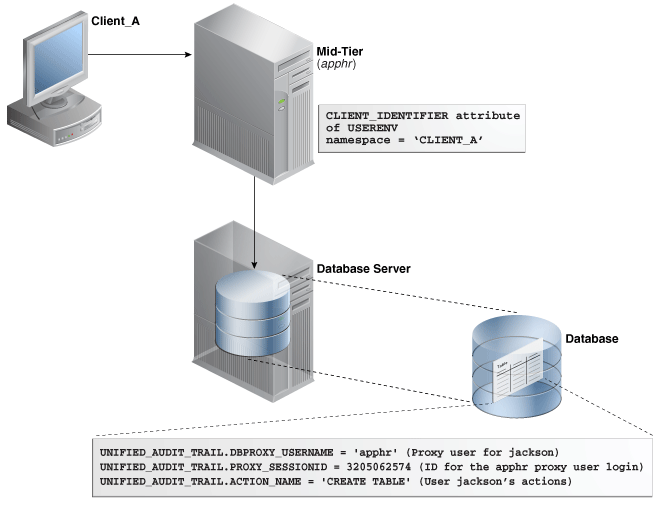
Figure 22-1 illustrates how you can audit proxy users by querying the PROXY_SESSIONID, ACTION_NAME, and SESSION_ID columns of the UNIFIED_AUDIT_TRAIL view. In this scenario, both the database user and proxy user accounts are known to the database. Session pooling can be used.
Figure 22-2 illustrates how you can audit client identifier information across multiple database sessions by querying the CLIENT_ID column of the DBA_AUDIT_TRAIL data dictionary view. In this scenario, the client identifier has been set to CLIENT_A. As with the proxy user-database user scenario described in Figure 22-1, session pooling can be used.
Figure 22-2 Auditing Client Identifier Information Across Sessions
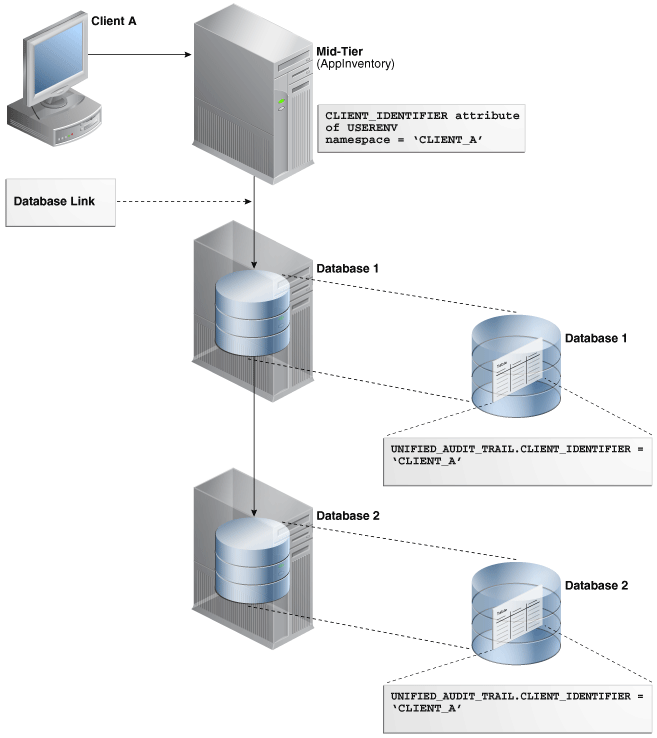
Description of "Figure 22-2 Auditing Client Identifier Information Across Sessions"
See Also:
"Preserving User Identity in Multitiered Environments" for more information about user authentication in a multitiered environmentCreating a Condition for a Unified Audit Policy
You can use the CREATE AUDIT POLICY statement to create conditions for a unified audit policy.
Topics:
-
Example: Auditing Both a System-Wide and a Schema-Specific Action
-
Example: Unified Audit Session ID of a Current Administrative User Session
-
Example: Unified Audit Session ID of a Current Non-Administrative User Session
About Conditions in Unified Audit Policies
You can create a unified audit policy that uses a SYS_CONTEXT namespace-attribute pair to specify a condition, such as a specific user who may fulfil the audit condition, or a computer host where the audit condition is fulfilled.
If the audit condition is satisfied, then Oracle Database creates an audit record for the event. As part of the condition definition, you must specify whether the audited condition is evaluated per statement occurrence, session, or database instance.
Note:
Audit conditions can use both secure and insecure application contexts.Configuring a Unified Audit Policy with a Condition
To create a unified audit policy that uses a condition, you can include the WHEN clause in the CREATE AUDIT POLICY statement.
-
Use the following syntax to create a unified audit policy that uses a condition:
CREATE AUDIT POLICY policy_name action_privilege_role_audit_option [WHEN function_operation_value_list_1 [[AND | OR] function_operation_value_list_n] EVALUATE PER STATEMENT | SESSION | INSTANCE];
In this specification:
-
action_privilege_role_audit_optionrefers to audit options for system actions, object actions, privileges, and roles. -
WHENdefines the condition. It has the following components:-
functionuses the following types of functions:Numeric functions, such as
BITAND,CEIL,FLOOR, andLNPOWERCharacter functions that return character values, such as
CONCAT,LOWER, andUPPERCharacter functions that return numeric values, such as
LENGTHorINSTREnvironment and identifier functions, such as
SYS_CONTEXTandUID. ForSYS_CONTEXT, in most cases, you may want to use theUSERENVnamespace, which is described in Oracle Database SQL Language Reference. -
operationcan be any the following operators:AND,OR,IN,NOT IN,=,<,>,<> -
value_listrefers to the condition for which you are testing.
You can include additional conditions for each
function_operation_value_listset, separated byANDorOR.When you write the
WHENclause, follow these guidelines:-
Enclose the entire
function operation valuesetting in single quotation marks. Within the clause, enclose each quoted component within two pairs of single quotation marks. Do not use double quotation marks. -
Do not exceed 4000 bytes for the
WHENcondition.
-
-
EVALUATE PERrefers to the following options:-
STATEMENTevaluates the condition for each relevant auditable statement that occurs. -
SESSIONevaluates the condition only once during the session, and then caches and re-uses the result during the remainder of the session. Oracle Database evaluates the condition the first time the policy is used, and then stores the result in UGA memory afterward. -
INSTANCEevaluates the condition only once during the database instance lifetime. After Oracle Database evaluates the condition, it caches and re-uses the result for the remainder of the instance lifetime. As with theSESSIONevaluation, the evaluation takes place the first time it is needed, and then the results are stored in UGA memory afterward.
-
For example:
CREATE AUDIT POLICY oe_orders_pol ACTIONS UPDATE ON OE.ORDERS WHEN 'SYS_CONTEXT(''USERENV'', ''IDENTIFICATION_TYPE'') = ''EXTERNAL''' EVALUATE PER STATEMENT; -
Remember that after you create the policy, you must use the AUDIT statement to enable it.
See Also:
-
Oracle Database SQL Language Reference for more information about functions that you can use in conditions
-
"Using the Unified Audit Policies or AUDIT Settings in a Multitenant Environment"
Example: Auditing Access to SQL*Plus
Example 22-12 shows how to audit access to the database with SQL*Plus by users who have been granted the roles emp_admin and sales_admin.
Example: Auditing Actions Not in Specific Hosts
Example 22-13 shows how to audit two actions (UPDATE and DELETE statements) on the OE.ORDERS table, but excludes the host names sales_24 and sales_12 from the audit. It performs the audit on a per session basis and writes audit records for failed attempts only.
Example: Auditing Both a System-Wide and a Schema-Specific Action
Example 22-14 shows a variation of Example 22-13 in which the UPDATE statement is audited system wide. The DELETE statement audit is still specific to the OE.ORDERS table.
Example: Auditing a Condition Per Statement Occurrence
Example 22-15 shows how to audit a condition based on each occurrence of the DELETE statement on the OE.ORDERS table and exclude user jmartin from the audit.
Example: Unified Audit Session ID of a Current Administrative User Session
Example 22-16 shows how to find the unified audit session ID of current user session for an administrative user. Note that in mixed mode auditing, the UNIFIED_AUDIT_SESSIONID value in the USERENV namespace is different from the value that is recorded by the SESSIONID parameter. Hence, if you are using mixed mode auditing and want to find the correct audit session ID, you should use the USERENV UNIFIED_AUDIT_SESSIONID parameter, not the SESSIONID parameter. In pure unified auditing, the SESSIONID and UNIFIED_AUDIT_SESSIONID values are the same.
Example 22-16 Unified Audit Session ID of a Current Administrative User Session
CONNECT SYS AS SYSDBA
Enter password: password
SELECT SYS_CONTEXT('USERENV', 'UNIFIED_AUDIT_SESSIONID') FROM DUAL;
Output similar to the following appears:
SYS_CONTEXT('USERENV','UNIFIED_AUDIT_SESSIONID')
--------------------------------------------------------------------------------
2318470183
Example: Unified Audit Session ID of a Current Non-Administrative User Session
Example 22-17 shows how to find the unified audit session ID of a current user session for a non-administrative user.
Example 22-17 Unified Audit Session ID of a Current Non-Administrative User Session
CONNECT mblake -- Or, CONNECT mblake@hrpdb for a PDB
Enter password: password
SELECT SYS_CONTEXT('USERENV', 'UNIFIED_AUDIT_SESSIONID') FROM DUAL;
Output similar to the following appears:
SYS_CONTEXT('USERENV','UNIFIED_AUDIT_SESSIONID')
--------------------------------------------------------------------------------
2776921346
How Audit Records from Conditions Appear in the Audit Trail
The audit record conditions themselves do not appear in the audit trail.
If the condition evaluates to true and the record is written, then the record appears in the audit trail.
Auditing Application Context Values
You can use the AUDIT statement to audit application context values.
Topics:
-
Example: Auditing Application Context Values in a Default Database
-
Example: Auditing Application Context Values from Oracle Label Security
About Auditing Application Context Values
You can capture application context values in the unified audit trail. This feature enables you to capture any application context values set by the database applications, while executing the audited statement.
If you plan to audit Oracle Label Security, then this feature captures session label activity for the database audit trail. The audit trail records all the values retrieved for the specified context-attribute value pairs.
The application context audit setting or the audit policy have session static semantics. In other words, if a new policy is enabled for a user, then the subsequent user sessions will see an effect of this command. After the session is established, then the policies and contexts settings are loaded and the subsequent AUDIT statements have no effect on that session.
For multitenant environments, the application context audit policy applies only to the current PDB.
See Also:
-
Chapter 9, "Using Application Contexts to Retrieve User Information," for detailed information about application contexts
-
"Using the Unified Audit Policies or AUDIT Settings in a Multitenant Environment"
-
Oracle Label Security Administrator's Guide for detailed information about Oracle Label Security
Configuring Application Context Audit Settings
To configure auditing for application context values, use the AUDIT statement with the CONTEXT keyword. (You do not create an unified audit policy for this type of auditing.)
-
Use the following syntax to configure auditing for application context values:
AUDIT CONTEXT NAMESPACE context_name1 ATTRIBUTES attribute1 [, attribute2] [, CONTEXT NAMESPACE context_name2 ATTRIBUTES attribute1 [, attribute2]] [BY user_list];
In this specification:
-
context_name1: Optionally, you can include one additionalCONTEXTname-attribute value pair. -
user_listis an optional list of database user accounts. Separate multiple names with a comma. If you omit this setting, then Oracle Database configures the application context policy for all users. When each user logs in, a list of all pertinent application contexts and their attributes is cached for the user session.
For example:
AUDIT CONTEXT NAMESPACE clientcontext3 ATTRIBUTES module, action, CONTEXT NAMESPACE ols_session_labels ATTRIBUTES ols_pol1, ols_pol3 BY appuser1, appuser2;
-
To find a list of currently configured application context audit settings, query the AUDIT_UNIFIED_CONTEXTS data dictionary view.
Disabling Application Context Audit Settings
You can use the NOAUDIT statement to disable application context audit settings.
-
To disable an application context audit setting, specify the namespace and attribute settings in the
NOAUDITstatement. You can enter the attributes in any order (that is, they do not need to match the order used in the correspondingAUDIT CONTEXTstatement.)For example:
NOAUDIT CONTEXT NAMESPACE client_context ATTRIBUTES module, CONTEXT NAMESPACE ols_session_labels ATTRIBUTES ols_pol1, ols_pol3 BY appuser1, appuser2;
To find the currently audited application contexts, query the AUDIT_UNIFIED_CONTEXTS data dictionary view.
Example: Auditing Application Context Values in a Default Database
Example 22-18 shows how to audit the clientcontext application values for the module and action attributes, by the user appuser1.
Example: Auditing Application Context Values from Oracle Label Security
Example 22-19 shows how to audit an application context for Oracle Label Security called ols_session_labels, for the attributes ols_pol1 and ols_pol2.
How Audited Application Contexts Appear in the Audit Trail
If necessary, you should run the DBMS_AUDIT_MGMT.FLUSH_UNIFIIED_AUDIT_TRAIL procedure to write the audit records to disk.
EXEC DBMS_AUDIT_MGMT.FLUSH_UNIFIED_AUDIT_TRAIL;
See "Manually Flushing Audit Records to the Audit Trail in Queued-Write Mode" for more information.
The APPLICATION_CONTEXTS column of the UNIFIED_AUDIT_TRAIL data dictionary view shows application context audit data. The application contexts appear as a list of semi-colon separated values.
For example:
SELECT APPLICATION_CONTEXTS FROM UNIFIED_AUDIT_TRAIL WHERE UNIFIED_AUDIT_POLICIES = 'app_audit_pol'; APPLICATION_CONTEXTS ---------------------------------------------------------- CLIENT_CONTEXT.APPROLE=MANAGER;E2E_CONTEXT.USERNAME=PSMITH
Auditing Oracle Database Real Application Security Events
You can use the CREATE AUDIT POLICY statement to audit Oracle Database Real Application Security events.
-
About Auditing Oracle Database Real Application Security Events
-
Oracle Database Real Application Security Events That You Can Audit
-
Configuring a Unified Audit Policy for Oracle Database Real Application Security
-
Example: Auditing Real Application Security User Account Modifications
-
Example: Using a Condition in a Real Application Security Unified Audit Policy
-
How Oracle Database Real Application Security Events Appear in the Audit Trail
See Also:
-
"Oracle Database Real Application Security Predfined Audit Policies"
-
Oracle Database Real Application Security Administrator's and Developer's Guide for detailed information about Oracle Database Real Application Security
About Auditing Oracle Database Real Application Security Events
As with all unified auditing, you must have the AUDIT_ADMIN role before you can audit Oracle Database Real Application Security events. To access the audit trail, you can query the UNIFIED_AUDIT_TRAIL data dictionary view, whose Real Application Security-specific columns begin with XS_.
Real Application Security-specific views are as follows:
-
DBA_XS_AUDIT_TRAILprovides detailed information about Real Application Security events that were audited. -
DBA_XS_AUDIT_POLICY_OPTIONSdescribes the auditing options that were defined for Real Application Security unified audit policies. -
DBA_XS_ENB_AUDIT_POLICIESlists users for whom Real Application Security unified audit polices are enabled.
Oracle Database Real Application Security Events That You Can Audit
To find a list of auditable Real Application Security events that you can audit, query the COMPONENT and NAME columns of the AUDITABLE_SYSTEM_ACTIONS data dictionary view, as follows:
SELECT NAME FROM AUDITABLE_SYSTEM_ACTIONS WHERE COMPONENT = 'XS'; NAME ------------- CREATE USER UPDATE USER DELETE USER ...
The following tables describe in detail the Oracle Database Real Application Security audit events.
-
Table 22-4, "Oracle Database Real Application Security User and Role Audit Events"
-
Table 22-5, "Oracle Database Real Application Security Security Class and ACL Audit Events"
-
Table 22-6, "Oracle Database Real Application Security Session Audit Events"
-
Table 22-7, "Oracle Database Real Application Security All Actions"
Table 22-4 describes the Oracle Database Real Application Security audit events.
Table 22-4 Oracle Database Real Application Security User and Role Audit Events
| Audit Event | Description |
|---|---|
|
|
Creates an Oracle Database Real Application Security user account through the |
|
|
Updates an Oracle Database Real Application Security user account through the following procedures:
|
|
|
Deletes an Oracle Database Real Application Security user account through the through the |
|
|
Creates an Oracle Database Real Application Security role through the |
|
|
Updates an Oracle Database Real Application Security role through the following procedures:
|
|
|
Deletes an Oracle Database Real Application Security role through the through the |
|
|
Grants Oracle Database Real Application Security roles through the |
|
|
Revokes Oracle Database Real Application Security roles through the |
|
|
Adds Oracle Database Real Application Security proxy user account through the |
|
|
Removes an Oracle Database Real Application Security proxy user account through the |
|
|
Sets the Oracle Database Real Application Security user account password through the |
|
|
Sets the Oracle Database Real Application Security proxy user account verifier through the |
Table 22-5 describes the Oracle Database Real Application Security security class and namespace audit events.
Table 22-5 Oracle Database Real Application Security Security Class and ACL Audit Events
| Audit Event | Description |
|---|---|
|
|
Creates a security class through the |
|
|
Creates a security class through the following procedures:
|
|
|
Deletes a security class through the |
|
|
Creates an Access Control List (ACL) through the |
|
|
Updates an ACL through the following procedures:
|
|
|
Deletes an ACL through the |
|
|
Creates a data security policy through the |
|
|
Updates a data security policy through the following procedures:
|
|
|
Deletes a data security policy through the |
|
|
Enables extensible data security for a database table or view through the |
|
|
Disables extensible data security for a database table or view through the |
Table 22-4 describes the Oracle Database Real Application Security session audit events.
Table 22-6 Oracle Database Real Application Security Session Audit Events
| Audit Event | Description |
|---|---|
|
|
Creates a session through the |
|
|
Destroys a session through the |
|
|
Creates a namespace through the |
|
|
Deletes a namespace through the |
|
|
Creates a namespace attribute through the |
|
|
Sets a namespace attribute through the |
|
|
Gets a namespace attribute through the |
|
|
Deletes a namespace attribute through the |
|
|
Creates a namespace attribute through the |
|
|
Updates a namespace attribute through the following procedures:
|
|
|
Deletes a namespace through the |
|
|
Adds a global callback through the |
|
|
Deletes a global callback through the |
|
|
Enables a global callback through the |
|
|
Sets a session cookie through the |
|
|
Sets the time-out time for inactive sessions through the |
|
|
Sets the security context of the current lightweight user session to a newly initialized security context for a specified user through the |
|
|
Assigns or removes one or more dynamic roles for the specified user through the |
|
|
Enable a role for a lightweight user session through the |
|
|
Disables a role for a lightweight user session through the |
Table 22-7 describes the Oracle Database Real Application Security ALL audit event.
Configuring a Unified Audit Policy for Oracle Database Real Application Security
You can use the CREATE AUDIT POLICY statement to create a unified audit policy for Oracle Real Application Security.
-
Use the following syntax to create a unified audit policy for Oracle Database Real Application Security:
CREATE AUDIT POLICY policy_name ACTIONS COMPONENT=XS component_action1 [, action2];
For example:
CREATE AUDIT POLICY audit_ras_pol ACTIONS COMPONENT=XS SWITCH USER, DISABLE ROLE;
You can build more complex policies, such as those that include conditions. Remember that after you create the policy, you must use the AUDIT statement to enable it.
Example: Auditing Real Application Security User Account Modifications
Example 22-20 shows how to audit user bhurst's attempts to switch users and disable roles.
Example: Using a Condition in a Real Application Security Unified Audit Policy
Example 22-21 shows how to create Real Application Security unified audit policy that applies the audit only to actions from the nemosity computer host.
Example 22-21 Using a Condition in a Real Application Security Unified Audit Policy
CREATE AUDIT POLICY ras_acl_pol
ACTIONS DELETE ON OE.CUSTOMERS
ACTIONS COMPONENT=XS CREATE ACL, UPDATE ACL, DELETE ACL
WHEN 'SYS_CONTEXT(''USERENV'', ''HOST'') = ''nemosity'''
EVALUATE PER INSTANCE;
AUDIT POLICY ras_acl_pol BY pfitch;
How Oracle Database Real Application Security Events Appear in the Audit Trail
If necessary, you should run the DBMS_AUDIT_MGMT.FLUSH_UNIFIIED_AUDIT_TRAIL procedure to write the audit records to disk.
EXEC DBMS_AUDIT_MGMT.FLUSH_UNIFIED_AUDIT_TRAIL;
See "Manually Flushing Audit Records to the Audit Trail in Queued-Write Mode" for more information.
The following example queries the Real Application Security-specific view, DBA_XS_AUDIT_TRAIL:
SELECT XS_USER_NAME FROM DBA_XS_AUDIT_TRAIL WHERE XS_ENABLED_ROLE = 'CLERK'; XS_USER_NAME ------------- USER2
Auditing Oracle Recovery Manager Events
You can use the CREATE AUDIT POLICY statement to audit Oracle Recovery Manager events.
-
Oracle Recovery Manager Events That the Unified Audit Trail Captures
-
How Oracle Recovery Manager Audited Events Appear in the Audit Trail
About Auditing Oracle Recovery Manager Events
Unlike other Oracle Database components, you do not create a unified audit policy for Oracle Recovery Manager events. The UNIFIED_AUDIT_TRAIL data dictionary view has a set of fields, whose names begin with RMAN_, that automatically record Recovery Manager-related events.
However, you must have the AUDIT_ADMIN or AUDIT_VIEWER role in order to query the UNIFIED_AUDIT_TRAIL view to see these events. If you have the SYSBACKUP or the SYSDBA administrative privilege, then you can find additional information about Recovery Manager jobs by querying views such as V$RMAN_STATUS or V$RMAN_BACKUP_JOB_DETAILS.
Oracle Recovery Manager Events That the Unified Audit Trail Captures
Table 22-8 shows the Oracle Recovery Manager-specific columns in the UNIFIED_AUDIT_TRAIL data dictionary view.
Table 22-8 Oracle Recovery Manager Columns in UNIFIED_AUDIT_TRAIL View
| Recovery Manager Column | Description |
|---|---|
|
|
Recovery Manager session identifier. Together with the |
|
|
Timestamp for the session. Together with the |
|
|
The Recovery Manager operation executed by the job. One row is added for each distinct operation within a Recovery Manager session. For example, a backup job contains |
|
|
Type of objects involved in a Recovery Manager session. It contains one of the following values. If the Recovery Manager session does not satisfy more than one of them, then preference is given in the following order, from top to bottom of the list.
|
|
|
Device associated with a Recovery Manager session. This column can be |
How Oracle Recovery Manager Audited Events Appear in the Audit Trail
If necessary, you should run the DBMS_AUDIT_MGMT.FLUSH_UNIFIIED_AUDIT_TRAIL procedure to write the audit records to disk.
EXEC DBMS_AUDIT_MGMT.FLUSH_UNIFIED_AUDIT_TRAIL;
See "Manually Flushing Audit Records to the Audit Trail in Queued-Write Mode" for more information.
Table 22-8 lists the columns in the UNIFIED_AUDIT_TRAIL data dictionary view that you can query to find Oracle Recovery Manager-specific audit data.
For example:
SELECT RMAN_OPERATION FROM UNIFIED_AUDIT_TRAIL WHERE RMAN_OBJECT_TYPE = 'DB FULL'; RMAN_OPERATION --------------- BACKUP
Auditing Oracle Database Vault Events
If you have Oracle Database Vault enabled, then you can create unified audit policies to capture activities related to Database Vault.
-
Oracle Database Vault Events That the Unified Audit Trail Captures
-
Configuring a Unified Audit Policy for Oracle Database Vault
-
How Oracle Database Vault Audited Events Appear in the Audit Trail
See Also:
-
Oracle Database Vault Administrator's Guide for detailed information about Oracle Database Vault audit policies
About Auditing Oracle Database Vault Events
As with all unified auditing, you must have the AUDIT_ADMIN role before you can audit Oracle Database Vault events. To create Oracle Database Vault unified audit policies, you must set the CREATE AUDIT POLICY statement's COMPONENT clause to DV, and then specify an action, such as Rule Set Failure, and an object, such as the name of a rule set.
To access the audit trail, you can query the following views:
-
UNIFIED_AUDIT_TRAIL -
SYS.DV$CONFIGURATION_AUDIT -
SYS.DV$ENFORCEMENT_AUDIT
In the UNIFIED_AUDIT_TRAIL view, the Oracle Database Vault-specific columns begin with DV_. You must have the AUDIT_VIEWER role before you can query the UNIFIED_AUDIT_TRAIL view.
In addition to these views, the Database Vault reports capture the results of Database Vault-specific unified audit policies.
See Also:
Oracle Database Vault Administrator's Guide for more information about Database Vault reportsWho Is Audited in Oracle Database Vault?
Users who are audited in Oracle Database Vault include Database Vault administrators and users whose activities affect Database Vault enforcement policies.
-
Database Vault administrators. All configuration changes that are made to Oracle Database Vault are mandatorily audited. The auditing captures activities such as creating, modifying, or deleting realms, factors, command rules, rule sets, rules, and so on.The
SYS.DV$CONFIGURATION_AUDITdata dictionary view captures configuration changes made by Database Vault administrators. -
Users whose activities affect Oracle Database Vault enforcement policies. The
SYS.DV$ENFORCEMENT_AUDITdata dictionary view captures enforcement-related audits
See Also:
Oracle Database Vault Administrator's Guide for more information about theSYS.DV$CONFIGURATION_AUDIT and SYS.DV$ENFORCEMENT_AUDIT data dictionary viewsOracle Database Vault Events That the Unified Audit Trail Captures
The audit trail in an Oracle Database Vault environment captures all configuration changes or attempts at changes to Database Vault policies, and violations by users to existing Database Vault policies.
-
All configuration changes or attempts at changes to Oracle Database Vault policies. It captures both Database Vault administrator changes and attempts made by unauthorized users.
-
Violations by users to existing Database Vault policies. For example, if you create a policy to prevent users from accessing a specific schema table during non-work hours, the audit trail will capture this activity.
The following tables describe the Oracle Database Vault audit events:
-
Table 22-10, "Oracle Database Vault Rule Set and Rule Audit Events"
-
Table 22-11, "Oracle Database Vault Command Rule Audit Events"
-
Table 22-13, "Oracle Database Vault Secure Application Role Audit Events"
-
Table 22-14, "Oracle Database Vault Oracle Label Security Audit Events"
-
Table 22-15, "Oracle Database Vault Oracle Data Pump Audit Events"
-
Table 22-16, "Oracle Database Vault Enable and Disable Audit Events"
Table 22-9 describes the Oracle Database Vault realm audit events.
Table 22-9 Oracle Database Vault Realm Audit Events
| Audit Event | Description |
|---|---|
|
|
Creates a realm through the |
|
|
Updates a realm through the |
|
|
Renames a realm through the |
|
|
Deletes a realm through the |
|
|
Deletes a realm and its related Database Vault configuration information through the |
|
|
Adds an authorization to the realm through the |
|
|
Removes an authorization from the realm through the |
|
|
Updates a realm authorization through the |
|
|
Adds an object to a realm authorization through the |
|
|
Removes an object from a realm authorization through the |
Table 22-10 describes the Oracle Database Vault rule set and rule audit events.
Table 22-10 Oracle Database Vault Rule Set and Rule Audit Events
| Audit Event | Description |
|---|---|
|
|
Creates a rule set through the |
|
|
Updates a rule set through the |
|
|
Renames a rule set through the |
|
|
Deletes a rule set through the |
|
|
Adds a rule to an existing rule set through the |
|
|
Removes a rule from an existing rule set through the |
|
|
Creates a rule through the |
|
|
Updates a rule through the |
|
|
Renames a rule through the |
|
|
Deletes a rule through the |
|
|
Synchronizes the rules in Oracle Database Vault and Advanced Queuing Rules engine through the |
Table 22-11 describes the Oracle Database Vault command rule audit events.
Table 22-11 Oracle Database Vault Command Rule Audit Events
| Audit Event | Description |
|---|---|
|
|
Creates a command rule through the |
|
|
Deletes a command rule through the |
|
|
Updates a command rule through the |
Table 22-12 describes the Oracle Database Vault factor audit events.
Table 22-12 Oracle Database Vault Factor Audit Events
| Audit Event | Description |
|---|---|
|
|
Creates a factor type through the |
|
|
Deletes a factor type through the |
|
|
Updates a factor type through the |
|
|
Renames a factor type through the |
|
|
Creates a factor through the |
|
|
Updates a factor through the |
|
|
Deletes a factor through the |
|
|
Renames a factor through the |
|
|
Specifies a parent-child relationship between two factors through the |
|
|
Removes the parent-child relationship between two factors through the |
|
|
Specifies that the label for a factor contributes to the Oracle Label Security label for a policy, through the |
|
|
Removes factor label from being associated with an Oracle Label Security label for a policy, through the |
|
|
Creates a factor identity through the |
|
|
Updates a factor identity through the |
|
|
Associates an identity with a different factor through the |
|
|
Updates the value of an identity through the |
|
|
Deletes an existing factor identity through the |
|
|
Creates a factor identity map through the |
|
|
Deletes a factor identity map through the |
|
|
Adds an Oracle Database Real Application Clusters database node to the domain factor identities and labels it according to the Oracle Label Security policy, through the |
|
|
Drops an Oracle RAC node from the domain factor identities through the |
Table 22-13 describes the Oracle Database Vault secure application role audit events.
Table 22-13 Oracle Database Vault Secure Application Role Audit Events
| Audit Event | Description |
|---|---|
|
|
Creates an Oracle Database Vault secure application role through the |
|
|
Deletes an Oracle Database Vault secure application role through the |
|
|
Updates an Oracle Database Vault secure application role through the |
|
|
Renames an Oracle Database Vault secure application role through the |
Table 22-14 describes the Oracle Database Vault Oracle Label Security audit events.
Table 22-14 Oracle Database Vault Oracle Label Security Audit Events
| Audit Event | Description |
|---|---|
|
|
Creates an Oracle Label Security policy label through the |
|
|
Deletes an Oracle Label Security policy label through the |
|
|
Specifies the algorithm that is used to merge labels when computing the label for a factor, or the Oracle Label Security Session label, through the |
|
|
Changes the Oracle Label Security merge label algorithm through the |
|
|
Deletes all Oracle Database Vault objects related to an Oracle Label Security policy, through the |
Table 22-15 describes the Oracle Database Vault Oracle Data Pump audit events.
Table 22-15 Oracle Database Vault Oracle Data Pump Audit Events
| Audit Event | Description |
|---|---|
|
|
Authorizes an Oracle Data Pump user through the |
|
|
Removes from authorization an Oracle Data Pump user through the |
Table 22-16 lists the Oracle Database Vault events that can be captured and made available to the audit trail.
Configuring a Unified Audit Policy for Oracle Database Vault
To create a unified audit policy for Oracle Database Vault events, include the ACTIONS and ACTIONS COMPONENT clauses in the CREATE AUDIT POLICY statement.
-
Use the following syntax to create an Oracle Database Vault unified audit policy:
CREATE AUDIT POLICY policy_name ACTIONS action1 [,action2 ] ACTIONS COMPONENT= DV DV_action ON DV_object [,DV_action2 ON DV_object2]
In this specification:
-
DV_actionis one of the following:-
Realm Violation,Realm Success,Realm Access -
Rule Set Failure,Rule Set Success,Rule Set Eval -
Factor Error,Factor Null,Factor Validate Error,Factor Validate False,Factor Trust Level Null,Factor Trust Level Neg,Factor All
-
-
DV_objectsis one of the following:-
Realm_Name -
Rule_Set_Name -
Factor_Name
-
-
If the object was created in lower or mixed case, then you must enclose DV_objects in double quotation marks. If you had created the object in all capital letters, then you can omit the quotation marks.
For example, to audit realm violations on the Database Vault Account Management realm:
CREATE AUDIT POLICY audit_dv ACTIONS CREATE TABLE, SELECT ACTIONS COMPONENT=DV Realm Violation ON "Database Vault Account Management";
You can build more complex policies, such as those that include conditions. Remember that after you create the policy, you must use the AUDIT statement to enable it.
Example: Auditing Two Oracle Database Vault Events
Example 22-22 shows how to audit a realm violation and a rule set failure.
Example: Auditing Oracle Database Vault Factor Settings
Example 22-23 shows how to audit two types of errors for one factor.
How Oracle Database Vault Audited Events Appear in the Audit Trail
If necessary, you should run the DBMS_AUDIT_MGMT.FLUSH_UNIFIIED_AUDIT_TRAIL procedure to write the audit records to disk.
EXEC DBMS_AUDIT_MGMT.FLUSH_UNIFIED_AUDIT_TRAIL;
See "Manually Flushing Audit Records to the Audit Trail in Queued-Write Mode" for more information.
The DV_*columns of the UNIFIED_AUDIT_TRAIL view show Oracle Database Vault-specific audit data.
For example:
SELECT DV_RULE_SET_NAME FROM UNIFIED_AUDIT_TRAIL WHERE ACTION_NAME = 'UPDATE'; DV_RULE_SET_NAME ----------------------- Allow System Parameters
Auditing Oracle Label Security Events
If you have Oracle Label Security enabled, then you can use the CREATE AUDIT POLICY statement to audit Oracle Label Security events.
-
Oracle Label Security User Session Labels That You Can Audit
-
Configuring a Unified Audit Policy for Oracle Label Security
-
Example: Auditing Oracle Label Security Session Label Attributes
-
Example: Excluding a User form an Oracle Label Security Policy
-
How Oracle Label Security Audit Events Appear in the Audit Trail
See Also:
-
Oracle Label Security Administrator's Guide for information about Oracle Label Security data dictionary views
About Auditing Oracle Label Security Events
As with all unified auditing, you must have the AUDIT_ADMIN role before you can audit Oracle Label Security (OLS) events. To create Oracle Label Security unified audit policies, you set the CREATE AUDIT POLICY statement's COMPONENT clause to OLS.
To audit user session label information, you use the AUDIT statement to audit application context values.
To access the audit trail, query the UNIFIED_AUDIT_TRAIL data dictionary view. This view contains Oracle Label Security-specific columns whose names begin with OLS_.
Oracle Label Security Events That You Can Audit
To find a list of auditable Oracle Label Security events that you can audit, you can query the COMPONENT and NAME columns of the AUDITABLE_SYSTEM_ACTIONS data dictionary view.
For example:
SELECT NAME FROM AUDITABLE_SYSTEM_ACTIONS WHERE COMPONENT = 'Label Security'; NAME ------------- CREATE POLICY ALTER POLICY DROP POLICY ...
Table 22-17 describes in detail the Oracle Label Security audit events.
Table 22-17 Oracle Label Security Audit Events
| Audit Event | Description |
|---|---|
|
|
Creates an Oracle Label Security policy through the |
|
|
Alters an Oracle Label Security policy through the |
|
|
Drops an Oracle Label Security policy through the |
|
|
Applies a table policy through the |
|
|
Removes a table policy through the |
|
|
Covers all Oracle Label Security authorizations, including Oracle Label Security privileges and user labels to either users or trusted stored procedures. The PL/SQL procedures that correspond to the |
|
|
Covers any action that requires the user of an Oracle Label Security privilege. These actions are logons, |
|
|
Enables an Oracle Label Security policy through the following procedures:
|
|
|
Disables an Oracle Label Security policy through the following procedures:
|
|
|
Subscribes to an Oracle Internet Directory-enabled Oracle Label Security policy through the |
|
|
Unsubscribes to an Oracle Internet Directory-enabled Oracle Label Security policy through the |
|
|
Creates an Oracle Label Security data label through the |
|
|
Alters an Oracle Label Security data label through the |
|
|
Drops an Oracle Label Security data label through the |
|
|
Creates an Oracle Label Security component through the following procedures:
|
|
|
Alters an Oracle Label Security component through the following procedures:
|
|
|
Drops an Oracle Label Security component through the following procedures:
|
|
|
Enables auditing of all Oracle Label Security actions |
Oracle Label Security User Session Labels That You Can Audit
You can use the ORA_OLS_SESSION_LABELS application context to capture the usage of the user session labels for each Oracle Database event. The attributes used by this application context refer to Oracle Label Security policies.
The syntax is the same as the syntax used for application context auditing, described on "Configuring Application Context Audit Settings". For example:
AUDIT CONTEXT NAMESPACE ORA_SESSION_LABELS ATTRIBUTES policy1, policy2;
Because the recording of session labels is not user-session specific, the BY user_list clause is not required for auditing Oracle Label Security application contexts.
To disable the auditing of user session label information, you use the NOAUDIT statement. For example, to stop auditing for policies policy1 and policy2, enter the following statement:
NOAUDIT CONTEXT NAMESPACE ORA_SESSION_LABELS ATTRIBUTES policy1, policy2;
Configuring a Unified Audit Policy for Oracle Label Security
To create a unified audit policy for Oracle Label Security events, you should include the ACTIONS and ACTIONS COMPONENT clauses in the CREATE AUDIT POLICY statement.
-
Use the following syntax to create an Oracle Label Security unified audit policy:
CREATE AUDIT POLICY policy_name ACTIONS action1 [,action2 ] ACTIONS COMPONENT=OLS component_action1 [, action2];
For example:
CREATE AUDIT POLICY audit_ols ACTIONS SELECT ON OE.ORDERS ACTIONS COMPONENT=OLS ALL;
You can build more complex policies, such as those that include conditions. Remember that after you create the policy, you must use the AUDIT statement to enable it.
Example: Auditing Oracle Label Security Session Label Attributes
Example 22-24 shows how to audit ORA_OLS_SESSION_LABELS application context attributes for the Oracle Label Security policies usr_pol1 and usr_pol2.
Example: Excluding a User form an Oracle Label Security Policy
Example 22-25 shows how to create a unified audit policy that excludes actions from user ols_mgr.
Example: Auditing Oracle Label Security Policy Actions
Example 22-26 shows how to audit the DROP POLICY, DISABLE POLICY, UNSUBSCRIBE OID events, and UPDATE and DELETE statements on the HR.EMPLOYEES table. Then this policy is applied to the HR and LBACSYS users, and audit records are written to the unified audit trail only when the audited actions are successful.
How Oracle Label Security Audit Events Appear in the Audit Trail
If necessary, you should run the DBMS_AUDIT_MGMT.FLUSH_UNIFIIED_AUDIT_TRAIL procedure to write the audit records to disk.
EXEC DBMS_AUDIT_MGMT.FLUSH_UNIFIED_AUDIT_TRAIL;
See "Manually Flushing Audit Records to the Audit Trail in Queued-Write Mode" for more information.
The OLS_* columns of the UNIFIED_AUDIT_TRAIL view show Oracle Label Security-specific audit data. For example:
SELECT OLS_PRIVILEGES_USED FROM UNIFIED_AUDIT_TRAIL WHERE DBUSERNAME = 'psmith'; OLS_PRIVILEGES_USED ------------------- READ WRITEUP WRITEACROSS
The session labels that the audit trail captures are stored in the APPLICATION_CONTEXTS column of the UNIFIED_AUDIT_TRAIL view. You can use the LBACSYS.ORA_GET_AUDITED_LABEL function to retrieve session labels that are stored in the APPLICATION_CONTEXTS column. This function accepts the UNIFIED_AUDIT_TRAIL.APPLICATION_CONTEXTS column value, and the Oracle Label Security policy name as arguments, and then returns the session label that is stored in the column for the specified policy.
Example 22-27 shows how to use the LBACSYS.ORA_GET_AUDITED_LABEL function in a UNIFIED_AUDIT_TRAIL data dictionary view query.
Example 22-27 Querying for Audited Oracle Label Security Session Labels
SELECT ENTRY_ID, SESSIONID,
LBACSYS.ORA_GET_AUDITED_LABEL( APPLICATION_CONTEXTS,'GENERIC_AUDIT_POL1') AS SESSION_LABEL1,
LBACSYS.ORA_GET_AUDITED_LABEL( APPLICATION_CONTEXTS,'GENERIC_AUDIT_POL2') AS SESSION_LABEL2
FROM UNIFIED_AUDIT_TRAIL;
/
ENTRY_ID SESSIONID SESSION_LABEL1 SESSION_LABEL2
-------- --------- -------------- --------------
1 1023 SECRET LEVEL_ALPHA
2 1024 TOP_SECRET LEVEL_BETA
See Also:
Oracle Label Security Administrator's Guide for more information about theORA_GET_AUDITED_LABEL functionAuditing Oracle Data Mining Events
You can use the CREATE AUDIT POLICY statement to audit Oracle Data Mining events.
Topics:
-
Oracle Data Mining Events That the Unified Audit Trail Captures
-
Example: Auditing Multiple Oracle Data Mining Operations by a User
-
Example: Auditing All Failed Oracle Data Mining Operations by a User
About Auditing Oracle Data Mining Events
As with all unified auditing, you must have the AUDIT_ADMIN role before you can audit Oracle Data Mining events.
To access the audit trail, query the UNIFIED_AUDIT_TRAIL data dictionary view.
See Also:
Oracle Data Mining Concepts for more information about Oracle Data MiningOracle Data Mining Events That the Unified Audit Trail Captures
Table 22-18 describes the audit events that you can capture for Oracle Data Mining.
Table 22-18 Oracle Data Mining Audit Events
| Audit Event | Description |
|---|---|
|
|
Generates an audit record for a Data Mining model |
|
|
Adds a comment to a Data Mining model |
|
|
Gives permission to a user to access the Data Mining model |
|
|
Changes the name of the Data Mining model |
|
|
Applies the Data Mining model or view its signature |
Configuring a Unified Audit Policy for Oracle Data Mining
To create a unified audit policy for Oracle Data Mining events, include the ACTIONS and ON MINING MODEL clauses in the CREATE AUDIT POLICY statement.
Example: Auditing Multiple Oracle Data Mining Operations by a User
Example 22-28 shows how to audit multiple Oracle Data Mining operations by user psmith. Include the ON MINING MODEL schema_name.model_name clause for each event, and separate each with a comma. This example specifies the same schema_name.model name for both actions, but the syntax enables you to specify different schema_name.model_name settings for different schemas and data models.
Example: Auditing All Failed Oracle Data Mining Operations by a User
Example 22-29 shows how to audit all failed Oracle Data Mining operations by user psmith.
How Oracle Data Mining Events Appear in the Audit Trail
If necessary, you should run the DBMS_AUDIT_MGMT.FLUSH_UNIFIIED_AUDIT_TRAIL procedure to write the audit records to disk.
EXEC DBMS_AUDIT_MGMT.FLUSH_UNIFIED_AUDIT_TRAIL;
See "Manually Flushing Audit Records to the Audit Trail in Queued-Write Mode" for more information.
The following example shows how to query the UNIFIED_AUDIT_TRAIL data dictionary view for Data Mining audit events.
SELECT DBUSERNAME, ACTION_NAME, SYSTEM_PRIVILEGE_USED, RETURN_CODE,
OBJECT_SCHEMA, OBJECT_NAME, SQL_TEXT
FROM UNIFIED_AUDIT_TRAIL;
DBUSERNAME ACTION_NAME SYSTEM_PRIVILEGE_USED RETURN_CODE
---------- -------------------- ------------------------- -----------
OBJECT_SCHEMA OBJECT_NAME
-------------------- --------------------
SQL_TEXT
--------------------------------------------------------------------------------
DMUSER1 CREATE MINING MODEL CREATE MINING MODEL 0
DMUSER1
BEGIN
dbms_data_mining.create_model(model_name => 'nb_model',
mining_function => dbms_data_mining.classification,
data_table_name => 'dm_data',
case_id_column_name => 'case_id',
target_column_name => 'target');
END;
DMUSER1 SELECT MINING MODEL 0
DMUSER1 NB_MODEL
select prediction(nb_model using *) from dual
DMUSER2 SELECT MINING MODEL 40284
DMUSER1 NB_MODEL
select prediction(dmuser1.nb_model using *) from dual
DMUSER1 ALTER MINING MODEL 0
DMUSER1 NB_MODEL
BEGIN dbms_data_mining.rename_model('nb_model', 'nb_model1'); END;
DMUSER2 ALTER MINING MODEL 40284
DMUSER1 NB_MODEL
BEGIN dbms_data_mining.rename_model('dmuser1.nb_model1', 'nb_model'); END;
DMUSER2 ALTER MINING MODEL 40284
DMUSER1 NB_MODEL
BEGIN dbms_data_mining.rename_model('dmuser1.nb_model1', 'nb_model'); END;
Auditing Oracle Data Pump Events
You can use the CREATE AUDIT POLICY statement to audit Oracle Data Pump.
Topics:
-
Oracle Data Pump Events That the Unified Audit Trail Captures
-
How Oracle Data Pump Audited Events Appear in the Audit Trail
About Auditing Oracle Data Pump Events
As with all unified auditing, you must have the AUDIT_ADMIN role before you can audit Oracle Data Pump events. To create Data Pump unified audit policies, you must set the CREATE AUDIT POLICY statement's COMPONENT clause to DATAPUMP. You can audit Data Pump export (expdp) and import (impdp) operations.
To access the audit trail, query the UNIFIED_AUDIT_TRAIL data dictionary view. The Data Pump-specific columns in this view begin with DP_.
See Also:
Oracle Database Utilities for detailed information about Oracle Data PumpOracle Data Pump Events That the Unified Audit Trail Captures
The unified audit trail captures information about both export (expdp) and import (impdp) operations.
Configuring a Unified Audit Policy for Oracle Data Pump
To create a unified audit policy for Oracle Data Pump events, include the ACTIONS COMPONENT clause in the CREATE AUDIT POLICY statement.
-
Use the following syntax to create a unified audit policy for Oracle Data Pump:
CREATE AUDIT POLICY policy_name ACTIONS COMPONENT=DATAPUMP { EXPORT | IMPORT | ALL };For example:
CREATE AUDIT POLICY audit_dp_export_pol ACTIONS COMPONENT=DATAPUMP EXPORT;
You can build more complex policies, such as those that include conditions. Remember that after you create the policy, you must use the AUDIT statement to enable it.
Example: Auditing Oracle Data Pump Import Operations
Example 22-30 shows how to audit all Oracle Data Pump import operations.
Example: Auditing All Oracle Data Pump Operations
Example 22-31 shows how to audit both Oracle Database Pump export and import operations.
How Oracle Data Pump Audited Events Appear in the Audit Trail
If necessary, you should run the DBMS_AUDIT_MGMT.FLUSH_UNIFIIED_AUDIT_TRAIL procedure to write the audit records to disk.
EXEC DBMS_AUDIT_MGMT.FLUSH_UNIFIED_AUDIT_TRAIL;
See "Manually Flushing Audit Records to the Audit Trail in Queued-Write Mode" for more information.
The DP_* columns of the UNIFIED_AUDIT_TRAIL view show Oracle Data Pump-specific audit data. For example:
SELECT DP_TEXT_PARAMETERS1, DP_BOOLEAN_PARAMETERS1 FROM UNIFIED_AUDIT_TRAIL WHERE AUDIT_TYPE = 'DATAPUMP'; DP_TEXT_PARAMETERS1 DP_BOOLEAN_PARAMETERS1 ---------------------------------------------- ---------------------------------- MASTER TABLE: "SCOTT"."SYS_EXPORT_TABLE_01", MASTER_ONLY: FALSE, JOB_TYPE: EXPORT, DATA_ONLY: FALSE, METADATA_JOB_MODE: TABLE_EXPORT, METADATA_ONLY: FALSE, JOB VERSION: 12.1.0.0, DUMPFILE_PRESENT: TRUE, ACCESS METHOD: DIRECT_PATH, JOB_RESTARTED: FALSE DATA OPTIONS: 0, DUMPER DIRECTORY: NULL REMOTE LINK: NULL, TABLE EXISTS: NULL, PARTITION OPTIONS: NONE
(This output was reformatted for easier readability.)
Auditing Oracle SQL*Loader Direct Load Path Events
You can use the CREATE AUDIT POLICY statement to audit Oracle SQL*Loader direct load path events.
Topics:
-
Oracle SQL*Loader Direct Load Path Events That the Unified Audit Trail Captures
-
Configuring a Unified Audit Trail Policy for Oracle SQL*Loader Direct Path Events
-
Example: Auditing Oracle SQL*Loader Direct Path Load Operations
-
How SQL*Loader Direct Path Load Audited Events Appear in the Audit Trail
About Auditing in Oracle SQL*Loader Direct Path Load Events
As with all unified auditing, you must have the AUDIT_ADMIN role before you can audit Oracle SQL*Loader direct path events.
To create SQL*Loader unified audit policies, you must set the CREATE AUDIT POLICY statement's COMPONENT clause to DIRECT_LOAD. You can audit direct path load operations only, not other SQL*Loader loads, such as conventional path loads.
To access the audit trail, query the DIRECT_PATH_NUM_COLUMNS_LOADED column in the UNIFIED_AUDIT_TRAIL data dictionary view.
See Also:
Oracle Database Utilities for detailed information about Oracle SQL*LoaderOracle SQL*Loader Direct Load Path Events That the Unified Audit Trail Captures
The unified audit trail captures information about direct path loads that SQL*Loader performs (that is, when you set direct=true on the SQL*Loader command line or in the SQL*Loader control file).
It also audits Oracle Call Interface (OCI) programs that use the direct path API.
See Also:
Oracle Database Utilities for detailed information about direct path loads in Oracle SQL*LoaderConfiguring a Unified Audit Trail Policy for Oracle SQL*Loader Direct Path Events
To create a unified audit policy that includes Oracle SQL*Loader direct path events, include the ACTIONS COMPONENT clause in the CREATE AUDIT POLICY statement.
-
Use the following syntax to create an Oracle SQL*Loader unified audit policy:
CREATE AUDIT POLICY policy_name ACTIONS COMPONENT=DIRECT_LOAD { LOAD };For example:
CREATE AUDIT POLICY audit_sqlldr_pol ACTIONS COMPONENT=DIRECT_LOAD LOAD;
You can build more complex policies, such as those that include conditions. Remember that after you create the policy, you must use the AUDIT statement to enable it.
Example: Auditing Oracle SQL*Loader Direct Path Load Operations
Example 22-30 shows how to audit SQL*Loader direct path load operations.
How SQL*Loader Direct Path Load Audited Events Appear in the Audit Trail
If necessary, you should run the DBMS_AUDIT_MGMT.FLUSH_UNIFIIED_AUDIT_TRAIL procedure to write the audit records to disk
See "Manually Flushing Audit Records to the Audit Trail in Queued-Write Mode" for more information.
The DIRECT_PATH_NUM_COLUMNS_LOADED column of the UNIFIED_AUDIT_TRAIL view shows the number of columns that were loaded using the SQL*Loader direct path load method. For example:
SELECT DBUSERNAME, ACTION_NAME, OBJECT_SCHEMA, OBJECT_NAME, DIRECT_PATH_NUM_COLUMNS_LOADED FROM UNIFIED_AUDIT_TRAIL WHERE AUDIT_TYPE = 'DIRECT PATH API'; DBUSERNAME ACTION_NAME OBJECT_SCHEMA OBJECT_NAME DIRECT_PATH_NUM_COLUMNS_LOADED ----------- ----------- ------------- ------------ ------------------------------ RLAYTON INSERT HR EMPLOYEES 4
Using the Unified Audit Policies or AUDIT Settings in a Multitenant Environment
In a multitenant environment, you can create unified audit policies in both the root and in PDBs.
Topics:
-
Configuring a Local Unified Audit Policy or Common Unified Audit Policy
-
How Local or Common Audit Policies or Settings Appear in the Audit Trail
See Also:
Oracle Database Concepts for information about the common audit configurations in a multitenant environmentAbout Local and Common Audit Policies
For both unified audit policies and the AUDIT and NOAUDIT SQL statements, if you are using a multitenant environment, then you can set the audit policy to be either a local audit policy or a common audit policy.
-
Local audit policy. This type of policy can exist in either the root or the PDB. A local audit policy that exists in the root can contain object audit options for both local and common objects. Both local and common users who have been granted the
AUDIT_ADMINrole can enable local policies: local users from their PDBs and common users from the root or the PDB to which they have privileges. If you are connected to the root, then you can specify object audit options but not privilege or role audit options. -
Common audit policy. This type of policy is available to all PDBs in the multitenant environment. Only common users who have been granted the AUDIT_ADMIN role can create and maintain common audit policies. You can enable common audit policies only for common users. You must create common audit policies only in the root. This type of policy can contain object audit options of only common objects, and be enabled only for common users.
By default, audit policies are local to the current PDB.
Configuring a Local Unified Audit Policy or Common Unified Audit Policy
To create a local or common unified audit policy, include the CONTAINER clause in the CREATE AUDIT POLICY statement.
-
Use the following syntax to create a local or common unified audit policy:
CREATE AUDIT POLICY policy_name action1 [,action2 ] [CONTAINER = {CURRENT | ALL}];
In this specification:
-
CURRENTsets the audit policy to be local to the current PDB. -
ALLmakes the audit policy a common audit policy, that is, available to the entire multitenant environment.
For example, for a common unified audit policy:
CREATE AUDIT POLICY dict_updates ACTIONS UPDATE ON SYS.USER$, DELETE ON SYS.USER$, UPDATE ON SYS.LINK$, DELETE ON SYS.LINK$ CONTAINER = ALL;
-
Note the following:
-
For unified audit policies, you can set the
CONTAINERclause for theCREATE AUDIT POLICYstatement but not forALTER AUDIT POLICYorDROP AUDIT POLICY. If you want to change the scope of an existing unified audit policy to use this setting, then you must drop and recreate the policy. -
For
AUDITstatements, you can set theCONTAINERclause for audit settings only if you have an Oracle database that has not been migrated to the Release 12.x audit features. You cannot use theCONTAINERclause in anAUDITstatement that is used to enable a unified audit policy. -
You can set the
CONTAINERclause toCURRENTonly from a PDB. If you omit this setting while in the PDB, then the default isCONTAINER = CURRENT. -
You can set the
CONTAINERclause toALLonly from the root. If you omit this setting while in the root, then the default isCONTAINER = ALL. -
For objects:
-
Common audit policies can have common objects only and local audit policies can have local objects only.
-
You cannot set
CONTAINERtoALLif the objects involved are local. They must be common objects.
-
-
For privileges:
-
You can set the
CONTAINERtoCURRENT(or omit theCONTAINERclause) if the user accounts involved are a mixture of local and common accounts. This creates a local audit configuration that applies only to the current PDB. -
You cannot set
CONTAINERtoALLif the users involved are local users. They must be common users. -
If you set
CONTAINERtoALLand do not specify a user list (using theBYclause in theAUDITstatement), then the configuration applies to all common users in each PDB.
-
Example: Local Unified Audit Policy
Example 22-33 shows a local unified audit policy that has been created by the common user c##sec_admin from a PDB and applied to common user c##hr_admin.
Example: Common Unified Audit Policy
Example 22-34 shows a common unified audit policy that has been created by the common user c##sec_admin from the root and applied to common user c##hr_admin.
How Local or Common Audit Policies or Settings Appear in the Audit Trail
When you want to query the dynamic and data dictionary views for the results of an audit policy, you can query the view from either the root or the PDB in which the action occurred, as follows:
-
Audit records from all PDBs. The audit trail reflects audited actions that have been performed in the PDBs. For example, if user
lbrowninPDB1performs an action that has been audited by either a common or a local audit policy, then the audit trail will capture this action. TheDBIDcolumn in theUNIFIED_AUDIT_TRAILdata dictionary view indicates the PDB in which the audited action takes place and to which the policy applies. If you want to see audit records from all PDBs, you should query theCDB_UNIFIED_AUDIT_TRAILdata dictionary view from the root. -
Audit records from common audit policies. This location is where the common audit policy results in an audit record. The audit record can be generated anywhere in the multitenant environment—the root or the PDBs, depending on where the action really occurred. For example, the common audit policy
fga_polaudits theEXECUTEprivilege on theDBMS_FGAPL/SQL package, and if this action occurs inPDB1, then the audit record is generated inPDB1and not in the root. Hence, the audit record can be seen in PDB1.However, be aware that if you want to include the name of the common audit policy in a
WHEREclause (for example,WHERE UNIFIED_AUDIT_POLICIES = 'FGA_POL') in aUNIFIED_AUDIT_TRAILview query, you must perform the query for the policy name from the root. This is because the common policy itself is only visible in the root, not the PDB.
The following example shows how to find the results of a common unified audit policy:
CONNECT c##sec_admin@root Enter password: password Connected. SELECT DBID, ACTION_NAME, OBJECT_SCHEMA, OBJECT_NAME FROM CDB_UNIFIED_AUDIT_TRAIL WHERE DBUSERNAME = 'c##hr_admin'; DBID ACTION_NAME OBJECT_SCHEMA OBJECT_NAME ----------- ----------- ------------- ----------- 653916017 UPDATE HR EMPLOYEES 653916018 UPDATE HR JOB_HISTORY 653916017 UPDATE HR JOBS
Note:
To view the latest audit records in the audit trail, if necessary, run the following procedure to write the records to disk:EXEC DBMS_AUDIT_MGMT.FLUSH_UNIFIED_AUDIT_TRAIL;
See "Manually Flushing Audit Records to the Audit Trail in Queued-Write Mode" for more information.
Altering Unified Audit Policies
You can use the ALTER AUDIT POLICY statement to modify a unified audit policy.
Topics:
-
Example: Altering an Oracle Label Security Component in a Unified Audit Policy
-
Example: Altering an Oracle Label Security Component in a Unified Audit Policy
About Altering Unified Audit Policies
You can change most properties in a unified audit policy, except for its CONTAINER setting. You cannot alter unified audit policies in a multitenant environment. For example, you cannot turn a common unified audit policy into a local unified audit policy.
To find existing unified audit policies, query the AUDIT_UNIFIED_POLICIES data dictionary view. If you want to find only the enabled unified audit policies, then query the AUDIT_UNIFIED_ENABLED_POLICIES view. You can alter both enabled and disabled audit policies. If you alter an enabled audit policy, it remains enabled after you alter it.
After you alter an object unified audit policy, the new audit settings take place immediately, for both the active and subsequent user sessions. If you alter system audit options, or audit conditions of the policy, then they are activated for new user sessions, but not the current user session.
Altering a Unified Audit Policy
To alter a unified audit policy, you must use the ALTER AUDIT POLICY statement.
-
Use the syntax in Example 22-35 to alter a unified audit policy, you use the
ALTER AUDIT POLICYstatement.
Example 22-35 Syntax for the ALTER AUDIT POLICY Statement
ALTER AUDIT POLICY policy_name [ADD [privilege_audit_clause][action_audit_clause] [role_audit_clause]] [DROP [privilege_audit_clause][action_audit_clause] [role_audit_clause]] [CONDITION {DROP | audit_condition EVALUATE PER {STATEMENT|SESSION|INSTANCE}}]
In this specification:
-
ADDenables you to alter the following the following settings:-
privilege_audit_clausedescribes privilege-related audit options. See "Auditing System Privileges" for details. The detailed syntax for configuring privilege audit options is as follows:ADD privilege_audit_clause := PRIVILEGES privilege1 [, privilege2]
-
action_audit_clauseandstandard_actionsdescribe object action-related audit options. See "Auditing Object Actions". The syntax is as follows:ADD action_audit_clause := {standard_actions | component_actions} [, component_actions ] standard_actions := ACTIONS action1 [ ON {schema.obj_name | DIRECTORY directory_name | MINING MODEL schema.obj_name } ] [, action2 [ ON {schema.obj_name | DIRECTORY directory_name | MINING MODEL schema.obj_name } ]
-
role_audit_clauseenables you to add or drop the policy for roles. See "Auditing Roles". The syntax is:ADD role_audit_clause := ROLES role1 [, role2]
-
-
DROPenables you to drop the same components that are described for theADDclause. For example:DROP role_audit_clause := ROLES role1 [, role2]
-
CONDITION {DROP...enables you to add or drop a condition for the policy. If you are altering an existing condition, then you must include theEVALUATE PERclause with the condition. See "Creating a Condition for a Unified Audit Policy". The syntax is:CONDITION 'audit_condition := function operation value_list' EVALUATE PER {STATEMENT|SESSION|INSTANCE}
If you want to drop a condition, then omit the condition definition and the
EVALUATE PERclause. For example:CONDITION DROP
Example: Altering a Condition in a Unified Audit Policy
Example 22-36 shows how to change a condition in an existing unified audit policy.
Example: Altering an Oracle Label Security Component in a Unified Audit Policy
Example 22-37 shows how to alter an Oracle Label Security component in an audit policy.
Example: Altering Roles in a Unified Audit Policy
Example 22-38 shows how to add roles to a common unified audit policy.
Example: Dropping a Condition from a Unified Audit Policy
Example 22-39 shows how to drop a condition from an existing unified audit policy.
Enabling and Applying Unified Audit Policies to Users
You can use the AUDIT POLICY statement to enable and apply unified audit policies to both users and roles.
Topics:
About Enabling Unified Audit Policies
To enable a unified audit policy, you must use the AUDIT statement with the POLICY clause. This applies for all types of audit options, including object-level options.
The policy does not take effect until after the audited users log into the database instance. In other words, if you create and enable a policy while the audited users are logged in, then the policy cannot collect audit data; the users must log out and then log in again before auditing can begin. Once the session is set up with auditing for it, then the setting lasts as long as the user session and then ends when the session ends.
You can check the results of the audit by querying the UNIFIED_AUDIT_TRAIL data dictionary view. To find a list of existing unified audit policies, query the AUDIT_UNIFIED_POLICIES data dictionary view.
The AUDIT statement lets you specify the following optional additional settings:
-
Whether to apply the unified audit policy to one or more users. To apply the policy to one or more users, including administrative users who log in with the
SYSDBAadministrative privilege (such asSYS), use theBYclause.For example:
AUDIT POLICY role_connect_audit_pol BY SYS, SYSTEM;
-
Whether to exclude users from the unified audit policy. To exclude users from the audit policy, include the
EXCEPTclause.For example:
AUDIT POLICY role_connect_audit_pol EXCEPT rlee, jrandolph;
-
Whether to create an audit record if the activity succeeds or fails. This method of auditing reduces the audit trail, helping you to focus on specific actions. This can aid in maintaining good database performance. Enter one of the following clauses:
-
WHENEVER SUCCESSFULaudits only successful executions of the user's activity. -
WHENEVER NOT SUCCESSFULaudits only failed executions of the user's activity. Monitoring unsuccessful SQL statement can expose users who are snooping or acting maliciously, though most unsuccessful SQL statements are neither.
For example:
AUDIT POLICY role_connect_audit_pol WHENEVER NOT SUCCESSFUL;
If you omit this clause, then both failed and successful user activities are written to the audit trail.
-
Note the following:
-
The unified audit policy only can have either the
BYclause or theEXCEPTclause, but not both for the same policy. -
If you run multiple
AUDITstatements on the same unified audit policy but specify differentBYusers, then Oracle Database audits all of these users. -
If you run multiple
AUDITstatements on the same unified audit policy but specify differentEXCEPTusers, then Oracle Database uses the last exception user list, not any of the users from the preceding lists. This means the effect of the earlierAUDIT POLICY ... EXCEPTstatements are overridden by the latestAUDIT POLICY ... EXCEPTstatement. -
You can only enable common unified audit policies for common users.
-
In a multitenant environment, you can enable a common audit policy only from the root and a local audit policy only from the PDB to which it applies.
Enabling a Unified Audit Policy
To enable a unified audit policy, you must use the AUDIT POLICY statement.
-
Use the following syntax to enable a unified audit policy:
AUDIT POLICY { policy_auditing } [WHENEVER [NOT] SUCCESSFUL]In this specification:
-
policy_auditingrefers to the following components:-
The name of the unified audit policy. To find all existing policies, query the
AUDIT_UNIFIED_POLICIESdata dictionary view. To find currently enabled policies, queryAUDIT_UNIFIED_ENABLED_POLICIES. -
Users to whom the unified audit policy applies. To apply the policy to one or more users (including user
SYS), enter theBYclause. For example:BY psmith, rlee
-
Users to exclude from the unified audit policy. To exclude one or more users from the policy, enter the
EXCEPTclause. For example:EXCEPT psmith, rlee
Mandatory audit records are captured in the
UNIFIED_AUDIT_TRAILdata dictionary view for theAUDIT POLICYSQL statement. To find users who have been excluded in the audit records, you can query theEXCLUDED_USERcolumn in theUNIFIED_AUDIT_TRAILview to list the excluded users.
You cannot enable the same audit policy with the
BY,BY USERS WITH GRANTED ROLES, andEXCEPTclauses in the same statement. This action throws an error for the subsequentAUDITstatement with the conflicting clause. -
-
WHENEVER [NOT] SUCCESSFULenables the policy to generate audit records based on whether the user's actions failed or succeeded. See "About Enabling Unified Audit Policies" for more information.
-
Example 22-40 shows how to enable a unified audit policy to record only failed actions by the user dv_admin.
Example 22-40 Enabling a Unified Audit Policy
AUDIT POLICY dv_admin_pol BY tjones WHENEVER NOT SUCCESSFUL;
After you enable the unified audit policy and it is generating records, you can find the audit records by querying the UNIFIED_AUDIT_TRAIL data dictionary view.
Disabling Unified Audit Policies
You can use the NOAUDIT POLICY statement to disable a unified audit policy.
Topics:
About Disabling Unified Audit Policies
The NOAUDIT statement with the POLICY clause enables you to disable a unified audit policy.
In the NOAUDIT statement, you can specify a BY user list, but not an EXCEPT user list. The disablement of a unified audit policy takes effect on subsequent user sessions.
You can find a list of existing unified audit policies by querying the AUDIT_UNIFIED_POLICIES data dictionary view.
In a multitenant environment, you can disable a common audit policy only from the root and a local audit policy only from the PDB to which it applies.
Disabling a Unified Audit Policy
To disable a unified audit policy, use the NOAUDIT statement.
-
Use the following syntax to disable a unified audit policy:
NOAUDIT POLICY {policy_auditing | existing_audit_options};In this specification:
-
policy_auditingis the name of the policy. To find all currently enabled policies, query theAUDIT_UNIFIED_ENABLED_POLICIESdata dictionary view. As part of this specification, you optionally can include theBYclause, but not theEXCEPTclause. See "About Enabling Unified Audit Policies" for more information. -
existing_audit_optionsrefers toAUDIToptions that were available in releases earlier than Oracle Database 12c Release 1 (12.1), such as the following:-
SELECT ANY TABLE, UPDATE ANY TABLE BY SCOTT, HR -
UPDATE ON SCOTT.EMP
-
-
Example 22-41 shows how to disable a unified audit policy for a user.
Dropping Unified Audit Policies
You can use the DROP AUDIT POLICY statement to drop a unified audit policy.
Topics:
About Dropping Unified Audit Policies
To drop a unified audit policy, you must first disable it, and then run the DROP AUDIT POLICY statement to remove it.
If a unified audit policy is already enabled for a session, the effect of dropping the policy is not seen by this existing session. Until that time, the unified audit policy's settings remain in effect. For object-related unified audit policies, however, the effect is immediate.
You can find a list of existing unified audit policies by querying the AUDIT_UNIFIED_POLICIES data dictionary view.
When you disable an audit policy before dropping it, ensure that you disable it using the same settings that you used to enable it. For example, suppose you enabled the logon_pol policy as follows:
AUDIT POLICY logon_pol BY HR, OE;
Before you can drop it, your NOAUDIT statement must include the HR and OE users as follows:
NOAUDIT POLICY logon_pol BY HR, OE;
In a multitenant environment, you can drop a common audit policy only from the root and a local audit policy only from the PDB to which it applies.
Dropping a Unified Audit Policy
To drop a unified audit policy, you must use the DROP AUDIT POLICY statement.
-
Use the following the following syntax to drop a unified audit policy:
DROP AUDIT POLICY policy_name;
Example 22-42 shows how to disable and drop a common unified audit policy.
Example 22-42 Disabling and Dropping a Unified Audit Policy
CONNECT c##sec_admin@root
Enter password: password
Connected.
NOAUDIT POLICY dv_admin_pol;
DROP AUDIT POLICY dv_admin_pol
In a multitenant environment, the unified audit policy drop applies to the current PDB. If the unified audit policy was created as a common unified audit policy, then you cannot drop it from the local PDB. See "Using the Unified Audit Policies or AUDIT Settings in a Multitenant Environment" for more information about common unified audit policies.
Tutorial: Auditing Nondatabase Users
This tutorial shows how to create a unified audit policy that audits a nondatabase user's actions, based on the identity set in the client identifier. If you are using a multitenant environment, then this tutorial applies to the current PDB only.
Topics:
Step 1: Create the User Accounts and Ensure the User OE Is Active
You must first create users and ensure that the user OE is active.
-
Log on as user
SYSwith theSYSDBAadministrative privilege.sqlplus sys as sysdba Enter password: password -
In a multitenant environment, connect to the appropriate PDB.
For example:
CONNECT SYS@hrpdb AS SYSDBA Enter password: passwordTo find the available PDBs, query the
DBA_PDBSdata dictionary view. To check the current PDB, run theshow con_namecommand. -
Create the local user
policy_admin, who will create the fine-grained audit policy.CREATE USER policy_admin IDENTIFIED BY password; GRANT CREATE SESSION, AUDIT_ADMIN TO policy_admin;Replace
passwordwith a password that is secure. See "Minimum Requirements for Passwords" for more information. -
Create the local user account
auditor, who will check the audit trail for this policy.CREATE USER policy_auditor IDENTIFIED BY password; GRANT CREATE SESSION, AUDIT_VIEWER TO policy_auditor; -
The sample user
OEwill also be used in this tutorial, so query theDBA_USERSdata dictionary view to ensure thatOEis not locked or expired.SELECT USERNAME, ACCOUNT_STATUS FROM DBA_USERS WHERE USERNAME = 'OE';
If the
DBA_USERSview lists userOEas locked and expired, log in as userSYSTEMand then enter the following statement to unlock theOEaccount and create a new password:ALTER USER OE ACCOUNT UNLOCK IDENTIFIED BY password;Enter a password that is secure. For greater security, do not give the
OEaccount the same password from previous releases of Oracle Database. "Minimum Requirements for Passwords" for the minimum requirements for creating passwords.
Step 2: Create the Unified Audit Policy
After you have created the users and enabled OE, you are ready to create the unified audit policy.
-
Connect to SQL*Plus as user
policy_admin.CONNECT policy_admin -- Or, CONNECT policy_admin@hrpdb Enter password: password
-
CREATE AUDIT POLICY orders_unified_audpol ACTIONS INSERT ON OE.ORDERS, UPDATE ON OE.ORDERS, DELETE ON OE.ORDERS, SELECT ON OE.ORDERS WHEN 'SYS_CONTEXT(''USERENV'', ''CLIENT_IDENTIFIER'') = ''robert''' EVALUATE PER STATEMENT; AUDIT POLICY orders_unified_audpol;In this example, the
AUDIT_CONDITIONparameter assumes that the nondatabase user is namedrobert. The policy will monitor anyINSERT,UPDATE,DELETE, andSELECTstatements thatrobertwill attempt. Remember that the user'sCLIENT_IDENTITIFERsetting that you enter in the policy is case sensitive and that the policy only recognizes the case used for the identity that you specify here. In other words, later on, if the user session is set toRobertorROBERT, the policy's condition will not be satisfied.
Step 3: Test the Policy
A unified auditing policy takes effect in the next user session for the users who are being audited. So, before their audit records can be captured, the users must connect to the database after the policy has been created.
-
Connect as user
OEand select from theOE.ORDERStable.CONNECT OE -- Or, CONNECT OE@hrpdb Enter password: password SELECT COUNT(*) FROM ORDERS;
The following output appears:
COUNT(*) ---------- 105 -
Connect as user
policy_adminand if necessary, run the following procedure.CONNECT policy_admin -- Or, CONNECT policy_admin@hrpdb Enter password: password EXEC DBMS_AUDIT_MGMT.FLUSH_UNIFIED_AUDIT_TRAIL;
If the audit trail mode is
QUEUED, then audit records are not written to disk until the in-memory queues are full. This command explicitly flushes the queues to disk, so that you can see the audit trail records in theUNIFIED_AUDIT_TRAILview. -
Connect as user
policy_auditorand then check if any audit records were generated.CONNECT policy_auditor -- Or, CONNECT policy_auditor@hrpdb Enter password: password col dbusername format a10 col client_identifier format a20 col sql_text format a29 SELECT DBUSERNAME, CLIENT_IDENTIFIER, SQL_TEXT FROM UNIFIED_AUDIT_TRAIL WHERE SQL_TEXT LIKE '%FROM ORDERS%';
The following output appears:
no rows selected
-
Reconnect as user
OE, set the client identifier torobert, and then reselect from theOE.ORDERStable.CONNECT OE -- Or, CONNECT OE@hrpdb Enter password: password EXEC DBMS_SESSION.SET_IDENTIFIER('robert'); SELECT COUNT(*) FROM ORDERS;
The following output should appear:
COUNT(*) ---------- 105 -
Connect as user
policy_adminand run theDBMS_AUDIT_MGMT.FLUSH_UNIFIED_AUDIT_TRAILprocedure.CONNECT policy_admin -- Or, CONNECT policy_admin@hrpdb Enter password: password EXEC DBMS_AUDIT_MGMT.FLUSH_UNIFIED_AUDIT_TRAIL;
-
Reconnect as user
auditorand then check the audit trail again.CONNECT policy_auditor -- Or, CONNECT policy_auditor@hrpdb Enter password: password SELECT DBUSERNAME, CLIENT_IDENTIFIER, SQL_TEXT FROM UNIFIED_AUDIT_TRAIL WHERE SQL_TEXT LIKE '%FROM ORDERS%';
This time, because
roberthas made his appearance and queried theOE.ORDERStable, the audit trail captures his actions:DBUSERNAME CLIENT_IDENTIFIER SQL_TEXT ---------- ----------------- ---------------------------- OE robert SELECT COUNT(*) FROM ORDERS;
Step 4: Remove the Components of This Tutorial
If you no longer need the components of this tutorial, then you can remove them.
-
Connect to SQL*Plus as user
policy_admin, and then manually disable and drop theorders_unified_audpolpolicy.CONNECT policy_admin -- Or, CONNECT policy_admin@hrpdb Enter password: password NOAUDIT POLICY orders_unified_audpol; DROP AUDIT policy orders_unified_audpol;
(Unified audit policies reside in the
SYSschema, not the schema of the user who created them.) -
Connect to SQL*Plus as user
SYSTEM.CONNECT SYSTEM -- Or, CONNECT SYSTEM@hrpdb Enter password: password
-
Drop users
policy_adminandpolicy_auditor.DROP USER policy_admin; DROP USER policy_auditor;
-
If you want, lock and expire
OE, unless other users want to use this account:ALTER USER OE PASSWORD EXPIRE ACCOUNT LOCK;
Auditing Activities with the Predefined Unified Audit Policies
Oracle Database provides five predefined unified audit policies, which cover commonly used security-relevant audit settings.
Topics:
-
Oracle Database Parameter Changes Predefined Unified Audit Policy
-
User Account and Privilege Management Predefined Unified Audit Policy
-
Center for Internet Security Recommendations Predefined Unified Audit Policy
-
Oracle Database Real Application Security Predfined Audit Policies
See Also:
"Auditing Commonly Used Security-Relevant Activities" for general steps for performing this type of auditingLogon Failures Predefined Unified Audit Policy
The ORA_LOGON_FAILURES unified audit policy tracks failed logons only. It does not track any other kinds of logons. By default, this policy is not enabled.
Example 22-43 shows the ORA_LOGON_FAILURES unified audit policy definition.
Example 22-43 ORA_LOGON_FAILURES Predefined Unified Audit Policy Setting
CREATE AUDIT POLICY ORA_LOGON_FAILURES ACTIONS LOGON;
You should enable the ORA_LOGON_FAILURES unified audit policy as follows:
AUDIT POLICY ORA_LOGON_FAILURES WHENEVER NOT SUCCESSFUL;
Secure Options Predefined Unified Audit Policy
The ORA_SECURECONFIG unified audit policy provides all the secure configuration audit options. This policy is enabled by default for both pure unified auditing and mixed-mode auditing environments. By default, this policy is not enabled.
Example 22-44 shows the ORA_SECURECONFIG unified audit policy definition.
Example 22-44 ORA_SECURECONFIG Predefined Unified Audit Policy Settings
CREATE AUDIT POLICY ORA_SECURECONFIG
PRIVILEGES ALTER ANY TABLE, CREATE ANY TABLE, DROP ANY TABLE,
CREATE ANY PROCEDURE, DROP ANY PROCEDURE, ALTER ANY PROCEDURE,
GRANT ANY PRIVILEGE, GRANT ANY OBJECT PRIVILEGE, GRANT ANY ROLE,
AUDIT SYSTEM, CREATE EXTERNAL JOB, CREATE ANY JOB,
CREATE ANY LIBRARY,
EXEMPT ACCESS POLICY,
CREATE USER, DROP USER,
ALTER DATABASE, ALTER SYSTEM,
CREATE PUBLIC SYNONYM, DROP PUBLIC SYNONYM,
CREATE SQL TRANSLATION PROFILE, CREATE ANY SQL TRANSLATION PROFILE,
DROP ANY SQL TRANSLATION PROFILE, ALTER ANY SQL TRANSLATION PROFILE,
TRANSLATE ANY SQL,
EXEMPT REDACTION POLICY,
PURGE DBA_RECYCLEBIN, LOGMINING,
ADMINISTER KEY MANAGEMENT
ACTIONS ALTER USER, CREATE ROLE, ALTER ROLE, DROP ROLE,
SET ROLE, CREATE PROFILE, ALTER PROFILE,
DROP PROFILE, CREATE DATABASE LINK,
ALTER DATABASE LINK, DROP DATABASE LINK,
CREATE DIRECTORY, DROP DIRECTORY,
CREATE PLUGGABLE DATABASE,
DROP PLUGGABLE DATABASE,
ALTER PLUGGABLE DATABASE,
EXECUTE ON DBMS_RLS;
See Also:
Oracle Database SQL Language Reference for detailed information about the SQL statements described in this sectionOracle Database Parameter Changes Predefined Unified Audit Policy
The ORA_DATABASE_PARAMETER policy audits commonly used Oracle Database parameter settings. By default, this policy is not enabled.
Example 22-45 shows the ORA_DATABASE_PARAMETER unified audit policy definition.
User Account and Privilege Management Predefined Unified Audit Policy
The ORA_ACCOUNT_MGMT policy audits commonly used user account and privilege settings. By default, this policy is not enabled.
Example 22-46 shows the ORA_ACCOUNT_MGMT unified audit policy definition.
Center for Internet Security Recommendations Predefined Unified Audit Policy
The ORA_CIS_RECOMMENDATIONS policy performs audits that are recommended by the Center for Internet Security (CIS). By default, this policy is not enabled.
Example 22-47 shows the ORA_CIS_RECOMMENDATIONS unified audit policy definition.
Example 22-47 ORA_CIS_RECOMMENDATIONS Predefined Unified Audit Policy Settings
CREATE AUDIT POLICY ORA_CIS_RECOMMENDATIONS
PRIVILEGES SELECT ANY DICTIONARY, CREATE ANY LIBRARY,
DROP ANY LIBRARY, CREATE ANY TRIGGER,
ALTER ANY TRIGGER, DROP ANY TRIGGER,
ALTER SYSTEM
ACTIONS CREATE USER, ALTER USER, DROP USER,
CREATE ROLE, DROP ROLE, ALTER ROLE,
GRANT, REVOKE, CREATE DATABASE LINK,
ALTER DATABASE LINK, DROP DATABASE LINK,
CREATE PROFILE, ALTER PROFILE, DROP PROFILE,
CREATE SYNONYM, DROP SYNONYM,
CREATE PROCEDURE, DROP PROCEDURE, ALTER PROCEDURE;
Oracle Database Real Application Security Predfined Audit Policies
You can use predefined unified audit policies for Oracle Database Real Application Security events. By default, these policies are not enabled. See "Enabling and Applying Unified Audit Policies to Users" for more information.
Topics:
System Administrator Operations Predefined Unified Audit Policy
The ORA_RAS_POLICY_MGMT predefined unified audit policy audits policies for all Oracle Real Application Security administrative actions on application users, roles, and policies.
Example 22-48 describes the ORA_RAS_POLICY_MGMT audit policy.
Example 22-48 ORA_RAS_POLICY_MGMT Predefined Unified Audit Policy
CREATE AUDIT POLICY ORA_RAS_POLICY_MGMT ACTIONS COMPONENT=XS CREATE USER, UPDATE USER, DELETE USER, CREATE ROLE, UPDATE ROLE, DELETE ROLE, GRANT ROLE, REVOKE ROLE, ADD PROXY, REMOVE PROXY, SET USER PASSWORD, SET USER VERIFIER, SET USER PROFILE, CREATE ROLESET, UPDATE ROLESET, DELETE ROLESET, CREATE SECURITY CLASS, UPDATE SECURITY CLASS, DELETE SECURITY CLASS, CREATE NAMESPACE TEMPLATE, UPDATE NAMESPACE TEMPLATE, DELETE NAMESPACE TEMPLATE, CREATE ACL, UPDATE ACL, DELETE ACL, CREATE DATA SECURITY, UPDATE DATA SECURITY, DELETE DATA SECURITY, ENABLE DATA SECURITY, DISABLE DATA SECURITY, ADD GLOBAL CALLBACK, DELETE GLOBAL CALLBACK, ENABLE GLOBAL CALLBACK;
Session Operations Predefined Unified Audit Policy
The ORA_RAS_SESSION_MGMT predefined unified audit policy audits policies for all run-time Oracle Real Application Security session actions and namespace actions.
Example 22-49 describes the ORA_RAS_SESSION_MGMT policy.
Example 22-49 ORA_RAS_SESSION_MGMT Predefined Unified Audit Policy
CREATE AUDIT POLICY ORA_RAS_SESSION_MGMT ACTIONS COMPONENT=XS CREATE SESSION, DESTROY SESSION, ENABLE ROLE, DISABLE ROLE, SET COOKIE, SET INACTIVE TIMEOUT, SWITCH USER, ASSIGN USER, CREATE SESSION NAMESPACE, DELETE SESSION NAMESPACE, CREATE NAMESPACE ATTRIBUTE, GET NAMESPACE ATTRIBUTE, SET NAMESPACE ATTRIBUTE, DELETE NAMESPACE ATTRIBUTE;
Oracle Database Vault Predefined Unified Audit Policy
The ORA_DV_AUDPOL policy audits all actions that are performed on the Oracle Database Vault DVSYS and DVF schema objects and the Oracle Label Security LBACSYS schema objects. It does not capture actions on the F$* factor functions in the DVF schema. By default, this policy is not enabled.
Example 22-50 shows the ORA_DV_AUDPOL unified audit policy definition.
Example 22-50 ORA_DV_AUDPOL Predefined Unified Audit Policy
CREATE AUDIT POLICY ORA_DV_AUDPOL ACTIONS AUDIT ON DVF.DBMS_MACSEC_FUNCTION';
See Also:
"Auditing Oracle Database Vault Events"Auditing Specific Activities with Fine-Grained Auditing
Fine-grained auditing enables you to create audit policies at the granular level. You cannot create unified audit policies using fine-grained auditing but you can create very customized audit settings, such as auditing the times that data is accessed.
Topics:
-
Using Fine-Grained Auditing on Tables or Views That Have Oracle VPD Policies
-
Using the DBMS_FGA PL/SQL Package to Manage Fine-Grained Audit Policies
-
Tutorial: Adding an Email Alert to a Fine-Grained Audit Policy
See Also:
"Auditing Specific, Fine-Grained Activities" for general steps for performing this type of auditingAbout Fine-Grained Auditing
Fine-grained auditing enables you to create policies that define specific conditions that must take place for the audit to occur.
This enables you to monitor data access based on content. It provides granular auditing of queries, and INSERT, UPDATE, and DELETE operations. You can use fine-grained auditing to audit the following types of actions:
-
Accessing a table between 9 p.m. and 6 a.m. or on Saturday and Sunday
-
Using an IP address from outside the corporate network
-
Selecting or updating a table column
-
Modifying a value in a table column
In general, fine-grained audit policies are based on simple, user-defined SQL predicates on table objects as conditions for selective auditing. During fetching, whenever policy conditions are met for a row, the query is audited.
The audit policies described in "Auditing Activities with Unified Audit Policies and the AUDIT Statement" can perform most of the operations that fine-grained audit policies can perform, except for the following actions:
-
Auditing specific columns. You can audit specific relevant columns that hold sensitive information, such as salaries or Social Security numbers.
-
Using event handlers. For example, you can write a function that sends an email alert to a security administrator when an audited column that should not be changed at midnight is updated.
Note:
-
Fine-grained auditing is supported only with cost-based optimization. For queries using rule-based optimization, fine-grained auditing checks before applying row filtering, which could result in an unnecessary audit event trigger.
-
Policies currently in force on an object involved in a flashback query are applied to the data returned from the specified flashback snapshot based on time or system change number (SCN).
-
If you want to use fine-grained auditing to audit data that is being directly loaded (for example, using Oracle Warehouse Builder to execute DML statements), then Oracle Database transparently makes all direct loads that are performed in the database instance into conventional loads. If you want to preserve the direct loading of data, consider using unified audit policies instead.
Where Are Fine-Grained Audit Records Stored?
Fine-grained auditing records are stored in the AUDSYS schema. These audit records are stored in the SYSAUX tablespace by default.
You can supply a new tablespace by using the DBMS_AUDIT_MGMT.SET_AUDIT_TRAIL_LOCATION procedure. (For more information about this procedure, see Oracle Database PL/SQL Packages and Types Reference.) To find the records have been generated for the audit policies that are in effect, you can query UNIFIED_AUDIT_TRAIL data dictionary view. For detailed information about this view, see Oracle Database Reference.
The audit trail captures an audit record for each reference of a table or a view within a SQL statement. For example, if you run a UNION statement that references the HR.EMPLOYEES table twice, then an audit policy for statement generates two audit records, one for each access of the HR.EMPLOYEES table.
Who Can Perform Fine-Grained Auditing?
You must be granted the AUDIT_ADMIN role to create fine-grained audit policies, and the AUDIT_VIEWER role to analyze and audit data.
The EXECUTE privilege on the DBMS_FGA PL/SQL package is already granted to AUDIT_ADMIN role.
Using Fine-Grained Auditing on Tables or Views That Have Oracle VPD Policies
If the table or view that you want to audit using a fine-grained audit policy is included in an Oracle Virtual Private Database policy, then the audit trail will capture the VPD predicate, similar to how it captures the predicate for unified audit policies.
The predicate information is stored in the RLS_INFO column of the following data dictionary views:
-
UNIFIED_AUDIT_TRAIL -
DBA_AUDIT_TRAIL -
V$XML_AUDIT_TRAIL -
DBA_FGA_AUDIT_TRAIL
If there are multiple VPD policies applied to the same table or view, then by default the predicates for these policies are concatenated in the RLS_INFO column. You can reformat the output so that each predicate is in its own row (identified by its corresponding VPD policy name and other information) by using the ORA_GET_RLS_PREDICATE function.
Using Fine-Grained Auditing in a Multitenant Environment
You can create fine-grained audit policies in the root or in PDBs.
Note the following:
-
You cannot create policies on
SYSobjects. -
When you create a policy in the root, the policy cannot be applied to all PDBs; it only applies to objects within the root. (In other words, there is no such thing as a common fine-grained audit policy.)
-
When you create a policy in a PDB, it applies only to objects within the PDB.
Using Fine-Grained Audit Policies with Editions
You can prepare an application for edition-based redefinition, and cover each table that the application uses with an editioning view.
If you do this, then you must move the fine-grained audit polices that protect these tables to the editioning view.
Using the DBMS_FGA PL/SQL Package to Manage Fine-Grained Audit Policies
The DBMS_FGA PL/SQL package enables you to manage fine-grained audit policies. You should be aware of how to use this package in editions and in a multitenant environment.
Topics:
-
Using the DBMS_FGA PL/SQL Package in a Multitenant Environment
-
Example: Using DBMS_FGA.ADD_POLICY to Create a Fine-Grained Audit Policy
About the DBMS_FGA PL/SQL PL/SQL Package
To manage a fine-grained audit policy, you can use the DBMS_FGA PL/SQL package. However, unless you want to perform column-level auditing or use event handlers with your audit policy, you should create audit policies as described in "Auditing Activities with Unified Audit Policies and the AUDIT Statement".
The DBMS_FGA PL/SQL package enables you to add all combinations of SELECT, INSERT, UPDATE, and DELETE statements to one policy. You also can audit MERGE statements, by auditing the underlying actions of INSERT and UPDATE. To audit MERGE statements, configure fine-grained access on the INSERT and UPDATE statements. Only one record is generated for each policy for successful MERGE operations. To administer fine-grained audit policies, you must have be granted the AUDIT_ADMIN role. Note also that the EXECUTE privilege for the DBMS_FGA package is mandatorily audited.
The audit policy is bound to the table for which you created it. This simplifies the management of audit policies because the policy only needs to be changed once in the database, not in each application. In addition, no matter how a user connects to the database—from an application, a Web interface, or through SQL*Plus or Oracle SQL Developer—Oracle Database records any actions that affect the policy.
If any rows returned from a query match the audit condition that you define, then Oracle Database inserts an audit entry into the fine-grained audit trail. This entry excludes all the information that is reported in the regular audit trail. In other words, only one row of audit information is inserted into the audit trail for every fine-grained audit policy that evaluates to true.
For detailed information about the syntax of the DBMS_FGA package, see Oracle Database PL/SQL Packages and Types Reference.
Using the DBMS_FGA PL/SQL Package with Editions
If you plan to use the DBMS_FGA package policy across different editions, then you can control the results of the policy: whether the results are uniform across all editions, or specific to the edition in which the policy is used.
See "How Editions Affects the Results of a Global Application Context PL/SQL Package" for more information.
Using the DBMS_FGA PL/SQL Package in a Multitenant Environment
In a multitenant environment, the DBMS_FGA PL/SQL package applies only to the current local PDBs.
You cannot create one policy for the entire multitenant environment.
Creating a Fine-Grained Audit Policy
The DBMS_FGA.ADD_POLICY procedure enables you to create a fine-grained audit policy.
Topics:
About Creating a Fine-Grained Audit Policy
To create a fine-grained audit policy, you can use the DBMS_FGA.ADD_POLICY procedure. This procedure creates an audit policy using the supplied predicate as the audit condition.
By default, Oracle Database executes the policy predicate with the privileges of the user who owns the policy. The maximum number of fine-grained policies on any table or view object is 256. Oracle Database stores the policy in the data dictionary table, but you can create the policy on any table or view that is not in the SYS schema. In a multitenant environment, the fine grained policy is only created in the local PDB.
You cannot modify a fine-grained audit policy after you have created it. If you must modify the policy, then drop and recreate it.
You can find information about a fine-grained audit policy by querying the ALL_AUDIT_POLICIES, DBA_AUDIT_POLICIES, and ALL_AUDIT_POLICIES views. The UNIFIED_AUDIT_TRAIL view contains a column entitled FGA_POLICY_NAME, which you can use to filter out rows that were generated using a specific fine-grained audit policy.
Be aware that if a table column has a fine-grained audit policy, you cannot encrypt or decrypt this column (by using the UPDATE statement). To do so raises an ORA-28133: full table access is restricted by fine-grained security error. If you want to update the column, first temporarily disable the fine-grained audit policy and then encrypt or decrypt the column. Afterwards, re-enable the fine-grained audit policy. See "Disabling a Fine-Grained Audit Policy" for more information.
Syntax for Creating a Fine-Grained Audit Policy
The syntax for the DBMS_FGA.ADD_POLICY procedure enables you to configure a wide range of settings, such as indicating the objects to with the policy is applied and whether to use a handler for more complex settings.
The syntax is as follows:
DBMS_FGA.ADD_POLICY( object_schema IN VARCHAR2 DEFAULT NULL object_name IN VARCHAR2, policy_name IN VARCHAR2, audit_condition IN VARCHAR2 DEFAULT NULL, audit_column IN VARCHAR2 DEFAULT NULL handler_schema IN VARCHAR2 DEFAULT NULL, handler_module IN VARCHAR2 DEFAULT NULL, enable IN BOOLEAN DEFAULT TRUE, statement_types IN VARCHAR2 DEFAULT SELECT, audit_trail IN BINARY_INTEGER DEFAULT NULL, audit_column_opts IN BINARY_INTEGER DEFAULT ANY_COLUMNS, policy_owner IN VARCHAR2 DEFAULT NULL);
In this specification:
-
object_schema: Specifies the schema of the object to be audited. (IfNULL, the current log-on user schema is assumed.) -
object_name: Specifies the name of the object to be audited. -
policy_name: Specifies the name of the policy to be created. Ensure that this name is unique. -
audit_condition: Specifies a Boolean condition in a row.NULLis allowed and acts asTRUE. See "Auditing Specific Columns and Rows" for more information. If you specifyNULLor no audit condition, then any action on a table with that policy creates an audit record, whether or not rows are returned.Follow these guidelines:
-
Do not include functions, which execute the auditable statement on the same base table, in the
audit_conditionsetting. For example, suppose you create a function that executes anINSERTstatement on theHR.EMPLOYEEStable. The policy'saudit_conditioncontains this function and it is forINSERTstatements (as set bystatement_types). When the policy is used, the function executes recursively until the system has run out of memory. This can raise the errorORA-1000: maximum open cursors exceededorORA-00036: maximum number of recursive SQL levels (50) exceeded. -
Do not issue the
DBMS_FGA.ENABLE_POLICYorDBMS_FGA.DISABLE_POLICYstatement from a function in a policy's condition.
-
-
audit_column: Specifies one or more columns to audit, including hidden columns. If set toNULLor omitted, all columns are audited. These can include Oracle Label Security hidden columns or object type columns. The default,NULL, causes audit if any column is accessed or affected. -
handler_schema: If an alert is used to trigger a response when the policy is violated, specifies the name of the schema that contains the event handler. The default,NULL, uses the current schema. See also "Tutorial: Adding an Email Alert to a Fine-Grained Audit Policy". -
handler_module: Specifies the name of the event handler. Include the package the event handler is in. This function is invoked only after the first row that matches the audit condition in the query is processed.Follow these guidelines:
-
Do not create recursive fine-grained audit handlers. For example, suppose you create a handler that executes an
INSERTstatement on theHR.EMPLOYEEStable. The policy that is associated with this handler is forINSERTstatements (as set by thestatement_typesparameter). When the policy is used, the handler executes recursively until the system has run out of memory. This can raise the errorORA-1000: maximum open cursors exceededorORA-00036: maximum number of recursive SQL levels (50) exceeded. -
Do not issue the
DBMS_FGA.ENABLE_POLICYorDBMS_FGA.DISABLE_POLICYstatement from a policy handler. Doing so can raise theORA-28144: Failed to execute fine-grained audit handlererror.
-
-
enable: Enables or disables the policy using true or false. If omitted, the policy is enabled. The default isTRUE. -
statement_types: Specifies the SQL statements to be audited:INSERT,UPDATE,DELETE, orSELECTonly. If you want to audit aMERGEoperation, then setstatement_typesto'INSERT,UPDATE'. The default isSELECT. -
audit_trail: If you have migrated to unified auditing, then Oracle Database ignores this parameter and writes the audit records immediately to the unified audit trail. If you have migrated to unified auditing, then omit this parameter.Be aware that sensitive data, such as credit card information, can be recorded in clear text.
-
audit_column_opts: If you specify more than one column in theaudit_columnparameter, then this parameter determines whether to audit all or specific columns. See "Auditing Specific Columns and Rows" for more information. -
policy_owner: User who owns the fine-grained auditing policy. However, this setting is not a user-supplied argument. The Oracle Data Pump client uses this setting internally to recreate the fine-grained audit policies appropriately.
See Oracle Database PL/SQL Packages and Types Reference for additional details about the DBMS_FGA.ADD_POLICY syntax.
Auditing Specific Columns and Rows
You can fine-tune the audit behavior by targeting a specific column, referred to as a relevant column, to be audited if a condition is met. To accomplish this, you use the audit_column parameter to specify one or more sensitive columns. In addition, you can audit data in specific rows by using the audit_condition parameter to define a Boolean condition. (However, if your policy needs only to audit for conditions, consider using an audit policy condition described in "Creating a Condition for a Unified Audit Policy".)
Example 22-51 performs an audit if anyone in Department 50 tries to access the salary and commission_pct columns.
audit_condition => 'DEPARTMENT_ID = 50', audit_column => 'SALARY,COMMISSION_PCT,'
As you can see, this feature is enormously beneficial. It not only enables you to pinpoint particularly important types of data to audit, but it provides increased protection for columns that contain sensitive data, such as Social Security numbers, salaries, patient diagnoses, and so on.
If the audit_column lists more than one column, then you can use the audit_column_opts parameter to specify whether a statement is audited when the query references any column specified in the audit_column parameter or only when all columns are referenced. For example:
audit_column_opts => DBMS_FGA.ANY_COLUMNS, audit_column_opts => DBMS_FGA.ALL_COLUMNS,
If you do not specify a relevant column, then auditing applies to all columns.
For more information about the audit_condition, audit_column, and audit_column_opts parameters in the DBMS_FGA.ADD_POLICY procedure, see Oracle Database PL/SQL Packages and Types Reference. See also the usage notes for the ADD_POLICY procedure in that section.
Example: Using DBMS_FGA.ADD_POLICY to Create a Fine-Grained Audit Policy
Example 22-51 shows how to audit statements INSERT, UPDATE, DELETE, and SELECT on table HR.EMPLOYEES. Note that this example omits the audit_column_opts parameter, because it is not a mandatory parameter.
Example 22-51 Using DBMS_FGA.ADD_POLICY to Create a Fine-Grained Audit Policy
BEGIN DBMS_FGA.ADD_POLICY( object_schema => 'HR', object_name => 'EMPLOYEES', policy_name => 'chk_hr_employees', audit_column => 'SALARY', enable => TRUE, statement_types => 'INSERT, UPDATE, SELECT, DELETE'); END; /
At this point, if you query the DBA_AUDIT_POLICIES view, you will find the new policy listed:
SELECT POLICY_NAME FROM DBA_AUDIT_POLICIES; POLICY_NAME ------------------------------- CHK_HR_EMPLOYEES
Afterwards, any of the following SQL statements log an audit event record.
SELECT COUNT(*) FROM HR.EMPLOYEES WHERE COMMISSION_PCT = 20 AND SALARY > 4500; SELECT SALARY FROM HR.EMPLOYEES WHERE DEPARTMENT_ID = 50; DELETE FROM HR.EMPLOYEES WHERE SALARY > 1000000;
Disabling a Fine-Grained Audit Policy
You can disable a fine-grained audit policy by using the DBMS_FGA.DISABLE_POLICY procedure.
-
Use the following syntax to disable a fine-grained audit policy:
DBMS_FGA.DISABLE_POLICY( object_schema VARCHAR2, object_name VARCHAR2, policy_name VARCHAR2);
For example, to disable the fine-grained audit policy created in Example 22-51.
BEGIN DBMS_FGA.DISABLE_POLICY( object_schema => 'HR', object_name => 'EMPLOYEES', policy_name => 'chk_hr_employees'); END; /
For detailed information about the DISABLE_POLICY syntax, see Oracle Database PL/SQL Packages and Types Reference.
Enabling a Fine-Grained Audit Policy
You can enable a fine-grained audit policy by using the DBMS_FGA.ENABLE_POLICY procedure.
-
Use the following syntax to enable a fine-grained audit policy:
DBMS_FGA.ENABLE_POLICY( object_schema VARCHAR2, object_name VARCHAR2, policy_name VARCHAR2, enable BOOLEAN);
For example, to reenable the
chk_hr_emppolicy by using theDBMS_FGA.ENABLE_POLICYprocedureBEGIN DBMS_FGA.ENABLE_POLICY( object_schema => 'HR', object_name => 'EMPLOYEES', policy_name => 'chk_hr_employees', enable => TRUE); END; /
For detailed information about the ENABLE_POLICY syntax, see Oracle Database PL/SQL Packages and Types Reference.
Dropping a Fine-Grained Audit Policy
Oracle Database automatically drops the audit policy if you remove the object specified in the object_name parameter of the DBMS_FGA.ADD_POLICY procedure, or if you drop the user who created the audit policy.
-
Use the following syntax to drop a fine-grained audit policy:
DBMS_FGA.DROP_POLICY( object_schema VARCHAR2, object_name VARCHAR2, policy_name IVARCHAR2);
For example, to drop a fine-grained audit policy manually by using the
DBMS_FGA.DROP_POLICYprocedure:BEGIN DBMS_FGA.DROP_POLICY( object_schema => 'HR', object_name => 'EMPLOYEES', policy_name => 'chk_hr_employees'); END; /
See Oracle Database PL/SQL Packages and Types Reference for detailed information about the DROP_POLICY syntax.
Tutorial: Adding an Email Alert to a Fine-Grained Audit Policy
This tutorial demonstrates how to create a fine-grained audit policy that generates an email alert when users violate the policy.
Topics:
-
Step 3: Configure an Access Control List File for Network Services
-
Step 5: Create and Test the Fine-Grained Audit Policy Settings
About This Tutorial
You can add an email alert to a fine-grained audit policy that goes into effect when a user (or an intruder) violates the policy. To accomplish this, you first must create a procedure that generates the alert, and then use the following DBMS_FGA.ADD_POLICY parameters to call this function when someone violates this policy:
-
handler_schema: The schema in which the handler event is stored -
handler_module: The name of the event handler
The alert can come in any form that best suits your environment: an email or pager notification, updates to a particular file or table, and so on. Creating alerts also helps to meet certain compliance regulations, such as California Senate Bill 1386. In this tutorial, you will create an email alert.
In this tutorial, you create an email alert that notifies a security administrator that a Human Resources representative is trying to select or modify salary information in the HR.EMPLOYEES table. The representative is permitted to make changes to this table, but to meet compliance regulations, we want to create a record of all salary selections and modifications to the table.
Note:
If you are using a multitenant environment, then this tutorial applies to the current PDB only.Step 1: Install and Configure the UTL_MAIL PL/SQL Package
The UTL_MAIL PL/SQL enables you to manage email that includes commonly used email features, such as attachments, CC, and BCC. You must install and configure this package before you can use it.
-
Log on as user
SYSwith theSYSDBAadministrative privilege.sqlplus sys as sysdba Enter password: password -
In a multitenant environment, connect to the appropriate PDB.
For example:
CONNECT SYS@hrpdb AS SYSDBA Enter password: passwordTo find the available PDBs, query the
DBA_PDBSdata dictionary view. To check the current PDB, run theshow con_namecommand. -
Install the
UTL_MAILpackage.@$ORACLE_HOME/rdbms/admin/utlmail.sql @$ORACLE_HOME/rdbms/admin/prvtmail.plb
The
UTL_MAILpackage enables you to manage email. See Oracle Database PL/SQL Packages and Types Reference for more information aboutUTL_MAIL.Be aware that currently, the
UTL_MAILPL/SQL package does not support SSL servers. -
Check the current value of the
SMTP_OUT_SERVERinitialization parameter, and make a note of this value so that you can restore it when you complete this tutorial.For example:
SHOW PARAMETER SMTP_OUT_SERVER
If the
SMTP_OUT_SERVERparameter has already been set, then output similar to the following appears:NAME TYPE VALUE ----------------------- ----------------- ---------------------------------- SMTP_OUT_SERVER string some_imap_server.example.com
-
Issue the following
ALTER SYSTEMstatement:ALTER SYSTEM SET SMTP_OUT_SERVER="imap_mail_server.example.com";Replace
imap_mail_serverwith the name of your SMTP server, which you can find in the account settings in your email tool. Enclose these settings in quotation marks. For example:ALTER SYSTEM SET SMTP_OUT_SERVER="my_imap_server.example.com";
-
Connect as
SYSusing theSYSOPERprivilege and then restart the database.CONNECT SYS AS SYSOPER -- Or, CONNECT SYS@hrpdb AS SYSOPER Enter password: password SHUTDOWN IMMEDIATE STARTUP
-
Ensure that the
SMTP_OUT_SERVERparameter setting is correct.CONNECT SYS AS SYSDBA -- Or, CONNECT SYS@hrpdb AS SYSDBA Enter password: password SHOW PARAMETER SMTP_OUT_SERVER
Output similar to the following appears:
NAME TYPE VALUE ----------------------- ----------------- ---------------------------------- SMTP_OUT_SERVER string my_imap_server.example.com
Step 2: Create User Accounts
You must create an administrative account and an auditor user.
-
Ensure that you are connected as
SYSusing theSYSDBAadministrative privilege, and then create thefga_adminuser, who will create the fine-grained audit policy.For example:
CONNECT SYS AS SYSDBA -- Or, CONNECT SYS@hrpdb AS SYSDBA Enter password: password CREATE USER fga_admin IDENTIFIED BY password; GRANT CREATE SESSION, CREATE PROCEDURE, AUDIT_ADMIN TO fga_admin; GRANT EXECUTE ON UTL_TCP TO fga_admin; GRANT EXECUTE ON UTL_SMTP TO fga_admin; GRANT EXECUTE ON UTL_MAIL TO fga_admin; GRANT EXECUTE ON DBMS_NETWORK_ACL_ADMIN TO fga_admin;
Replace
passwordwith a password that is secure. See "Minimum Requirements for Passwords" for more information.The
UTL_TCP,UTL_SMTP,UTL_MAIL, andDBMS_NETWORK_ACL_ADMINPL/SQL packages are used by the email security alert that you create. -
Create the auditor user, who will check the audit trail for this policy.
GRANT CREATE SESSION TO fga_auditor IDENTIFIED BY password; GRANT AUDIT_VIEWER TO fga_auditor; -
Connect as user
SYSTEM.CONNECT SYSTEM -- Or, CONNECT SYSTEM@hrpdb Enter password: password
-
Ensure that the
HRschema account is unlocked and has a password. If necessary, unlockHRand grant this user a password.SELECT USERNAME, ACCOUNT_STATUS FROM DBA_USERS WHERE USERNAME = 'HR';
If the
DBA_USERSview lists userHRas locked and expired, then enter the following statement to unlock theHRaccount and create a new password:ALTER USER HR ACCOUNT UNLOCK IDENTIFIED BY password;Enter a password that is secure. For greater security, do not give the
HRaccount the same password from previous releases of Oracle Database. "Minimum Requirements for Passwords" for the minimum requirements for creating passwords. -
Create a user account for Susan Mavris, who is an HR representative whose actions you will audit, and then grant this user access to the
HR.EMPLOYEEStable.GRANT CREATE SESSION TO smavris IDENTIFIED BY password; GRANT SELECT, INSERT, UPDATE, DELETE ON HR.EMPLOYEES TO SMAVRIS;
Step 3: Configure an Access Control List File for Network Services
Before you can use PL/SQL network utility packages such as UTL_MAIL, you must configure an access control list (ACL) file that enables fine-grained access to external network services. For detailed information about this topic, see Chapter 6, "Managing Fine-Grained Access in PL/SQL Packages and Types."
-
Connect to SQL*Plus as user
fga_admin.CONNECT fga_admin -- Or, CONNECT fga_admin@hrpdb Enter password: password
-
Configure the following access control setting and its privilege definitions.
BEGIN DBMS_NETWORK_ACL_ADMIN.APPEND_HOST_ACE( host => 'SMTP_OUT_SERVER_setting', lower_port => 25, ace => xs$ace_type(privilege_list => xs$name_list('smtp'), principal_name => 'FGA_ADMIN', principal_type => xs_acl.ptype_db)); END; /In this example:
-
SMTP_OUT_SERVER_setting: Enter theSMTP_OUT_SERVERsetting that you set for theSMTP_OUT_SERVERparameter in "Step 1: Install and Configure the UTL_MAIL PL/SQL Package". This setting should match exactly the setting that your email tool specifies for its outgoing server. -
lower_port: Enter the port number that your email tool specifies for its outgoing server. Typically, this setting is 25. Enter this value for thelower_portsetting. (Currently, theUTL_MAILpackage does not support SSL. If your email server is an SSL server, then enter 25 for the port number, even if the email server uses a different port number.) -
ace: Define the privileges here.
-
Step 4: Create the Email Security Alert PL/SQL Procedure
The email security alert PL/SQL procedure generates a message describing the violation and then sends this message to the appropriate users.
-
As user
fga_admin, create the following procedure. (You can copy and paste this text by positioning the cursor at the start ofCREATE OR REPLACEin the first line.)1 2 3 4 5 6 7 8 9 10 11 12
CREATE OR REPLACE PROCEDURE email_alert (sch varchar2, tab varchar2, pol varchar2) AS msg varchar2(20000) := 'HR.EMPLOYEES table violation. The time is: '; BEGIN msg := msg||TO_CHAR(SYSDATE, 'Day DD MON, YYYY HH24:MI:SS'); UTL_MAIL.SEND ( sender => 'youremail@example.com', recipients => 'recipientemail@example.com', subject => 'Table modification on HR.EMPLOYEES', message => msg); END email_alert; /In this example:
-
Lines 1 and 2: You must include a signature that describes the schema name (
sch), table name (tab), and the name of the audit procedure (pol) that you will define in audit policy in the next step. -
Lines 7 and 8: Replace
youremail@example.comwith your email address, andrecipientemail@example.comwith the email address of the person you want to receive the notification.
-
Step 5: Create and Test the Fine-Grained Audit Policy Settings
The fine-grained audit policy will trigger the alert when the policy is violated.
-
As user
fga_admin, create thechk_hr_emppolicy fine-grained audit policy as follows.BEGIN DBMS_FGA.ADD_POLICY ( object_schema => 'HR', object_name => 'EMPLOYEES', policy_name => 'CHK_HR_EMP', audit_column => 'SALARY', handler_schema => 'FGA_ADMIN', handler_module => 'EMAIL_ALERT', enable => TRUE, statement_types => 'SELECT, UPDATE'); END; /
-
Commit the changes you have made to the database.
COMMIT;
-
Test the settings that you have created so far.
EXEC email_alert ('hr', 'employees', 'chk_hr_emp');SQL*Plus should display a
PL/SQL procedure successfully completedmessage, and in a moment, depending on the speed of your email server, you should receive the email alert.If you receive an
ORA-24247: network access denied by access control list (ACL)error followed byORA-06512: atstringlinestringerrors, then check the settings in the access control list file.
Step 6: Test the Alert
With the components in place, you are ready to test the alert.
-
Connect to SQL*Plus as user
smavris, check your salary, and give yourself a nice raise.CONNECT smavris -- Or, CONNECT smavris@hrpdb Enter password: password SELECT SALARY FROM HR.EMPLOYEES WHERE LAST_NAME = 'Mavris'; SALARY ----------- 6500 UPDATE HR.EMPLOYEES SET SALARY = 38000 WHERE LAST_NAME = 'Mavris';
By now, depending on the speed of your email server, you (or your recipient) should have received an email with the subject header
Table modification on HR.EMPLOYEESnotifying you of the tampering of theHR.EMPLOYEEStable. Now all you need to do is to query theUNIFIED_AUDIT_TRAILdata dictionary view to find who the violator is. -
If necessary, connect as user
fga_adminand then execute the following procedure to write the audit records to disk:CONNECT fga_admin -- Or, CONNECT fga_admin@hrpdb Enter password: password EXEC DBMS_AUDIT_MGMT.FLUSH_UNIFIED_AUDIT_TRAIL;
-
As user
fga_auditor, query theUNIFIED_AUDIT_TRAILdata dictionary view as follows:CONNECT fga_auditor -- Or, CONNECT fga_auditor@hrpdb Enter password: password col dbusername format a20 col sql_text format a66 col audit_type format a17 SELECT DBUSERNAME, SQL_TEXT, AUDIT_TYPE FROM UNIFIED_AUDIT_TRAIL WHERE OBJECT_SCHEMA = 'HR' AND OBJECT_NAME = 'EMPLOYEES';
Output similar to the following appears:
DBUSERNAME SQL_TEXT AUDIT_TYPE ---------- ----------------------------------------------------------------- ---------------- SMAVRIS UPDATE HR.EMPLOYEES SET SALARY = 38000 WHERE LAST_NAME = 'Mavris' FineGrainedAudit
The audit trail captures the SQL statement that Susan Mavris ran that affected the
SALARYcolumn in theHR.EMPLOYEEStable. The first statement she ran, in which she asked about her current salary, was not recorded because it was not affected by the audit policy. This is because Oracle Database executes the audit function as an autonomous transaction, committing only the actions of thehandler_modulesetting and not any user transaction. The function has no effect on any user SQL transaction.
Step 7: Remove the Components of This Tutorial
If you no longer need the components of this tutorial, then you can remove them.
-
Connect to SQL*Plus as user
SYSTEMprivilege, and then drop usersfga_admin(including the objects in thefga_adminschema),fga_auditor, andsmavris.CONNECT SYSTEM -- Or, CONNECT SYSTEM@hrpdb Enter password: password DROP USER fga_admin CASCADE; DROP USER fga_auditor; DROP USER smavris;
-
Connect as user
HRand remove the loftiness of Susan Mavris's salary.CONNECT HR -- Or, CONNECT HR@hrpdb Enter password: password UPDATE HR.EMPLOYEES SET SALARY = 6500 WHERE LAST_NAME = 'Mavris';
-
If you want, lock and expire
HR, unless other users want to use this account:ALTER USER HR PASSWORD EXPIRE ACCOUNT LOCK;
-
Issue the following
ALTER SYSTEMstatement to restore theSMTP_OUT_SERVERparameter to the previous value, from Step 5 under "Step 1: Install and Configure the UTL_MAIL PL/SQL Package":ALTER SYSTEM SET SMTP_OUT_SERVER="previous_value";Enclose this setting in quotation marks. For example:
ALTER SYSTEM SET SMTP_OUT_SERVER="some_imap_server.example.com"
-
Restart the database instance.
Audit Policy Data Dictionary Views
Table 22-19 lists data dictionary and dynamic views that provide auditing information. For detailed information about these views, see Oracle Database Reference.
Tip:
To find error information about audit policies, check the trace files. TheUSER_DUMP_DEST initialization parameter sets the location of the trace files.Table 22-19 Views That Display Information about Audited Activities
| View | Description |
|---|---|
|
|
Displays information about all fine-grained audit policies |
|
|
Lists default object-auditing options that are to be applied when objects are created |
|
|
Describes application context values that have been configured to be captured in the audit trail |
|
|
Describes all unified audit policies that are enabled in the database |
|
|
Describes all unified audit policies created in the database |
|
|
Shows the description of each unified audit policy, if a description was entered for the unified audit policy using the |
|
|
Maps the auditable system action numbers to the action names |
|
|
Similar to the |
|
|
Displays information about fine-grained audit policies |
|
|
Describes audited Oracle Label Security events performed by users, and indicates if the user's action failed or succeeded |
|
|
Displays audit trail information related to Oracle Database Real Application Security |
|
|
Displays configuration changes made by Oracle Database Vault administrators |
|
|
Displays user activities that are affected by Oracle Database Vault policies |
|
|
Describes privilege (auditing option) type codes. This table can be used to map privilege (auditing option) type numbers to type names. |
|
|
Displays information about all fine-grained audit policies on table and views owned by the current user |
|
|
You can query the |
|
|
Displays all audit records |