3 Getting Started with Oracle Database Vault
Before you can start using Oracle Database Vault, you must register it with the Oracle database. Then you can log in to it.
Topics:
Registering Oracle Database Vault with an Oracle Database
You must register Oracle Database Vault before you can use it. You can register it in a non-multitenant environment and for a multitenant environment, perform the registration based on the type of configuration you have.
Topics:
-
About Registering Oracle Database Vault with an Oracle Database
-
Registering Oracle Database Vault in a Non-Multitenant Environment
-
Registering Oracle Database Vault with a Common User to Manage the CDB Root
-
Registering Database Vault Common Users to Manage Specific PDBs
-
Registering Oracle Database Vault Common Users to Manage All Database Vault PDBs
-
Plugging in a Database That Has Oracle Database Vault Enabled
-
Verifying That Oracle Database Vault Is Configured and Enabled
About Registering Oracle Database Vault with an Oracle Database
After you install Oracle Database, you must register (that is, configure and enable) Oracle Database Vault with the Oracle database in which it was installed.
Oracle Database includes Database Vault when you choose to include a default database in the installation process, but you must register it before you can use it. If you create a custom database, then you can use DBCA to install and enable Database Vault for it. As part of the registration process, you create the Database Vault administrative accounts. The registration process enables Oracle Label Security if it is not already enabled. This procedure applies to the current pluggable database (PDB), as well as to both single-instance and Oracle RAC installations. To check if Database Vault has already been enabled, see "Checking if Oracle Database Vault Is Enabled or Disabled".
This section explains how to register Oracle Database Vault in a non-multitenant environment, and several ways that you can register it in a multitenant environment.
Registering Oracle Database Vault in a Non-Multitenant Environment
You can register Oracle Database Vault from SQL*Plus in a non-multitenant environment.
-
Log into the database instance as user
SYSwith theSYSDBAadministrative privilege.sqlplus sys as sysdba Enter password: password -
As user
SYSwith theSYSDBAadministrative privilege, configure the Database Vault user accounts.BEGIN DVSYS.CONFIGURE_DV ( dvowner_uname => 'dbv_owner', dvacctmgr_uname => 'dbv_acctmgr'); END; /
Do not enter the names
DV_OWNER,DV_ACCTMGR, or the names of any other Database Vault roles for these user accounts. These names are reserved words. "Oracle Database Vault Roles" describes the Database Vault roles. -
Run the
utlrp.sqlscript to recompile invalidated objects.@?/rdbms/admin/utlrp.sql
If the script gives you any instructions, follow them, and then run the script again. If the script terminates abnormally without giving any instructions, run it again.
-
Connect as the Database Vault Owner user that you just configured.
For example:
CONNECT dbv_owner Enter password: password -
EXEC DBMS_MACADM.ENABLE_DV;
-
Connect with the
SYSDBAadministrative privilege.CONNECT / AS SYSDBA
-
Restart the database.
SHUTDOWN IMMEDIATE STARTUP
See "Verifying That Oracle Database Vault Is Configured and Enabled" to confirm that this procedure was successful. After you have registered Oracle Database Vault with an Oracle database, you can start Oracle Database Vault Administrator. See "Logging into Oracle Database Vault" for more information.
Registering Oracle Database Vault with a Common User to Manage the CDB Root
In SQL*Plus, you can register Oracle Database Vault with a common user who will manage the CDB root.
-
In a multitenant environment, log into the root of the database instance as a user who has privileges to create users and grant the
CREATE SESSIONandSET CONTAINERprivileges.For example:.
sqlplus c##sec_admin Enter password: password -
Create two user accounts to be used as the Database Vault accounts and grant them the
CREATE SESSIONandSET CONTAINERprivileges.One account will be the Database Vault Owner user and the second (optional) account will be the Database Vault Account Manager account. Ensure that they have at minimum the
CREATE SESSIONprivilege. If you decide not to create a Database Vault Account Manager account, then the Database Vault Owner will have the Database Vault Account Manager privileges. For better separation of duty, Oracle recommends that you create a Database Vault Account Manager account.Prepend the names of these accounts with
c##orC##. For example:GRANT CREATE SESSION, SET CONTAINER TO c##dbv_owner_root IDENTIFIED BY password CONTAINER = ALL; GRANT CREATE SESSION, SET CONTAINER TO c##dbv_acctmgr_root IDENTIFIED BY password CONTAINER = ALL;
-
Connect to the root as user
SYSwith theSYSDBAadministrative privilegeCONNECT SYS AS SYSDBA Enter password: password -
Configure the Database Vault user accounts.
BEGIN DVSYS.CONFIGURE_DV ( dvowner_uname => 'c##dbv_owner_root', dvacctmgr_uname => 'c##dbv_acctmgr_root'); END; /
-
Run the
utlrp.sqlscript to recompile invalidated objects in the root.@?/rdbms/admin/utlrp.sql
If the script provides instructions, follow them, and then run the script again. If the script terminates abnormally without giving any instructions, run it again.
-
Connect to the root as the Database Vault Owner user that you just configured.
For example:
CONNECT c##dbv_owner_root Enter password: password -
EXEC DBMS_MACADM.ENABLE_DV;
-
Connect with the
SYSDBAadministrative privilege.CONNECT / AS SYSDBA
-
Restart the database.
SHUTDOWN IMMEDIATE STARTUP
See "Verifying That Oracle Database Vault Is Configured and Enabled" to confirm that this procedure was successful. After you have registered Oracle Database Vault with an Oracle database, you can start Oracle Database Vault Administrator. See "Logging into Oracle Database Vault" for more information.
Registering Database Vault Common Users to Manage Specific PDBs
In a multitenant environment, you must register Oracle Database Vault in the root first, then in the PDBs afterward. If you try to register in a PDB first, then an ORA-47503: Database Vault is not enabled on CDB$ROOT error appears.
-
In a multitenant environment, log into the root of the database instance as a user who has privileges to create users and to grant the
CREATE SESSIONandSET CONTAINERprivileges.For example:.
sqlplus c##sec_admin Enter password: password -
If you have not already done so, then create two user accounts to be used as the Database Vault accounts.
See Step 2 under "Registering Oracle Database Vault with a Common User to Manage the CDB Root" for more information about these accounts.
-
Connect to the PDB to which the common users will need access.
For example:
CONNECT c##sec_admin@pdb_name Enter password: password
To find the available PDBs, query the
DBA_PDBSdata dictionary view. To check the current PDB, run theshow con_namecommand. -
Grant the
CREATE SESSIONandSET CONTAINERprivileges to the users.For example:
GRANT CREATE SESSION, SET CONTAINER TO c##dbv_owner_root; GRANT CREATE SESSION, SET CONTAINER TO c##dbv_acctmgr_root;
-
Connect as user
SYSwith theSYSDBAadministrative privilegeCONNECT SYS@pdb_name AS SYSDBA Enter password: password
-
While still in the PDB, configure the Database Vault user accounts.
For example:
BEGIN DVSYS.CONFIGURE_DV ( dvowner_uname => 'c##dbv_owner_root', dvacctmgr_uname => 'c##dbv_acctmgr_root'); END; /
-
Run the
utlrp.sqlscript to recompile invalidated objects in this PDB.@?/rdbms/admin/utlrp.sql
If the script provides instructions, follow them, and then run the script again. If the script terminates abnormally without giving any instructions, run it again.
-
Connect to the PDB as the Database Vault Owner user that you just configured.
For example:
CONNECT c##dbv_owner_root@pdb_name Enter password: password
-
EXEC DBMS_MACADM.ENABLE_DV;
-
Connect with the
SYSDBAadministrative privilege.CONNECT / AS SYSDBA
-
Close and reopen the PDB.
For example:
ALTER PLUGGABLE DATABASE pdb_name CLOSE IMMEDIATE; ALTER PLUGGABLE DATABASE pdb_name OPEN;
See "Verifying That Oracle Database Vault Is Configured and Enabled" to confirm that this procedure was successful. After you have registered Oracle Database Vault with an Oracle database, you can start Oracle Database Vault Administrator. See "Logging into Oracle Database Vault" for more information.
Registering Oracle Database Vault Common Users to Manage All Database Vault PDBs
Using SQL*Plus, you can register Oracle Database Vault common users to manage all Database Vault PDBs.
-
In a multitenant environment, log into the root of the database instance as user
SYSwith theSYSDBAadministrative privilege.sqlplus sys as sysdba Enter password: password -
Ensure that Oracle Database Vault has been configured and enabled on the root.
See "Verifying That Oracle Database Vault Is Configured and Enabled".
-
If you have not already done so, create two user accounts to be used as the Database Vault accounts, and grant them the
CREATE SESSIONandSET CONTAINERprivileges.For example:
GRANT CREATE SESSION, SET CONTAINER TO c##dbv_owner_root IDENTIFIED BY password CONTAINER = ALL; GRANT CREATE SESSION, SET CONTAINER TO c##dbv_acctmgr_root IDENTIFIED BY password CONTAINER = ALL;
See Step 2 under "Registering Oracle Database Vault with a Common User to Manage the CDB Root" for more information about these accounts.
-
As user
SYSwith theSYSDBAprivilege, connect to the PDB to which the common users must have access.For example:
CONNECT SYS@pdb_name AS SYSDBA Enter password: password
To find the available PDBs, query the
DBA_PDBSdata dictionary view. To check the current PDB, run theshow con_namecommand. -
Configure the Database Vault user accounts for the PDB.
BEGIN DVSYS.CONFIGURE_DV ( dvowner_uname => 'c##dbv_owner_root', dvacctmgr_uname => 'c##dbv_acctmgr_root'); END; /
-
Run the
utlrp.sqlscript to recompile invalidated objects in this PDB.@?/rdbms/admin/utlrp.sql
If the script provides instructions, follow them, and then run the script again. If the script terminates abnormally without giving any instructions, run it again.
-
Connect to the PDB as the Database Vault Owner user that you just configured.
For example:
CONNECT c##dbv_owner_root Enter password: passwordTo find the available PDBs, query the
DBA_PDBSdata dictionary view. To check the current PDB, run theshow con_namecommand. -
EXEC DBMS_MACADM.ENABLE_DV;
-
Connect with the
SYSDBAadministrative privilege.CONNECT / AS SYSDBA
-
Close and reopen the PDB.
For example:
ALTER PLUGGABLE DATABASE pdb_name CLOSE IMMEDIATE; ALTER PLUGGABLE DATABASE pdb_name OPEN;
See "Verifying That Oracle Database Vault Is Configured and Enabled" to confirm that this procedure was successful. After you have registered Oracle Database Vault with an Oracle database, you can start Oracle Database Vault Administrator. See "Logging into Oracle Database Vault" for more information.
Plugging in a Database That Has Oracle Database Vault Enabled
From SQL*Plus, in a multitenant environment, you can plug in a database that already has Database Vault enabled.
In this scenario, the plugged in database has its own local Database Vault accounts.
To enable a common user to manage the Database Vault configuration for this PDB:
-
Log into the PDB as the local Database Vault owner.
For example:
sqlplus dbv_owner@pdb_name Enter password: password
To find the available PDBs, query the
DBA_PDBSdata dictionary view. To check the current PDB, run theshow con_namecommand. -
Grant the common user the
CREATE SESSIONandSET CONTAINERprivileges, and the appropriate Database Vault roles.For example:
GRANT CREATE SESSION, SET CONTAINER, DV_OWNER TO c##dbv_owner_root; GRANT CREATE SESSION, SET CONTAINER, DV_ACCTMGR TO c##dbv_acctmgr_root;
If necessary, see "Verifying That Oracle Database Vault Is Configured and Enabled". After you have registered Oracle Database Vault with an Oracle database, you can start Oracle Database Vault Administrator. See "Logging into Oracle Database Vault" for more information.
Verifying That Oracle Database Vault Is Configured and Enabled
You can query the V$OPTION dynamic view to verify if Oracle Database is configured and enabled.
-
Query the
V$OPTIONdynamic view as follows:-
To find if Oracle Database Vault is configured and enabled, run the following query, which should show the
VALUEsetting asTRUE:SELECT VALUE FROM V$OPTION WHERE PARAMETER = 'Oracle Database Vault';
-
To check if Oracle Label Security is enabled, query
V$OPTIONas follows:SELECT VALUE FROM V$OPTION WHERE PARAMETER = 'Oracle Label Security';
-
At this stage, you have only the two Oracle Database Vault accounts: one for the Database Vault Owner and the other for the Database Vault Account Manager. Oracle recommends that you reserve these accounts as back-up accounts, and then grant the DV_OWNER and DV_ACCTMGR roles to existing user accounts for every day use. See the tip under "Oracle Database Vault Accounts" for more information.
Logging into Oracle Database Vault
From Oracle Enterprise Manager Cloud Control (Cloud Control), you can use the Oracle Database Vault pages to administer and monitor Database Vault-protected databases from a centralized console, automate alerts, view Database Vault reports, and propagate Database Vault policies to other Database Vault-protected databases.
-
Ensure that you have configured the Cloud Control target databases that you plan to use with Database Vault.
See the Oracle Enterprise Manager online help and Oracle Enterprise Manager Advanced Configuration for more information about configuring target databases.
-
If necessary, register Oracle Database Vault.
If you have just installed Oracle Database Vault, you must register it with the database. See "Registering Oracle Database Vault with an Oracle Database" for more information.
-
Start Cloud Control.
For example:
https://myserver.example.com:7799/em
-
Log into Cloud Control as user
SYSMAN. -
In the Cloud Control home page, from the Targets menu, select Databases.
-
In the Databases page, select the link for the Oracle Database Vault-protected database to which you want to connect.
The Database home page appears.
-
From the Security menu, select Database Vault.
The Database Login page appears.
-
Enter the following information:
-
Username: Enter the name of a user who has been granted the appropriate Oracle Database Vault role:
-
Creating and propagating Database Vault policies:
DV_OWNERorDV_ADMINrole,SELECT ANY DICTIONARYprivilege -
Viewing Database Vault alerts and reports:
DV_OWNER,DV_ADMIN, orDV_SECANALYSTrole,SELECT ANY DICTIONARYprivilege
See "About Oracle Database Vault Roles" for more information.
-
-
Password: Enter your password.
-
Role: Select NORMAL from the list.
-
Save as: Select this check box if you want these credentials to be automatically filled in for you the next time that this page appears. The credentials are stored in Enterprise Manager in a secured manner. Access to these credentials depends on the user who is currently logged in.
The Database Vault home page appears.
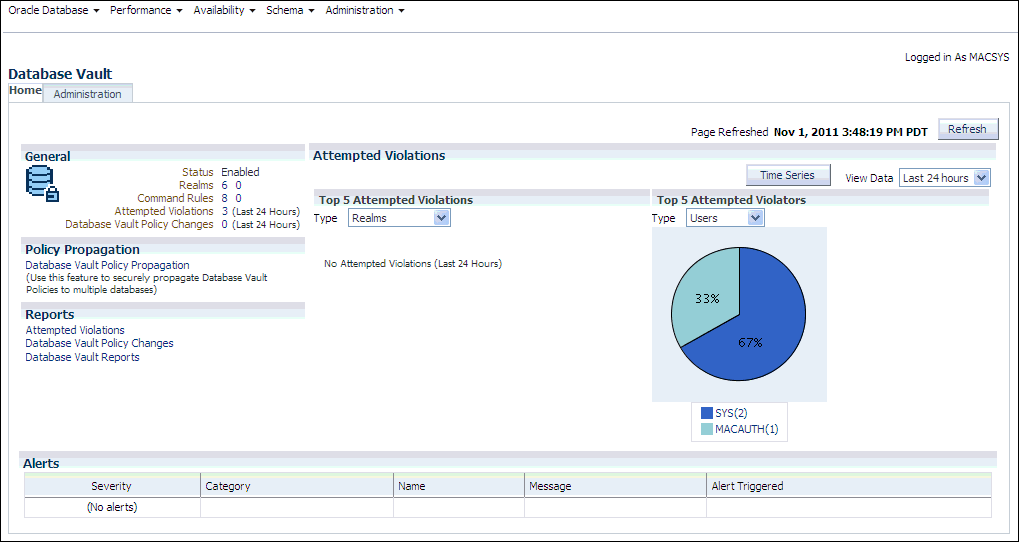
Description of the illustration cc_home_page.gif
-
Quick Start Tutorial: Securing a Schema from DBA Access
This tutorial shows how to create a realm around the HR schema. After you create the realm, you will test the realm with a user account.
Topics:
About This Tutorial
In this tutorial, you create a simple security configuration for the HR sample database schema.
In the HR schema, the EMPLOYEES table has information such as salaries that should be hidden from most employees in the company, including those with administrative access. To accomplish this, you add the HR schema to the secured objects of the protection zone, which in Oracle Database Vault is called a realm, inside the database. Then you grant limited authorizations to this realm. Afterward, you test the realm to make sure it has been properly secured. And finally, to see how Oracle Database Vault provides an audit trail on suspicious activities like the one you will try when you test the realm, you will run a report.
Before you can use this tutorial, ensure that the HR sample schema is installed. See Oracle Database Sample Schemas for information on installing the sample schemas.
Step 1: Log On as SYSTEM to Access the HR Schema
You must enable the HR schema for this tutorial.
-
Log into the database instance as user
SYSTEMand access theHRschema.sqlplus system Enter password: password -
In a multitenant environment, connect to the appropriate PDB.
For example:
CONNECT SYSTEM@my_pdb Enter password: passwordTo find the available PDBs, query the
DBA_PDBSdata dictionary view. To check the current PDB, run theshow con_namecommand. -
Query the
HR.EMPLOYEEStable as follows.SELECT FIRST_NAME, LAST_NAME, SALARY FROM HR.EMPLOYEES WHERE ROWNUM < 10;
Output similar to the following appears:
FIRST_NAME LAST_NAME SALARY -------------------- ------------------------- ---------- Steven King 24000 Neena Kochhar 17000 Lex De Haan 17000 Alexander Hunold 9000 Bruce Ernst 6000 David Austin 4800 Valli Pataballa 4800 Diana Lorentz 4200 Nancy Greenberg 12008 9 rows selected.
-
If the
HRschema is locked and expired, log into the database instance as theDV_ACCTMGRuser and unlock and unexpire the account. For example:sqlplus bea_dvacctmgr -- For CDBs: sqlplus bea_dvacctmgr@hrpdb Enter password: password ALTER USER HR ACCOUNT UNLOCK IDENTIFIED BY password
Replace
passwordwith a password that is secure. See Oracle Database Security Guide for the minimum requirements for creating passwords.As you can see,
SYSTEMhas access to the salary information in theEMPLOYEEStable of theHRschema. This is becauseSYSTEMis automatically granted theDBArole, which includes theSELECT ANY TABLEsystem privilege. -
Do not exit SQL*Plus.
Step 2: Create a Realm
Realms can protect one or more schemas, individual schema objects, and database roles. Once you create a realm, you can create security restrictions that apply to the schemas and their schema objects within the realm. Your first step is to create a realm for the HR schema.
-
Log into Oracle Database Vault Administrator from Cloud Control as a user who has been granted the
DV_OWNERorDV_ADMINrole and theSELECT ANY DICTIONARYprivilege."Logging into Oracle Database Vault" explains how to log in.
-
In the Administration page, under Database Vault Components, click Realms. (It should be selected by default.)
-
In the Realms page of Oracle Database Vault Administrator, click Create.
-
In the Create Realm page, under General, enter
HR Appsafter Name. -
In the Description field, enter
Realm to protect the HR schema. -
After Status, ensure that Enabled is selected so that the realm can be used.
-
Under Audit Options, ensure that Audit On Failure is selected so that you can create an audit trial later on.
-
Click Next to display the Realm secured objects page.
-
Click the Add button and in the Add Secured Object dialog box, enter the following information:
-
Owner: Enter
HRto select theHRschema. -
Object Type: Enter
TABLE. -
Object Name: Enter
EMPLOYEES.
-
-
Click OK.
The
HR.EMPLOYEEStable is added to the Create Realm : Realm Secured Objects page. -
Click Done, and then click Finish.
At this stage, you have created the realm but you have not assigned any authorizations to it. You will take care of that later on in this tutorial.
Step 3: Create the SEBASTIAN User Account
At this stage, there are no database accounts or roles authorized to access or otherwise manipulate the database objects the realm will protect. So, the next step is to authorize database accounts or database roles so that they can have access to the schemas within the realm. You will create the SEBASTIAN user account.
-
In SQL*Plus, connect as the Database Vault Account Manager, who has the
DV_ACCTMGRrole, and create the local userSEBASTIAN.For example:
CONNECT bea_dvacctmgr -- Or, CONNECT bea_dvacctmgr@hrpdb Enter password: password GRANT CREATE SESSION TO SEBASTIAN IDENTIFIED BY password;
Replace
passwordwith a password that is secure. See Oracle Database Security Guide for the minimum requirements for creating passwords. -
Connect as
SYSwith theSYSDBAprivilege, and then grantSEBASTIANthe following additional privilege.CONNECT SYS AS SYSDBA -- Or, CONNECT SYS@hrpdb AS SYSDBA Enter password: password GRANT READ ANY TABLE TO SEBASTIAN;
Do not exit SQL*Plus; you will need it for Step 5: Test the Realm, when you test the realm.
Step 4: Create an Authorization for the Realm
At this stage, even though SEBASTIAN has the SELECT ANY TABLE privilege, he cannot select from the HR.EMPLOYEES table because it is protected by a realm.
Next, authorize user SEBASTIAN to have access to the HR Apps realm as follows:
-
In the Realms page of Database Vault Administrator, select the HR Apps in the list of realms, and then click Edit.
-
Click the Next button until you reach the Realm authorizations page.
-
Click Add and then enter the following information in the Add Authorizations dialog box:
-
Realm Authorization Grantee: Enter
SEBASTIAN. -
Realm Authorization Type: Select Participant from the list.
-
Realm Authorization Ruleset: Leave this field blank.
-
-
Click OK.
The Participant (0) authorization allows the user
SEBASTIANin the HR Apps realm to manage access, manipulate, and create objects protected by the HR Apps realm. In this case, theHRuser andSEBASTIANare the only users allowed to view theEMPLOYEEStable. -
Click Done, and then Finish.
Step 5: Test the Realm
To test the realm, try accessing the EMPLOYEES table as a user other than HR. The SYSTEM account normally has access to all objects in the HR schema, but now that you have safeguarded the EMPLOYEES table with Oracle Database Vault, this is no longer the case.
In SQL*Plus, connect as SYSTEM, and then try accessing the salary information in the EMPLOYEES table again:
CONNECT SYSTEM -- Or, CONNECT SYSTEM@hrpdb Enter password: password SELECT FIRST_NAME, LAST_NAME, SALARY FROM HR.EMPLOYEES WHERE ROWNUM <10;
The following output should appear:
Error at line 1: ORA-01031: insufficient privileges
SYSTEM no longer has access to the salary information in the EMPLOYEES table. (In fact, even user SYS does not have access to this table.) However, user SEBASTIAN does have access to this information. Try the following:
CONNECT sebastian -- Or, CONNECT sebastian@hrpdb Enter password: password SELECT FIRST_NAME, LAST_NAME, SALARY FROM HR.EMPLOYEES WHERE ROWNUM <10;
Output similar to the following appears:
FIRST_NAME LAST_NAME SALARY -------------------- ------------------------- ---------- Steven King 24000 Neena Kochhar 17000 Lex De Haan 17000 Alexander Hunold 9000 Bruce Ernst 6000 David Austin 4800 Valli Pataballa 4800 Diana Lorentz 4200 Nancy Greenberg 12008 9 rows selected.
Step 6: If Unified Auditing Is Not Enabled, Then Run a Report
Because you enabled auditing on failure for the HR Apps realm, you can generate a report to find any security violations such as the one you attempted in Step 5: Test the Realm.
-
In SQL*Plus, connect as user
SYSTEMand ensure that unified auditing is not enabled.CONNECT SYSTEM -- Or, CONNECT SYSTEM@hrpdb Enter password: password SQL> SELECT VALUE FROM V$OPTION WHERE PARAMETER = 'Unified Auditing';
If
VALUEreturnsTRUE, then you cannot complete this section. Go to "Step 7: Remove the Components for This Tutorial."If unified auditing is enabled, then you must create a unified audit policy to capture events. See Oracle Database Security Guide for information about how to create unified audit policies for Oracle Database Vault.
-
In the Database Vault Administrator page, click Home to display the home page.
-
In the Database Vault Home page, under Reports, select Database Vault Reports.
-
In the Database Vault Reports page, select Database Vault Enforcement Audit Report.
-
From the Database Vault Audit Report list, select Realm Audit Report.
-
In the Search area, from the Command menu, select Equals and in the text field, enter
SELECT. Then click Search.The report appears in the table that follows the Search region.
-
Click OK to exit the report.
Oracle Database Vault generates a report listing the type of violation (in this case, the SELECT statement entered in the previous section), when and where it occurred, the login account who tried the violation, and what the violation was.
Step 7: Remove the Components for This Tutorial
You can remove the components that you created for this tutorial if you no longer need them.
-
Drop user
SEBASTIAN.In SQL*Plus, log on as the Oracle Database Vault account manager (for example,
bea_dvacctmgr) and then dropSEBASTIANas follows:sqlplus bea_dvacctmgr -- Or, CONNECT bea_dvacctmgr@hrpdb Enter password: password DROP USER SEBASTIAN;
-
Delete the HR Apps realm.
-
In the Database Vault Home page, click Administration.
-
In the Realms page, select
HR Appsfrom the list of realms. -
Click Delete, and in the Confirmation window, click Yes.
-
-
If necessary, lock and expire the
HRaccount.ALTER USER HR ACCOUNT LOCK PASSWORD EXPIRE;