| Oracle® Auto Service Request Release 3.2 for Oracle Enterprise Linux and Solaris |
|
|
Mobi · ePub |
| Oracle® Auto Service Request Release 3.2 for Oracle Enterprise Linux and Solaris |
|
|
Mobi · ePub |
This chapter contains all procedures and other information required to manage the ASR environment.
This section provides a variety of commands and procedures for managing ASR Assets. The following diagram shows the status transition of ASR Asset:
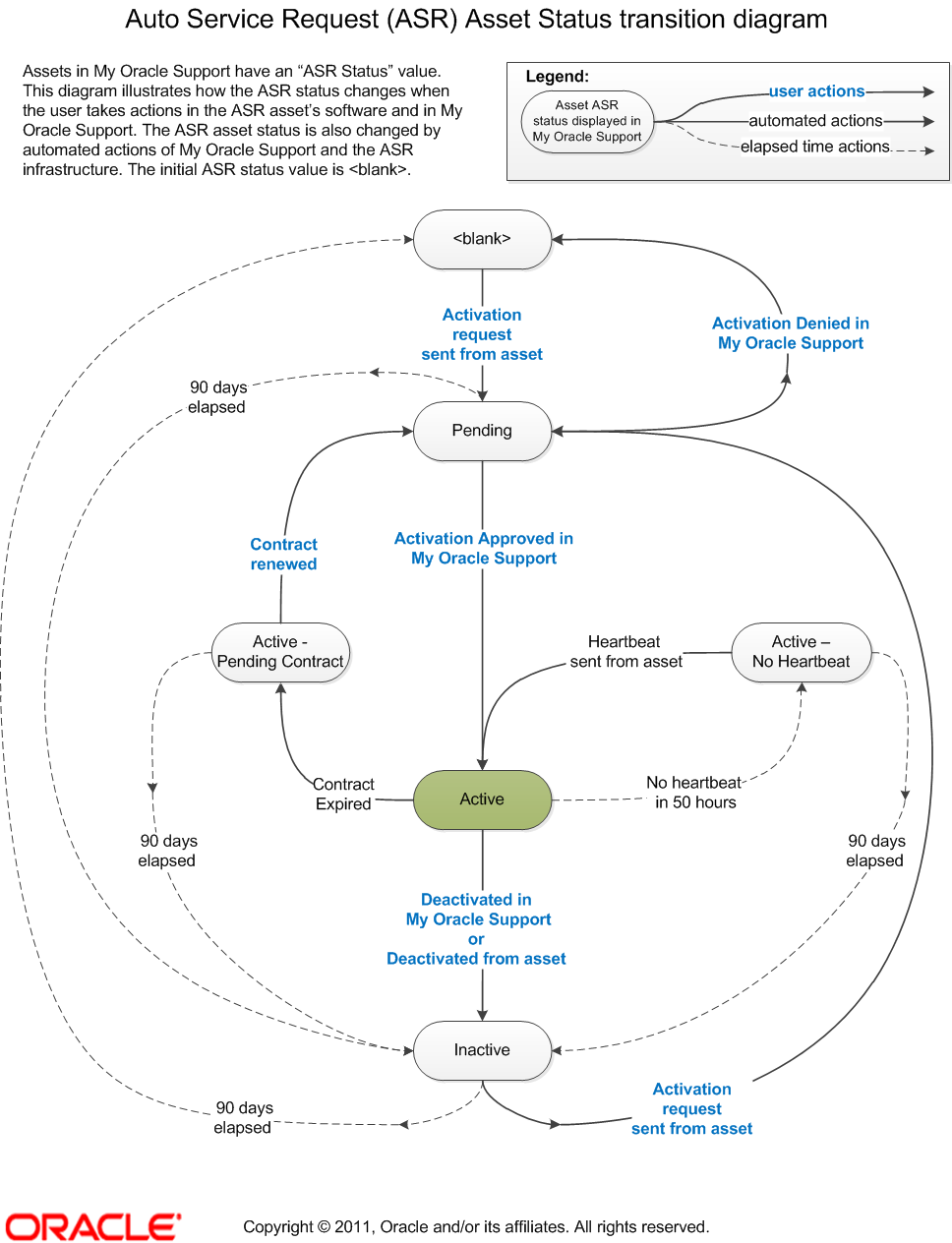
The status of any ASR Asset can be obtained by running any one of the following command options from the ASR Manager system:
asr list_asset - lists all assets associated with this ASR Manager
asr list_asset -i IP_Address_of_ASR Asset
asr list_asset -h Hostname_of_ASR Asset
asr list_asset -s Subnet_IP_Address_of_ASR Asset(s)
Note:
Theasr list_asset command accepts a comma-delimited list of IP addresses, subnets, or hostnames.The results will be similar to the following example:
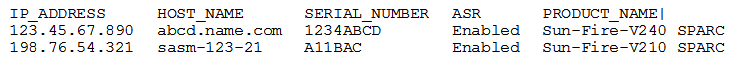
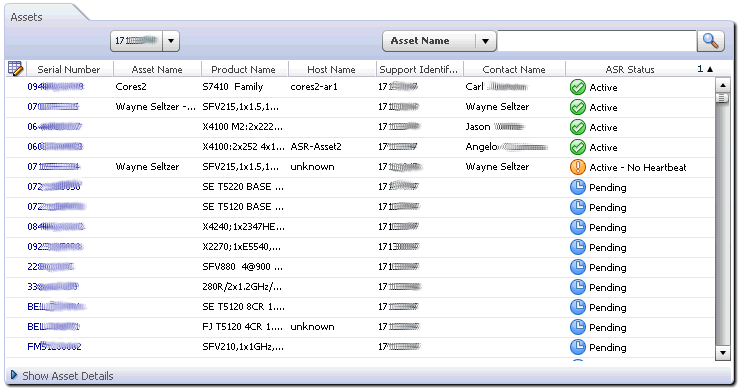
To view the status of all ASR Assets, login to My Oracle Support (https://support.oracle.com). In the My Oracle Support Dashboard, click the “More...” tab. Then select “Settings” from the menu.
In the “Settings” pane on the left of the window, select “Assets” (located under the Administrative submenu). A complete list of all ASR Assets is displayed:
The following command allows you to test the end-to-end functionality of ASR by simulating a hardware fault. The end result is an email sent to the email address of the Sun Online Account associated with the ASR installation.
Execute the asrassetbundle shell script:
If on an ASR Asset:
cd /untar_location_of_assetbundle/asrassetbundle
./asrassetmenu.sh
Note:
If you have issues finding theasrassetbundle directory, go to "Obtain the ASR Asset Bundle for non-ILOM Telemetry Sources" for more information.If on the ASR Manager system:
cd /opt/SUNWswasr/asrassetbundle ./asrassetmenu.sh
From the ASR Asset Menu, type 8.
Whether you are on an ASR Asset or the ASR Manager, enter the IP address of the ASR Manager.
Note:
Test Alerts can only be generated from a host. Test Alerts are not supported on service processors.Enter the SNMP port used to send hardware telemetry to the ASR Manager. The default port is 162.
When the test alert is sent, check the email account of the Sun Online Account associated with the ASR installation.
Note:
If this test fails on Solaris 10, be sure that the/usr/sfw/bin/snmptrap exists and Solaris netsnmp library is installed on the asset.Follow the procedures below to enable or disable ASR Asset(s). Regardless of which asset you wish to enable or disable, this action is always performed on the ASR Manager system. The most common reasons to disable ASR Asset(s) are for system maintenance or if an asset is “noisy” in terms of sending an excess of telemetry data. Disabling an ASR Asset stops it from sending hardware telemetry.
Open a terminal window and log in to the ASR Manager system as root.
Run any one of the following commands depending on your circumstance. Use the IP address or the hostname of the asset you wish to disable. If you disable the ASR Manager itself, only its telemetry will be stopped. All enabled ASR Asset(s) that send telemetry to this ASR Manager will continue, and the ASR Manager will continue to forward fault telemetry to Oracle's backend systems.
asr disable_asset -i IP_address
asr disable_asset -h hostname
asr disable_asset -s subnet(used to disable a group of assets within the subnet)
After you have disabled an ASR asset, you can re-enable it when you are ready for ASR to begin transmitting telemetry data.
Open a terminal window and log in to the ASR Manager system as root.
Run any one of the following commands depending on your circumstance. Use the IP address or the hostname of the asset you wish to enable. Once enabled, the asset will send hardware telemetry data to the ASR Manager and faults will be sent to Oracle's backend systems.
asr enable_asset -i IP_address
asr enable_asset -h hostname
asr enable_asset -s subnet(used to enable a group of assets within the subnet)
Once complete, a successfully enabled message is displayed.
To confirm the asset is enabled, you can generate a test event using either one of the following command options:
asr send_test -i IP_address
asr send_test -h hostname
The status of the test event is sent to the email address of the Sun Online Account associated with the ASR installation.
Deactivating an ASR Asset is done when you are replacing the asset or removing it entirely from the ASR system. When you deactivate an ASR Asset, ASR can no longer transmit telemetry data from this asset to Oracle.
You can deactivate/activate ASR Assets from My Oracle Support. For more information see "Review Assets in My Oracle Support".
In the "Assets" dashboard, click on the serial number of the asset you wish to deactivate/activate. The last column (ASR Status) will show the status of the asset (Active, Inactive, or Pending)

In the Asset's Details pane, click the "Deactive" button to deactivate the asset. If the asset is already deactivated, click the "Activate" button to activate it.
If necessary, you can update details about the asset (for example, change the Contact Name).
Follow these instructions to deactivate/activate an ASR Asset from the ASR Manager:
Open a terminal window and log in to the ASR Manager system as root.
Run any one of the following commands depending on your circumstance. Use the IP address or the hostname of the asset you wish to deactivate.
asr deactivate_asset -i IP_address
asr deactivate_asset -h hostname
asr deactivate_asset -s subnet(used to enable a group of assets within the subnet)
Note:
When you deactivate an ASR Asset, you cannot re-enable it. If you want to enable it again for ASR, you must re-activate it. Refer to "Activate ASR Assets".Once an asset is deactivated, you should also stop the hardware telemetry from being sent from the asset (even though the telemetry data is ignored by ASR once sent).
The procedures in this section explain how to enable or disable telemetry trap destinations on ASR Asset(s). A trap destination is where the telemetry data is sent. During ASR installation, each asset is configured by setting trap destinations from the asset system. In all cases, the trap destination specified is the ASR Manager system, which centrally collects the telemetry data sent from ASR Asset(s). Even if the ASR Manager itself is configured to send telemetry data, its trap destination must be this same ASR Manager.
Reasons for enabling traps include:
Traps were not enabled during installation.
Traps need to be enabled as part of troubleshooting tasks.
Reasons for disabling traps include:
IP address of ASR Manager changed. If this situation occurs, you need to disable the traps, then re-enable the traps with the new IP information.
Stopping the use of ASR and/or you want to minimize telemetry traffic.
Before continuing, be mindful of the following:
You should know what telemetry sources exist on any particular ASR system. Refer to "Confirm Existing Telemetry Sources".
An active ASR Manager should already be fully installed. Refer to "Install the ASR Manager" on page 3-1.
Ideally, but not required, at least one ASR Asset should already be fully installed. Refer to "Configure and Manage ASR Assets" on page 4-1.
Follow the procedure below to add or remove a trap destination for systems using Solaris FMA telemetry.
To add a Solaris FMA telemetry trap, go to "Enable FMA Telemetry".
To remove a trap destination, make sure you are logged in as root on the system whose telemetry trap you wish to remove. This could be either an ASR Manager or an ASR Asset system. Keep in mind that this process stops telemetry from being sent to the ASR Manager. It does not remove the telemetry software itself nor disables its operation (for example, FMA).
Go to the directory where you previously untarred the ASR Asset Bundle file, and then go to the specific ASR Asset Bundle directory, if needed. For example:
If on an ASR Asset:
cd /file_copy_location/asrassetbundle
If on the ASR Manager system:
cd /opt/SUNWswasr/asrassetbundle
Note:
Refer to "Obtain the ASR Asset Bundle for non-ILOM Telemetry Sources" if you have issues locating theasrassetbundle directory and/or asrassetmenu.sh script (below).Launch the ASR Asset Menu:
./asrassetmenu.sh Welcome to the ASR asset menu ---------------------------------------------- 1) Check system for ASR qualifications 2) Add a trap-destination to SunMC agent 3) Add a trap-destination to FMA agent 4) Remove a trap-destination from SunMC agent 5) Remove a trap-destination from FMA agent 6) List SunMC agent trap-destinations 7) List FMA agent trap-destinations 8) Test event to verify ASR connectivity 9) Exit
Select 5 to remove the FMA trap destination.
When prompted, “. . . enter the number of the trap-destination to remove,” enter the list number of the IP address of the ASR Manager.
Note:
If you are removing an FMA trap, enter the listed IP address with the port number (for example, 192.20.77.192:162).The trap is then removed from the system and all telemetry sent from Solaris FMA to the ASR Manager is stopped.
To add or remove an ILOM trap, refer to "Enable ILOM Telemetry". This referenced procedure can be used to add or remove traps. If removing a trap, use the following parameters:
If using the ILOM GUI interface, either remove the entire alert rule destination or set the Level parameter to Disable.
If using the command line interface, set the Level parameter to Disable. Also, be sure to specify the correct alert rule (1 to 15) to disable.
To add or remove telemetry traps on systems that have XSCF telemetry (Sun M-Series), refer to "Enable M-Series XSCF Telemetry". This referenced procedure can be used to add or remove traps.
This section provides a variety of procedures that can be used to manage the ASR environment as a whole.
When you installed ASR, you registered it with the transport server (transport.sun.com) using your Sun Online Account. The registration is performed on the ASR Manager system, as is an unregister if required. Reasons for unregistering ASR can include the following:
If your current Sun Online Account (SOA) is no longer valid, as in a case when the email contact is no longer associated with the company. The email address associated with the SOA login is used by ASR to send a variety of ASR notifications, such as status reports. In this case, ASR should be unregistered and then re-registered with the new Sun Online account information.
If the server and ASR handshake becomes corrupted.
To unregister ASR:
From the ASR Manager system, run:
/opt/SUNWswasr/bin/asr unregister
Once unregistered, ASR cannot send hardware fault telemetry to Oracle's backend systems.
To register ASR, refer to "Register the ASR Manager" for instructions.
This section explains how to stop and start your complete ASR environment. There are several reasons why you may want to do this, as listed below:
Telemetry rules or other image upgrade to ASR.
If you change network and port settings used by ASR. These changes are typically made in the SASM config.ini file:
/var/opt/SUNWsasm/configuration/config.ini
Note:
On Solaris, SASM startup/restart is done via SMF service.Follow the procedure below to stop ASR and SASM.
Note:
Stopping SASM is optional, depending upon what your purpose is. If changes are made to the SASMconfig.ini file, for example, you must stop and restart SASM. In conformance with best practices, SASM should be stopped whenever ASR is stopped, and started whenever ASR is started.Open a terminal window and log in as root on the ASR Manager system.
Run the following commands:
For Solaris:
/opt/SUNWasr/bin/asr stop-instance (stops ASR)svcadm disable sasm (stops SASM)
For OEL:
/opt/SUNWasr/bin/asr stop-instance (stops ASR)/opt/SUNWsasm/bin/sasm stop-instance (stops SASM)
Once ASR is stopped, you can perform the desired maintenance tasks. Once complete, continue to the next section to restart ASR.
Follow the procedure below to restart ASR and SASM:
Open a terminal window and log in as root on the ASR Manager system.
Run the following commands:
For Solaris:
svcadm enable sasm (starts SASM)/opt/SUNWasr/bin/asr start-instance (starts ASR)
For OEL:
/opt/SUNWsasm/bin/sasm start-instance (starts SASM)/opt/SUNWasr/bin/asr start-instance (starts ASR)
Be sure that ASR can send information to the transport.sun.com servers by running the following command:
asr test_connection
This section describes the types of emails generated by ASR. See "ASR Email Examples" for examples. Email generated by ASR is sent to:
The email address of the Sun Online Account (SOA) associated with the ASR installation.
The contact assigned to the asset in My Oracle Support.
A distribution list assigned to the asset in My Oracle Support (optional)
The types of email generated by ASR include:
ASR Activation Email and Status of ASR Assets
An email indicating success or failure of ASR activation is sent. Instructions for any user action is included as needed. ASR Asset status is available in My Oracle Support.
ASR Service Request Email
Service Request emails are generated whenever a Service Request is created at Oracle that results from a hardware fault detection on any of your ASR-enabled systems. Failure emails indicate what issues may have prevented a Service Request from being created upon receipt of a hardware fault from ASR.
All Service Request emails are sent to the Primary and Preferred Technical Contact associated with the system reporting a potential fault. For more on how this contact is established or changed, refer to "Review Assets in My Oracle Support".
Note:
email sent from Blade ASR Assets have a different email format.Heartbeat Failure Notification
If the ASR Heartbeat detects a communications error to Oracle, an email is sent. The ASR Heartbeat should have been setup in a cron job during ASR installation, as discussed in "Set Up Crontab".
Fault Rules Out of Date Email
This email is sent if ASR detects that its fault rules are out of date. See "Set Up Crontab" for more information on fault rules.
Note:
If the asr heartbeat is disabled in crontab, you will not be notified, via email, if your ASR fault rules are out of date with the most current release. To be sure your fault rules are current, you can run theasr update_rules command from the ASR Manager system.ASR Backup
Verify all information is in the database that is activated. Run:
/opt/SUNWswasr/bin/asr list_asset
Stop SASM so that data does not change in middle of backup:
For Solaris, run: svcadm disable sasm
For OEL, run: /opt/SUNWsasm/bin/sasm stop-instance
Back up the database directory. Run:
tar -cjf db.tar.bz /var/opt/SUNWsasm/db
Create a backup of the ASR configuration. Run:
tar -cjf configuration.tar.bz /var/opt/SUNWsasm/configuration
Copy both db.tar.bz and configuration.tar.bz files to their proper backup destination.
Restart SASM. Run:
For Solaris, run: /opt/SUNWsasm/bin/svcadm enable sasm
For OEL, run: /opt/SUNWsasm/bin/sasm start-instance
ASR Restore
Install the ASR plugin and SASM:
For Solaris, run:
pkgadd -d SUNWsasm.version_num.pkg pkgadd -d SUNWswasr.version_num.pkg
For OEL, run:
rmp -i SUNWsasm.version_num.rpm rpm -i SUNWswasr.version_num.rpm
Note:
Download and install the latest packages to upgrade to the latest version of the ASR Manager. See "Download the SASM and ASR Packages" for more information.Stop SASM to restore files:
For Solaris, run: svcadm disable sasm
For OEL, run: /opt/SUNWsasm/bin/sasm stop-instance
Restore the files from backup:
Remove files /var/opt/SUNWsasm/configuration and /var/opt/SUNWsasm/db
Copy backup data to /var/opt/SUNWsasm/
Extract the tar files (both Solaris and OEL):
tar -xvf configuration.tar.bz tar -xvf db.tar.bz
Verify the files have been correctly extracted. Run:
ls /var/opt/SUNWsasm/
Restart SASM. Run:
For Solaris, run: svcadm enable sasm
For OEL, run: /opt/SUNWsasm/bin/sasm start-instance
Register the backup configuration. Run:
/opt/SUNWswasr/bin/asr register
Note:
If you are running the latest version of ASR (or at least ASR 2.6) and if host name of the restored ASR Manager and Sun Online Account (SOA) login have not changed, then you can stop here. Steps 7 and 8 are not required.Remove old entries from the My Oracle Support backend to associate correctly. Run:
/opt/SUNWswasr/bin/asr send_deactivations -a
Add new entries to the My Oracle Support backend. Run:
/opt/SUNWswasr/bin/asr send_activations -a
List ASR Assets. Run:
asr list_asset
This section provides the instructions for networking-related tasks for ASR operations.
The following table explains the network ports used by ASR:
| Source | Destination | Protocol | Port | Description |
|---|---|---|---|---|
| ASR Manager | ASR Backend (Oracle) | https | 443 | For sending telemetry messages to the ASR backend systems at Oracle. |
| ASR Manager | ASR Asset | http | 6481 | Service Tags listener for Asset activation |
| ASR Asset | ASR Manager | snmp udp | 162 | For sending telemetry messages to the ASR Manager. |
| ASR Manager | ASR Asset | snmp (get) udp | 161 | FMA enrichment for getting additional diagnostics information. |
You can change the default SNMP port on the ASR Manager by editing the /var/opt/SUNWsasm/configuration/config.ini file as follows:
Change com.sun.svc.container.snmp.port=162 to listen on whatever port is appropriate. 162 is the default.
Restart SASM:
svcadm restart sasm
Verify the change:
/opt/SUNWsasm/bin/sasm getprop | grep com.sun.svc.container.snmp.port
This command will return the new port value that you entered.
This procedure should be used to enable network communications in cases where you have a SOCKS proxy server mediating network traffic between the ASR Manager and the internet. For other proxy server types, you need to re-register ASR to set-up the proxy server information, as discussed in "Register the ASR Manager".
Open a terminal window and log in as root to the ASR Manager system.
Using an editor of your choice (such as vi), edit the following file by changing the SOCKS proxy information as needed:
/var/opt/SUNWsasm/configuration/config.ini
The following entries must be made within the file. Contact a Network Administrator if needed.
socksProxyHost= socksProxyPort= java.net.socks.username= java.net.socks.password=
Restart ASR using the following command:
For Solaris: svcadm restart sasm
For OEL, run:
/opt/SUNWsasm/bin/sasm stop-instance /opt/SUNWsasm/bin/sasm start-instance
To verify the changes, run the following command:
cat /var/opt/SUNWsasm/configuration/config.ini | grep socks
The following command can be used to confirm that the network parameters used by SASM to connect to Oracle's ASR backend systems are properly set:
grep transport.root /var/opt/SUNWsasm/configuration/config.ini
The ASR transport hostname is displayed and will be similar to the results shown below:
com.sun.svc.container.transport.root= https://transport.sun.com
The following procedure can be used to confirm proper communication between the ASR Manager and Oracle's ASR backend systems.
Complete one of the following steps from the ASR Manager to verify connectivity to Oracle's ASR backend systems:
telnet transport.sun.com 443
If you have a web browser, go to https://transport.sun.com. The web page should indicate that the Data Transport Service is operating.
If a web browser is unavailable, or you are in Europe, the Middle East, or Africa regions, run one the following commands from a terminal window:
wget https://transport.sun.comor wget https://transport.sun.co.uk (for Europe, Middle East, or Africa Regions)
If the results of the above commands do not indicate the Data Transport Service is operating, you must resolve your network connection issue. Listed below are possible resolutions:
The issue could be a DNS problem, or you might need to add transport.sun.com to the /etc/hosts file.
You may need to contact your network administrator for assistance. Refer to "Oracle Auto Service Request Configuration Requirements" for the specific ASR network requirements.
If you use a proxy server, the issue could be that the proxy information has not yet been configured to ASR and SASM. This is done by registering ASR, as discussed in the following procedure.
Other environments are set up to use different enterprise monitoring systems (e.g., IBM Tivoli, HP OpenView, etc.). Beginning with ASR 3.0, integration with My Oracle Support allows sending ASR service-request information to these systems. Once installed and properly configured, ASR provides the following integration features with enterprise monitoring systems:
Ability to configure SNMP trap destination from SASM ASR to enterprise monitoring systems.
Send case creation and test alert messages to enterprise monitoring systems.
New ASR MIB that provides the data model of ASR case creation notification.
Examples of enterprise-monitoring systems include:
IBM Tivoli
HP OpenView
BMC Patrol
Unicenter
xVM Ops Center
Any monitoring tool that can receive an SNMP v2c trap
During installation of the ASR software package, the SNMP trap destination can be configured from the SASM host to monitoring systems. Once the ASR-capable assets are activated, ASR is designed to generate a service request after specific faults are detected. Once the service request is opened, the Oracle Support coverage and response times are delivered in accordance with your Oracle Premier Support or Warranty Contract.
Note:
Because of ASR 3.0 integration with My Oracle Support, there are changes in the Service Request format. The service request number format in the notification trap is not correct if you are using any version older than ASR 3.0 manager. See "Upgrade ASR" for instructions on upgrading to the latest version of ASR.The SASM ASR Plugin polls the ASR backend whenever a fault event or test alert occurred and updates its local database with service request or test alert information. Once the service request/test alert information is available to the SASM ASR Plugin, it sends an SNMP v2c trap to the enterprise monitoring systems and include the following service request/test alert data defined in the ASR MIB:
|
|
Follow the procedure below to configure trap files for ASR:
Set ASR notification trap destination:
/opt/SUNWswasr/bin/asr set_notification_trap -i <ip_address>-p <portNumber> -c <community string>
For example:
/opt/SUNWswasr/bin/asr set_notification_trap -i 127.0.0.1 -p 162 -c public
Note:
Port “162” in the example is the destination port on your monitoring system. The notification trap will be sent only when a new service request (SR) is created successfully, and also when the test SR (test SNMP alert from the ASR asset menu) is successfulShow ASR notification trap destination:
asr show_notification_trap
Delete ASR notification trap destination:
asr delete_notification_trap
The SUN-ASR-NOTIFICATION-MIB file is located at:
/var/opt/SUNWsasm/configuration/SUN-ASR-NOTIFICATION-MIB.mib
| Data Element | Description |
|---|---|
sunAsrSrHostname |
Hostname of the system for which the Service Request was created. |
sunAsrSrIpAddress |
IP address of the system for which the Service Request was created. |
sunAsrSrSerialNumber |
Product serial number of the system for which the Service Request was created. For chassis and blade systems, chassis serial number is used. |
sunAsrSrPlatformType |
Product Type of the system for which the Service Request was created. |
sunAsrSrCreationDateTime |
Date and time when the Service Request was created. |
sunAsrSrFaultDetectionDateTime |
Date and time when the fault was generated. |
sunAsrSrCreationStatus |
Status indicating the processing of Service Request creation. |
sunAsrSrAdditionalInfo |
Additional information associated with the fault can be added as name/value pairs. For example:
|
sunAsrSrFaultSummary |
Brief summary of the fault for which the Service Request was created. |
sunAsrSrKnowledgeLink |
Link to a knowledge article for the fault that was reported. |
sunAsrSrNumber |
Service request number |
sunAsrSrLink |
URL for accessing the Service Request information. |
sunAsrSrSeverity |
Severity of the Service Request opened for the reported fault. |
sunAsrSrName |
|
sunAsrSrTelephone |
Telephone number of Customer Contact associated with the Serial Number of the Device for which the Service Request was created. |
sunAsrSrEmail |
Email address of Customer Contact associated with the Serial Number of the Device for which the Service Request was created. |
The following procedure explains how to remove ASR completely, or partially for the purpose of an upgrade.
Important: If you wish to remove ASR for the long term, start with the procedures below. If you are removing ASR for a short time, or for an ASR upgrade, start at step 6.
From all ASR Asset systems, remove telemetry traps that send hardware telemetry to the ASR Manager. Follow these steps:
Identify what telemetry sources reside on the systems. If uncertain, refer to "Telemetry Sources: Overview and Check".
Remove the telemetry traps. Refer to Add/Remove Telemetry Traps from ASR Asset(s). If you are collecting telemetry from the ASR Manager itself, be sure to remove those traps as well.
Deactivate all ASR Asset(s). Refer to Deactivate/Activate ASR Assets.
Deactivate the ASR Manager. Refer to Deactivate/Activate ASR Assets.
Unregister ASR. Refer to Unregister ASR.
Important:
If you are using other SASM plug-ins (for example SFT), the SASM transport service used by these plug-ins will be unregistered as part of this process. Consult your plug-in documentation to re-register the SASM transport service, if needed.Remove the ASR package from the ASR Manager system:
For Solaris: pkgrm SUNWswasr
For OEL: rpm -e SUNWswasr
Remove the SASM package from the ASR Manager system. Removing this package is optional and is often done to reduce system overhead. If you have other applications running under SASM, do not remove it. Refer to "Check for SASM Installation and Version" for more information on SASM.
For Solaris: pkgrm SUNWsasm
For OEL: rpm -e SUNWsasm
If you never intend to use ASR and SASM again, run the following command to remove leftover artifacts (SASM log files, ASR asset database, configuration files, etc.):
Warning:
This command will remove all asset activation, configuration, and ASR log file data. Only remove these files if you want to permanently remove ASR from the system or node.rm -r /var/opt/SUNWsasm
After completing the steps above, the uninstall of ASR is complete.
Follow the steps below to upgrade ASR:
Uninstall ASR. Refer to "Uninstall ASR".
Obtain the new ASR and SASM packages. Refer to "Download the SASM and ASR Packages".
Install the new SASM and ASR packages. If you did not remove SASM during the uninstall of ASR, you can still install the new SASM package.
Install SASM. Refer to "Install the SASM Package".
Install ASR. Refer to "Install the ASR Package". Be sure to register and activate the ASR Manager, as explained in the referenced instructions.