10 Integrating Oracle Database Vault with Other Oracle Products
You can integrate Oracle Database Vault with Enterprise User, Transparent Data Encryption (TDE), Oracle Virtual Private Database, Oracle Label Security, and Oracle Data Guard.
Topics:
-
Integrating Oracle Database Vault with Enterprise User Security
-
Configuring Oracle Database Vault Accounts as Enterprise User Accounts
-
Integration of Oracle Database Vault with Transparent Data Encryption
-
Integrating Oracle Database Vault with Oracle Label Security
Integrating Oracle Database Vault with Enterprise User Security
You can integrate Oracle Database Vault with Oracle Enterprise User Security.
Topics:
About Integrating Oracle Database Vault with Enterprise User Security
Enterprise User Security enables you to centrally manage database users and authorizations in one place. It is combined with Oracle Identity Management and is available in Oracle Database Enterprise Edition.
In general, to integrate Oracle Database Vault with Oracle Enterprise User Security, you configure the appropriate realms to protect the data that you want to protect in the database.
After you define the Oracle Database Vault realms as needed, you can create a rule set for the Enterprise users to allow or disallow their access.
See Also:
Oracle Database Enterprise User Security Administrator's Guide for more information about Enterprise User SecurityConfiguring an Enterprise User Authorization
To configure an Enterprise User authorization, you must create an Oracle Database Vault rule set to control the user access.
-
Create a rule to allow or disallow user access.
Follow the instructions in "Creating a Rule to Add to a Rule Set" to create a new rule. In the Create Rule page, enter the following PL/SQL in the Rule Expression field:
SYS_CONTEXT('USERENV','AUTHENTICATED_IDENTITY') = 'user_domain_name'Replace
user_domain_namewith the domain, for example:SYS_CONTEXT('USERENV','AUTHENTICATED_IDENTITY') = 'myserver.us.example.com' -
Add this rule to a new rule set.
"Creating a Rule Set" explains how to create a new rule set, including how to add an existing rule to it.
-
Add this rule set to the realm authorization for the data that you want to protect.
"About Realm Authorization" explains how to create realm authorizations. In the Authorization Rule Set list, select the rule set that you created in Step 2. Afterward, the realm authorization applies to all users.
Configuring Oracle Database Vault Accounts as Enterprise User Accounts
You can configure existing Oracle Database Vault user accounts as enterprise user accounts.
-
Log into the database instance as a user who has been granted the
CREATE ROLEsystem privilege.For example:
sqlplus system Enter password: password -
In a multitenant environment, connect to the appropriate pluggable database (PDB).
For example:
CONNECT SYSTEM@hrpdb Enter password: passwordTo find the available PDBs, query the
DBA_PDBSdata dictionary view. To check the current PDB, run theshow con_namecommand. -
Create a global role for the
DV_OWNERrole and a global role for theDV_ACCTMGRrole.For example:
CREATE ROLE g_dv_owner IDENTIFIED GLOBALLY; CREATE ROLE g_dv_acctmgr IDENTIFIED GLOBALLY;
-
Connect as a user who has been granted the
DV_OWNERrole.For example:
CONNECT dbv_owner -- Or, CONNECT dbv_owner@hrpdb Enter password: password
-
Grant the
DV_OWNERrole to the globalDV_OWNERrole.GRANT DV_OWNER TO g_dv_owner;
-
Connect as a user who has been granted the
DV_ACCTMGRrole.For example:
CONNECT dbv_acctmgr -- Or, CONNECT dbv_acctmgr@hrpdb Enter password: password
-
Grant the
DV_ACCTMGRrole to the globalDV_ACCTMGRrole.GRANT DV_ACCTMGR TO g_dv_acctmgr;
-
Connect as user
SYSwith theSYSDBAadministrative privilege.CONNECT SYS AS SYSDBA -- Or, CONNECT SYS@hrpdb AS SYSDBA Enter password: password
-
Temporarily grant the
DV_ACCTMGRuser who will import the Database Vault users into OID theCREATE TABLEprivilege and theSELECT_CATALOG_ROLErole.GRANT CREATE TABLE, SELECT_CATALOG_ROLE TO dbv_acctmgr;
-
From the command line, run the User Migration Utility (
UMU) to import the Database Vault accounts into Oracle Internet Directory (OID).The following example imports the Database Vault accounts
leo_dvownerandbea_dvacctmgrinto OID. TheDV_ACCTMGRuser is specified for theDBADMINsetting.$ORACLE_HOME/rdbms/bin/umu PHASE=ONE DBADMIN=dbv_acctmgr:password ENTADMIN=cn=jane_ent_admin,dc=example,dc=com:password USERS= LIST DBLOCATION=example.com:7777:orcl DIRLOCATION=example.com:636 USERSLIST=leo_dvowner:bea_dvacctmgr MAPSCHEMA=PRIVATE CONTEXT=CONTEXT="c=Users, c=us" KREALM=EXAMPLE.COM $ORACLE_HOME/rdbms/bin/umu PHASE=TWO DBADMIN=dbv_acctmgr:password ENTADMIN=cn=jane_ent_admin,dc=example,dc=com:password DBLOCATION=example.com:7777:orcl DIRLOCATION=example.com:636
By default, errors are written to the
$ORACLE_HOME/network/log/umu.logfile. -
From the Oracle Internet Directory Self Service Console (
http://hostname:port/oiddas/), grant the globalDV_OWNERandDV_ACCTMGRroles (for example,g_dv_ownerandg_dv_acctmgr) to the enterprise user Database Vault accounts.See the example of creating enterprise users in Oracle Database Enterprise User Security Administrator's Guide for a demonstration of creating an enterprise role from a global role and then granting this role to a user.
-
From SQL*Plus, as user
SYSwith theSYSDBAadministrative privilege, revoke theCREATE TABLEandSELECT_CATALOG_ROLErole from theDV_ACCTMGRuser.REVOKE CREATE TABLE, SELECT_CATALOG_ROLE FROM dbv_acctmgr;
See Also:
Oracle Database Enterprise User Security Administrator's Guide for detailed information about the User Migration UtilityIntegration of Oracle Database Vault with Transparent Data Encryption
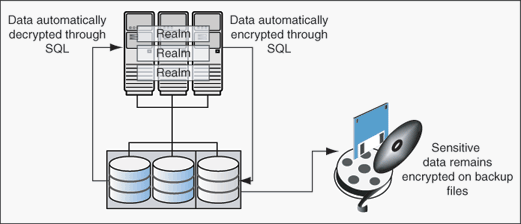
Transparent Data Encryption complements Oracle Database Vault in that it provides data protection when the data leaves the secure perimeter of the database.
With Transparent Data Encryption, a database administrator or database security administrator can simply encrypt columns with sensitive content in application tables, or encrypt entire application tablespaces, without any modification to the application. For detailed information about Transparent Data Encryption, see Oracle Database Advanced Security Guide.
If a user passes the authentication and authorization checks, Transparent Data Encryption automatically encrypts and decrypts information for the user. This way, you can implement encryption without having to change your applications.
Once you have granted the Transparent Data Encryption user the appropriate privileges, then Transparent Data Encryption can be managed as usual and be used complimentary to Database Vault.
Figure 10-1 shows how Oracle Database Vault realms handle encrypted data.
Figure 10-1 Encrypted Data and Oracle Database Vault
Description of "Figure 10-1 Encrypted Data and Oracle Database Vault"
Attaching Factors to an Oracle Virtual Private Database
You can attach factors to an Oracle Virtual Private Database.
-
Define a Virtual Private Database policy predicate that is a PL/SQL function or expression.
-
For each function or expression, use the
DVF.F$PL/SQL function that is created for each factor.
See Also:
Oracle Database Security Guide for more information about Oracle Virtual Private DatabaseIntegrating Oracle Database Vault with Oracle Label Security
Oracle Database Vault enables you to integrate Database Vault with Oracle Label Security, and provides reports and data dictionary views to check the integration.
Topics:
-
How Oracle Database Vault Is Integrated with Oracle Label Security
-
Requirements for Using Oracle Database Vault with Oracle Label Security
-
Using Oracle Database Vault Factors with Oracle Label Security Policies
-
Tutorial: Integrating Oracle Database Vault with Oracle Label Security
How Oracle Database Vault Is Integrated with Oracle Label Security
When you integrate Oracle Database Vault with Oracle Label Security, it means that you can assign an Oracle Label Security label to an Oracle Database Vault factor identity.
In Oracle Label Security, you can restrict access to records in database tables or PL/SQL programs. For example, Mary may be able to see data protected by the HIGHLY SENSITIVE label, an Oracle Label Security label on the EMPLOYEE table that includes records that should have access limited to certain managers. Another label can be PUBLIC, which allows more open access to this data.
In Oracle Database Vault, you can create a factor called Network, for the network on which the database session originates, with the following identities:
-
Intranet: Used for when an employee is working on site within the intranet for your company.
-
Remote: Used for when the employee is working at home from a VPN connection.
You then assign a maximum session label to both. For example:
-
Assign the Intranet identity to the HIGHLY SENSITIVE Oracle Label Security label.
-
Assign the Remote identity to the PUBLIC label.
This means that when Mary is working at home using her VPN connection, she has access only to the limited table data protected under the PUBLIC identity. But when she is in the office, she has access to the HIGHLY SENSITIVE data, because she is using the Intranet identity. "Tutorial: Integrating Oracle Database Vault with Oracle Label Security" provides an example of how to accomplish this type of integration.
In a non-unified auditing environment, you can audit the integration with Oracle Label Security by using the Label Security Integration Audit Report. Oracle Database Vault writes the audit trail to the DVSYS.AUDIT_TRAIL$ table. If unified auditing is enabled, then you can create audit policies to capture this information, as described in Oracle Database Security Guide.
See Also:
-
Appendix A, "Auditing Oracle Database Vault" for information about how auditing works for Database Vault
-
"Oracle Database Vault Oracle Label Security APIs" for information about Database Vault APIs that you can use to integrate Database Vault with Oracle Label Security
-
"Related Reports and Data Dictionary Views" for information about reports that you can run on the Oracle Database Vault and Oracle Label Security integration
-
Oracle Label Security Administrator's Guide for more information about Oracle Label Security labels
Requirements for Using Oracle Database Vault with Oracle Label Security
You must fulfill specific requirements in place before you use Oracle Database Vault with Oracle Label Security.
-
Oracle Label Security is licensed separately. Ensure that you have purchased a license to use it.
-
Before you install Oracle Database Vault, you must have already installed Oracle Label Security.
-
The installation process for Oracle Label Security creates the
LBACSYSuser account. As a user who has been granted theDV_ACCTMGRrole, unlock this account and grant it a new password. For example:sqlplus bea_dvacctmgr -- Or, sqlplus bea_dvacctmgr@hrpdb for a PDB Enter password: password ALTER USER LBACSYS ACCOUNT UNLOCK IDENTIFIED BY password;
Replace
passwordwith a password that is secure. See Oracle Database Security Guide for the minimum requirements for creating passwords. -
If you plan to use the
LBACSYSuser account in Oracle Enterprise Manager, then log into Enterprise Manager as userSYSwith theSYSDBAadministrative privilege, and grant this user theSELECT ANY DICTIONARYandSELECT_CATALOG_ROLEsystem privileges. -
Ensure that you have the appropriate Oracle Label Security policies defined. For more information, see Oracle Label Security Administrator's Guide.
-
If you plan to integrate an Oracle Label Security policy with a Database Vault policy, then ensure that the policy name for Oracle Label Security is less than 24 characters. You can check the names of Oracle Label Security policies by querying the
POLICY_NAMEcolumn of theALL_SA_POLICIESdata dictionary view.
Using Oracle Database Vault Factors with Oracle Label Security Policies
To enhance security, you can integrate Oracle Database Vault factors with Oracle Label Security policies.
Topics:
-
About Using Oracle Database Vault Factors with Oracle Label Security Policies
-
Configuring Factors to Work with an Oracle Label Security Policy
About Using Oracle Database Vault Factors with Oracle Label Security Policies
Oracle Database Vault controls the maximum security clearance for a database session by merging the maximum allowable data for each label in a database session by merging the labels of Oracle Database Vault factors that are associated to an Oracle Label Security policy.
In brief, a label acts as an identifier for the access privileges of a database table row. A policy is a name associated with the labels, rules, and authorizations that govern access to table rows. See Oracle Label Security Administrator's Guide for more information about row labels and policies.
Configuring Factors to Work with an Oracle Label Security Policy
You can define factors that contribute to the maximum allowable data label of an Oracle Label Security policy.
-
From Cloud Control, log into Oracle Database Vault Administrator as a user who has been granted the
DV_OWNERorDV_ADMINrole."Logging into Oracle Database Vault" explains how to log in.
-
Make the user
LBACSYSaccount an owner of the realm that contains the schema to which a label security policy has been applied.This enables the
LBACSYSaccount to have access to all the protected data in the realm, so that it can properly classify the data.The
LBACSYSaccount is created in Oracle Label Security using the Oracle Universal Installer custom installation option. Before you can create an Oracle Label Security policy for use with Oracle Database Vault, you must makeLBACSYSan owner for the realm you plan to use. See "About Realm Authorization" for more information. -
Authorize the schema owner (on which the label security policy has been applied) as either a realm participant or a realm owner.
-
In the Administration page, under Database Vault Components, click OLS Integration.
Description of the illustration ols_policies_integration.gif
-
In the Label Security Policies page:
-
To register a new label security policy with Database Vault, click Create.
-
To edit an existing label security policy that has been registered with Database Vault, select it from the list and then click Edit.
-
-
Enter the following settings:
-
Label Security Policy: From the list, select the Oracle Label Security policy that you want to use.
-
Algorithm: Optionally change the label-merging algorithm for cases when Oracle Label Security has merged two labels. In most cases, you may want to select LII - Minimum Level/Intersection/Intersection. This setting is the most commonly used method that Oracle Label Security administrators use when they want to merge two labels. This setting provides optimum flexibility when your applications must determine the resulting label that is required when combining two data sets that have different labels. It is also necessary for situations in which you must perform queries using joins on rows with different data labels.
For more information on these label-merging algorithms, see Oracle Label Security Administrator's Guide. If you want to use the
DBMS_MACADMpackage to specify a merge algorithm, see Table 18-3, "Oracle Label Security Merge Algorithm Codes" for a full listing of possible merge algorithms. -
Label Security Policy Factors: In the Available Factors list under Label Security Policy Factors, select the factor that you want to associate with the Oracle Label Security policy. Then click Move to move the factor to the Selected Factors list. You can select multiple factors by holding down the Ctrl key as you click each factor that you want to select.
-
-
Click OK.
The policy is listed in the Label Security Policies Integration page.
-
Label the factor identities using the labels for the policy.
"Adding an Identity to a Factor" provides detailed information.
Note:
If you do not associate an Oracle Label Security policy with factors, then Oracle Database Vault maintains the default Oracle Label Security behavior for the policy.Tutorial: Integrating Oracle Database Vault with Oracle Label Security
This tutorial shows how you can integrate Oracle Database Vault with Oracle Label Security to grant two administrative users who normally have the same privileges different levels of access.
Topics:
-
Step 3: Create Oracle Database Vault Rules to Control the OLS Authorization
-
Step 4: Update the ALTER SYSTEM Command Rule to Use the Rule Set
About This Tutorial
You can use Oracle Database Vault factors with Oracle Label Security and Oracle Virtual Private Database (VPD) technology to restrict access to sensitive data.
You can restrict this data so that it is only exposed to a database session when the correct combination of factors exists, defined by the security administrator, for any given database session.
Step 1: Create Users for This Tutorial
You must create two administrative users for this tutorial.
-
Log into the database instance as a user who has been granted the
DV_ACCTMGRrole.For example:
sqlplus bea_dvacctmgr Enter password: password -
In a multitenant environment, connect to the appropriate PDB.
For example:
CONNECT bea_dvacctmgr@hrpdb Enter password: passwordTo find the available PDBs, query the
DBA_PDBSdata dictionary view. To check the current PDB, run theshow con_namecommand. -
Create the following local users:
GRANT CREATE SESSION TO mdale IDENTIFIED BY password CONTAINER = CURRENT; GRANT CREATE SESSION TO jsmith IDENTIFIED BY password CONTAINER = CURRENT;
Replace
passwordwith a password that is secure. See Oracle Database Security Guide for the minimum requirements for creating passwords. -
Connect as a user who can grant system privileges and who has been granted the owner authorization for the Oracle System Privilege and Role Management realm, and then grant administrative privileges to users
mdaleandjsmith.CONNECT dba_psmith -- Or, CONNECT dba_psmith@hrpdb Enter password: password GRANT DBA TO mdale, jsmith;
At this stage, users
mdaleandjsmithhave identical administrative privileges.
Step 2: Create the Oracle Label Security Policy
Next, you are ready to create the Oracle Label Security policy and grants users the appropriate privileges for it.
-
In SQL*Plus, connect as the Oracle Label Security administrator,
LBACSYS.CONNECT LBACSYS -- Or, CONNECT LBACSYS@hrpdb Enter password: password
If user
LBACSYSis locked and expired, connect as the Database Vault Account Manager, unlock and unexpire theLBACSYSaccount, and then log back in asLBACSYS.For example:
CONNECT bea_dvacctmgr -- Or, CONNECT bea_dvaccmgr@hrpdb Enter password: password ALTER USER LBACSYS ACCOUNT UNLOCK IDENTIFIED BY password; CONNECT LBACSYS Enter password: password
-
Create a new Oracle Label Security policy:
EXEC SA_SYSDBA.CREATE_POLICY('PRIVACY','PRIVACY_COLUMN','NO_CONTROL'); -
Create the following levels for the
PRIVACYpolicy:EXEC SA_COMPONENTS.CREATE_LEVEL('PRIVACY',2000,'S','SENSITIVE'); EXEC SA_COMPONENTS.CREATE_LEVEL('PRIVACY',1000,'C','CONFIDENTIAL'); -
Create the PII compartment.
EXEC SA_COMPONENTS.CREATE_COMPARTMENT('PRIVACY',100,'PII','PERS_INFO'); -
Grant users
mdaleandjsmiththe following labels:EXEC SA_USER_ADMIN.SET_USER_LABELS('PRIVACY','mdale','S:PII'); EXEC SA_USER_ADMIN.SET_USER_LABELS('PRIVACY','jsmith','C');User
mdaleis granted the more sensitive label, Sensitive, which includes the PII compartment. Userjsmithgets the Confidential label, which is less sensitive.
Step 3: Create Oracle Database Vault Rules to Control the OLS Authorization
After you have created the Oracle Label Security policy, you are ready to create Database Vault rules to work with it.
-
Connect to SQL*Plus as the Database Vault Owner.
For example:
CONNECT leo_dvowner -- Or, CONNECT leo_dvowner@hrpdb Enter password: password
-
Create the following rule set:
EXEC DBMS_MACADM.CREATE_RULE_SET('PII Rule Set', 'Protect PII data from privileged users','Y',1,0,2,NULL,NULL,0,NULL); -
Create a rule for the PII Rule Set.
EXEC DBMS_MACADM.CREATE_RULE('Check OLS Factor', 'dominates(sa_utl.numeric_label(''PRIVACY''), char_to_label(''PRIVACY'',''S:PII'')) = ''1''');Ensure that you use single quotes, as shown in this example, and not double quotes.
-
Add the Check OLS Factor rule to the PII Rule Set.
EXEC DBMS_MACADM.ADD_RULE_TO_RULE_SET('PII Rule Set', 'Check OLS Factor');
Step 4: Update the ALTER SYSTEM Command Rule to Use the Rule Set
Before the rule set can be used, you must update the ALTER SYSTEM command rule, which is a default command rule.
-
As the Database Vault Owner, check the current value of the ALTER SYSTEM command rule, which is one of the default command rules when you install Oracle Database Vault.
SELECT * FROM DVSYS.DBA_DV_COMMAND_RULE WHERE COMMAND = 'ALTER SYSTEM';
-
Make a note of these settings so that you can revert them to their original values later on.
In a default installation, the ALTER SYSTEM command rule uses the Allow Fine Grained Control of System Parameters rule set, and is enabled.
-
Update the ALTER SYSTEM command rule to be associated with the PII Rule Set.
EXEC DBMS_MACADM.UPDATE_COMMAND_RULE('ALTER SYSTEM', 'PII Rule Set', '%', '%', 'Y');This command adds the PII Rule Set to the ALTER SYSTEM command rule, applies it to all object owners and object names, and enables the command rule.
Step 5: Test the Authorizations
With all the components in place, you are ready to test the authorization.
-
In SQL*Plus, log on as user
mdale.CONNECT mdale -- Or, CONNECT mdale@hrpdb Enter password: password
-
Check the current setting for the
AUDIT_TRAILinitialization parameter.SHOW PARAMETER AUDIT_TRAIL NAME TYPE VALUE ------------------------------------ ----------- ---------------------- audit_trail string DB
Make a note of this setting, so that you can revert it to its original setting later on.
-
As user
mdale, use theALTER SYSTEMstatement to modify theCPU_COUNTparameter.ALTER SYSTEM SET CPU_COUNT = 4; System altered.
Because user
mdalewas assigned the Sensitive label with the PII compartment, he can use theALTER SYSTEMstatement to modify theAUDIT_TRAILsystem parameter. -
Set the
CPU_COUNTparameter back to its original value.For example:
ALTER SYSTEM SET CPU_COUNT = 2;
-
Log in as user
jsmithand then issue the sameALTER SYSTEMstatement:CONNECT jsmith -- Or, CONNECT jsmith@hrpdb Enter password: password ALTER SYSTEM SET CPU_COUNT = 14;
The following output should appear:
ERROR at line 1: ORA-01031: insufficient privileges
Because user
jsmithwas assigned only the Confidential label, he cannot perform theALTER SYSTEMstatement.
Step 6: Remove the Components for This Tutorial
You can remove the components that you created for this tutorial if you no longer need them.
-
Connect as the Oracle Label Security administrator and remove the label policy and its components.
CONNECT LBACSYS -- Or, CONNECT LBACSYS@hrpdb Enter password: password EXEC SA_SYSDBA.DROP_POLICY('PRIVACY', TRUE);
-
Connect as the Oracle Database Vault Owner and issue the following commands in the order shown, to set the ALTER SYSTEM command rule back to its previous setting and remove the rule set.
For example:
CONNECT leo_dvowner Enter password: password EXEC DBMS_MACADM.UPDATE_COMMAND_RULE('ALTER SYSTEM', 'Allow System Parameters','%', '%', 'Y'); EXEC DBMS_MACADM.DELETE_RULE_FROM_RULE_SET('PII Rule Set', 'Check OLS Factor'); EXEC DBMS_MACADM.DELETE_RULE('Check OLS Factor'); EXEC DBMS_MACADM.DELETE_RULE_SET('PII Rule Set'); COMMIT; -
Connect as the Database Vault Account Manager and remove users
mdaleandjsmith.CONNECT bea_dvacctmgr -- Or, CONNECT bea_dvacctmgr@hrpdb Enter password: password DROP USER mdale; DROP USER jsmith;
Related Reports and Data Dictionary Views
Table 10-1 lists Oracle Database Vault reports that are useful for analyzing the integration of Oracle Database Vault and Oracle Label Security. See Chapter 24, "Oracle Database Vault Reports," for information about how to run these reports.
Table 10-1 Reports Related to Database Vault and Oracle Label Security Integration
| Report | Description |
|---|---|
|
Lists factors in which the Oracle Label Security policy does not exist. |
|
|
Lists invalid label identities (the Oracle Label Security label for this identity has been removed and no longer exists). |
|
|
Lists accounts and roles that have the |
Table 10-2 lists data dictionary views that provide information about existing Oracle Label Security policies used with Oracle Database Vault.
Table 10-2 Data Dictionary Views Used for Oracle Label Security
| Data Dictionary View | Description |
|---|---|
|
Lists the Oracle Label Security policies defined |
|
|
Lists the factors that are associated with Oracle Label Security policies |
|
|
Lists the Oracle Label Security label for each factor identifier in the |
Integrating Oracle Database Vault with Oracle Data Guard
This section covers the following topics:
Step 1: Configure the Primary Database
-
For Linux and UNIX systems, ensure there is an
/etc/oratabentry for the database on the node in which you are installing Oracle Database Vault. -
If you are using Data Guard Broker, then from the command prompt, disable the configuration as follows:
dgmgrl sys Enter password: password DGMGRL> disable configuration; -
Run Database Configuration Assistant (DBCA) and configure the database options to add Oracle Database Vault to the primary database.
-
From the command line, enter the following command to start DBCA:
dbca
-
Select the correct database type (Cluster or Single Instance) and click Next.
-
In the Database Operation page, select Configure Database Options and click Next.
-
Select the appropriate database and click Next.
-
Select Oracle Label Security, which then enables you to select Oracle Database Vault and click Next.
-
Enter the name of the Database Vault owner (required) and the Database Vault account manager (recommended).
Passwords must have at least one alphabetic character, one number, and one special character.
-
Click Next.
-
Choose appropriate connection mode and click Next.
-
Click OK to restart the database.
-
Click OK on Configure Additional Components.
At this point, the installation on the primary site is complete.
-
-
Log into the database instance as user
SYSwith theSYSDBAadministrative privilege.sqlplus sys as sysdba Enter password: password -
Run the following
ALTER SYSTEMstatements:ALTER SYSTEM SET AUDIT_SYS_OPERATIONS=TRUE SCOPE=SPFILE; ALTER SYSTEM SET OS_ROLES=FALSE SCOPE=SPFILE; ALTER SYSTEM SET RECYCLEBIN='OFF' SCOPE=SPFILE; ALTER SYSTEM SET REMOTE_LOGIN_PASSWORDFILE='EXCLUSIVE' SCOPE=SPFILE; ALTER SYSTEM SET SQL92_SECURITY=TRUE SCOPE=SPFILE; ALTER SYSTEM SET REMOTE_OS_AUTHENT=FALSE SCOPE=SPFILE; ALTER SYSTEM SET REMOTE_OS_ROLES=FALSE SCOPE=SPFILE;
-
Run the
ALTER SYSTEMstatement on each database instance to set the parameters as shown in Step 5. -
Restart each database instance.
CONNECT SYS AS SYSOPER Enter password: password SHUTDOWN IMMEDIATE STARTUP
Step 2: Configure the Standby Database
-
Log into the database instance as user
SYSwith theSYSDBAadministrative privilege.sqlplus sys as sysdba Enter password: password -
In a multitenant environment, connect to the appropriate PDB.
For example:
CONNECT bea_dvacctmgr@hrpdb Enter password: passwordTo find the available PDBs, query the
DBA_PDBSdata dictionary view. To check the current PDB, run theshow con_namecommand. -
Mount a standby database instance.
ALTER DATABASE MOUNT STANDBY DATABASE;
-
Run the following
ALTER SYSTEMstatements:ALTER SYSTEM SET AUDIT_SYS_OPERATIONS=TRUE SCOPE=SPFILE; ALTER SYSTEM SET OS_ROLES=FALSE SCOPE=SPFILE; ALTER SYSTEM SET RECYCLEBIN='OFF' SCOPE=SPFILE; ALTER SYSTEM SET REMOTE_LOGIN_PASSWORDFILE='EXCLUSIVE' SCOPE=SPFILE; ALTER SYSTEM SET SQL92_SECURITY=TRUE SCOPE=SPFILE; ALTER SYSTEM SET REMOTE_OS_AUTHENT=FALSE SCOPE=SPFILE; ALTER SYSTEM SET REMOTE_OS_ROLES=FALSE SCOPE=SPFILE;
-
Restart or mount the database instance.
For example:
SHUTDOWN IMMEDIATE STARTUP
-
Mount the next standby instance.
-
Restart the managed recovery as follows:
ALTER DATABASE RECOVER MANAGED STANDBY DATABASE USING CURRENT LOGFILE THROUGH ALL SWITCHOVER DISCONNECT;
-
If you are using Data Guard Broker, then from the command line, re-enable the configuration.
dgmgrl sys Enter password: password DGMGRL> enable configuration;This command applies the changes to the physical standby database made by the Oracle Database Vault installation on the primary database.
-
Repeat the physical standby installation process on each physical standby database. For example, if there are three physical standby databases, then run these procedures or each standby database.