2 Securing the Database Installation and Configuration
You should secure the Oracle Database installation, the network it users, and database user accounts.
Topics:
-
Oracle Database Security Guide for detailed information about security
-
Oracle Database Security Guide for important security guidelines
About Securing the Database Installation and Configuration
After you install Oracle Database, you should secure the database installation and configuration.
Oracle provides commonly used ways to do secure the database installation and configuration, all of which involve restricting permissions to specific areas of the database files.
Oracle Database is available on several operating systems. Consult the following guides for detailed platform-specific information about Oracle Database:
-
Oracle Database Administrator's Reference for Linux and UNIX-Based Operating Systems
-
Oracle Database Installation Guide for your platform
Securing Access to the Oracle Database Installation
Oracle Database provides a set a default security settings and initialization parameters that help you secure your installation. In addition, you should secure the data dictionary.
Topics:
Default Security Settings
When you create a new database, Oracle Database provides a set of default security settings.
These default security settings are as follows:
-
Enables default auditing settings. See Oracle Database Security Guide for detailed information.
-
Creates stronger enforcements for new or changed passwords. "Requirements for Creating Passwords" describes the new password requirements.
-
Removes the CREATE EXTERNAL JOB privilege from the PUBLIC role. For greater security, grant the
CREATE EXTERNAL JOBprivilege only toSYS, database administrators, and those trusted users who need it. -
Sets security-related initialization and profile parameter settings. Table 2-1 lists the default parameter settings.
Security for the Oracle Data Dictionary
You should secure the data dictionary. The data dictionary is a set of database tables that provide information about the database, such as schema definitions or default values.
Topics:
About the Oracle Data Dictionary
The Oracle data dictionary is a set of database tables that provides information about the database.
The data dictionary has the following contents:
-
The names of Oracle Database users
-
Privileges and roles granted to each user
-
The definitions of all schema objects in the database (tables, views, indexes, clusters, synonyms, sequences, procedures, functions, packages, triggers, and so on)
-
The amount of space allocated for, and is currently used by, the schema objects
-
Default values for columns
-
Integrity constraint information
-
Auditing information, such as who has accessed or updated various schema objects
-
Other general database information
The data dictionary tables and views for a given database are stored in the SYSTEM tablespace for that database. All the data dictionary tables and views for a given database are owned by the user SYS. Connecting to the database with the SYSDBA administrative privilege gives full access to the data dictionary. Oracle strongly recommends limiting access to the SYSDBA administrative privilege to only those operations necessary such as patching and other administrative operations. The data dictionary is central to every Oracle database.
You can view the contents of the data dictionary by querying data dictionary views, which are described in Oracle Database Reference. Be aware that not all objects in the data dictionary are exposed to users. A subset of data dictionary objects, such as those beginning with USER_ are exposed as read only to all database users.
Example 2-1 shows how you can find a list of database views specific to the data dictionary by querying the DICTIONARY view.
Enabling Data Dictionary Protection
You can protect the data dictionary by setting the O7_DICTIONARY_ACCESSIBILITY initialization parameter to FALSE.
The O7_DICTIONARY_ACCESSIBILITY parameter prevents users who have the ANY system privilege from using those privileges on the data dictionary, that is, on objects in the SYS schema.
Oracle Database provides highly granular privileges. One such privilege, commonly referred to as the ANY privilege, should typically be granted to only application owners and individual database administrators. For example, you could grant the DROP ANY TABLE privilege to an application owner. You can protect the Oracle data dictionary from accidental or malicious use of the ANY privilege by turning on or off the O7_DICTIONARY_ACCESSIBILITY initialization parameter.
To enable data dictionary protection:
-
Access the Database home page.
See Oracle Database 2 Day DBA for more information.
-
From the Administration menu, select Initialization Parameters.
If the Database Login page appears, then log in as
SYSwith the SYSDBA role selected. -
In the Initialization Parameters page, from the list, search for
O7_DICTIONARY_ACCESSIBILITY.In the Name field, enter
O7_(the letterO), and then click Go. You can enter the first few characters of a parameter name. In this case,O7_displays theO7_DICTIONARY_ACCESSIBILTYparameter. -
Set the value for
O7_DICTIONARY_ACCESSIBILTYtoFALSE. -
Click Apply.
-
Restart the Oracle Database instance.
sqlplus sys as sysdba Enter password: password SQL> SHUTDOWN IMMEDIATE SQL> STARTUP
-
In a default installation, the
O7_DICTIONARY_ACCESSIBILITYparameter is set toFALSE. -
The
SELECT ANY DICTIONARYprivilege is not included in theGRANT ALL PRIVILEGESstatement, but you can grant it through a role. Roles are described in "When to Grant Roles to Users" and Oracle Database Security Guide.
Initialization Parameters Used for Installation and Configuration Security
Oracle Database provides a set of initialization parameters for setting installation and configuration security.
Table 2-2 lists initialization parameters that you can set to better secure your Oracle Database installation and configuration.
Table 2-2 Initialization Parameters Used for Installation and Configuration Security
| Initialization Parameter | Default Setting | Description |
|---|---|---|
|
|
|
Controls the display of the product version information, such as the release number, in a client connection. An intruder could use the database release number to find information about security vulnerabilities that may be present in the database software. You can enable or disable the detailed product version display by setting this parameter. See Oracle Database Security Guide for more information about this and similar parameters. Oracle Database Reference describes this parameter in detail. |
|
|
|
Controls restrictions on |
Oracle Database Reference for more information about initialization parameters
Modifying the Value of an Initialization Parameter
You can use Enterprise Manager to modify the value of an initialization parameter.
To find detailed information about the initialization parameters available, see Oracle Database Reference.
To modify the value of an initialization parameter:
-
Access the Database home page.
See Oracle Database 2 Day DBA for more information.
-
From the Administration menu, select Initialization Parameters.
If the Database Login page appears, then log in as
SYSwith the SYSDBA role selected. -
In the Initialization Parameters page, in the Name field, enter the name of the parameter to change, and then click Go.
You can enter the first few letters of the parameter, for example,
SEC_RETURNif you are searching for theSEC_RETURN_SERVER_RELEASE_NUMBERparameter. Alternatively, you can scroll down the list of parameters to find the parameter you want to change. The text is not case sensitive. -
In the Value field, either enter the new value or if a list is presented, select from the list.
-
Click Apply.
-
If the parameter is static, then restart the Oracle Database instance.
sqlplus sys as sysdba Enter password: password SQL> SHUTDOWN IMMEDIATE SQL> STARTUPTo find out if an initialization parameter is static, check its description in Oracle Database Reference. If the Modifiable setting in its summary table shows No, then you must restart the database instance.
Security for the Network
Not only must you secure data within a database, but you must secure how the data is accessed from and sent to the database. Oracle provides ways that enable you to protect client connections and encrypt (disguise) data that travels through the network between the client and the server.
Topics:
About Securing the Network
When you encrypt data as it travels through the network, you should follow guidelines to secure the network connections for Oracle Database.
You can configure the client connection to your Oracle Database installation by following the procedures in "Configuring the Network Environment" in Oracle Database 2 Day DBA and the Oracle Database Installation Guide for your platform.
Protecting Data on the Network by Using Network Encryption
In addition to protecting information by encrypting it at the database level, you must protect it as it travels across the network.
Topics:
About Network Encryption
Network encryption refers to encrypting data as it travels across the network between the client and server.
The reason that you should encrypt data at the network level, and not just the database level, is because data can be exposed on the network level. For example, an intruder can use a network packet sniffer to capture information as it travels on the network, and then spool it to a file for malicious use. Encrypting data on the network prevents this sort of activity.
To encrypt data on the network, you must have the following components:
-
An encryption seed. The encryption seed is a random string of up to 256 characters. It generates the cryptographic keys that encrypts data as it travels across the network.
-
An encryption algorithm. You can specify any of the supported algorithm types: AES, RC4, DES, or 3DES.
-
Whether the settings apply to a client or server. You must configure the server and each client to which it connects.
-
How the client or server should processes the encrypted data. The settings you select (you have four options) must complement both server and client.
-
A mechanism for configuring the encryption. You can use Oracle Net Manager to configure the encryption. Alternatively, you can edit the
sqlnet.oraconfiguration file. Both Oracle Net Manager and thesqlnet.orafile are available in a default Oracle Database installation.
Configuring Network Encryption
You can configure network encryption by using either Oracle Net Manager or by editing the sqlnet.ora file.
To configure network encryption:
-
On the server computer, start Oracle Net Manager.
-
UNIX: From
$ORACLE_HOME/bin, enter the following at the command line:netmgr
-
Windows: From the Start menu, click All Programs. Then, click Oracle - HOME_NAME, Configuration and Migration Tools, and then Net Manager
-
-
From the Oracle Net Configuration navigation tree, expand Local, and then select Profile.
-
From the list, select Network Security.
-
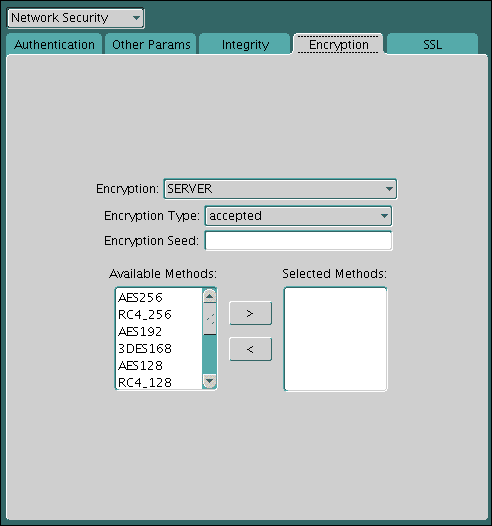
Under Network Security, select the Encryption tab.
The Encryption settings pane appears.
-
-
Encryption: From the list, select SERVER to configure the network encryption for the server. (For the client computer, you select CLIENT.)
-
Encryption Type: Select from the following values to specify the actions of the server (or client) when negotiating encryption and integrity:
-
accepted: Service will be active if the other side of the connection specifies either required or requested, and there is a compatible algorithm available on the receiving database; it will otherwise be inactive.
-
rejected: Service must not be active, and the connection will fail if the other side requires any of the methods in this list.
-
requested: Service will be active if the other side of the connection specifies either accepted, required, or requested, and there is a compatible algorithm available on the other side. Otherwise, the service is inactive.
-
required: Service must be active, and the connection will fail if the other side specifies rejected, or if there is no compatible algorithm on the other side.
-
-
Encryption Seed: Enter a random string of up to 256 characters. Oracle Database uses the encryption seed to generate cryptographic keys. This is required when either encryption or integrity is enabled.
If you choose to use special characters such as a comma [,] or a right parenthesis [)] as a part of the Encryption Seed parameter, enclose the value within single quotation marks.
-
Available Methods: Select one or more of the following algorithms, and use the move button (>) to move them to the Selected Methods list. The order in which they appear in the Selected Methods list determines the preferred order for negotiation. That is, the first algorithm listed is selected first, and so on.
-
AES256: Advanced Encryption Standard (AES). AES was approved by the National Institute of Standards and Technology (NIST) to replace Data Encryption Standard (DES). AES256 enables you to encrypt a block size of 256 bits.
-
RC4_256: Rivest Cipher 4 (RC4), which is the most commonly used stream cipher that protects protocols such as Secure Sockets Layer (SSL). RC4_256 enables you to encrypt up to 256 bits of data.
-
AES192: Enables you to use AES to encrypt a block size of 192 bits.
-
3DES168: Triple Data Encryption Standard (TDES) with a three-key option. 3DES168 enables you to encrypt up to 168 bits of data.
-
AES128: Enables you to use AES to encrypt a block size of 128 bits.
-
RC4_128: Enables you to use RC4 to encrypt up to 128 bits of data.
-
3DES112: Enables you to use Triple DES with a two-key (112 bit) option.
-
DES: Data Encryption Standard (DES) 56-bit key. Note that National Institute of Standards and Technology (NIST) no longer recommends DES.
-
RC4_40: Enables you to use RC4 to encrypt up to 40 bits of data. (Not recommended.)
-
DES40: Enables you to use DES to encrypt up to 40 bits of data. (Not recommended.)
-
-
-
From the File menu, select Save Network Configuration, and then select Exit to exit Oracle Net Manager.
-
Repeat these steps for each client computer that connects to the server.
-
Oracle Database Net Services Reference for information about editing the
sqlnet.orafile parameters to configure network encryption
Initialization Parameters Used for Network Security
Oracle Database provides a set of initialization parameters for configuring network security.
Table 2-3 lists initialization parameters that you can set to better secure user accounts.
Table 2-3 Initialization Parameters Used for Network Security
| Initialization Parameter | Default Setting | Description |
|---|---|---|
|
|
|
Specifies a prefix that Oracle Database uses to identify users attempting to connect to the database. Oracle Database concatenates the value of this parameter to the beginning of the user operating system account name and password. When a user attempts a connection request, Oracle Database compares the prefixed username with user names in the database. |
|
|
No default setting |
Specifies a network name that resolves to an address or address list of Oracle Net remote listeners (that is, listeners that are not running on the same computer as this instance). The address or address list is specified in the |
|
|
|
Specifies whether remote clients will be authenticated with the value of the |
|
|
|
Specifies whether operating system roles are allowed for remote clients. The default value, |
To modify an initialization parameter, see "Modifying the Value of an Initialization Parameter". For detailed information about initialization parameters, see Oracle Database Reference andOracle Database Administrator's Guide.
Securing User Accounts
Oracle Database provides a set of predefined user accounts. You should create passwords in a secure fashion. If you have default passwords, you should change these. Oracle Database also provides a set of parameters that you can use to secure user accounts.
Topics:
-
Oracle Database Security Guide for detailed information about securing user accounts
-
Oracle Database Security Guide for important guidelines on securing user accounts
About Securing Oracle Database User Accounts
You can use many methods to secure both common and local database user accounts.
For example, Oracle Database has a set of built-in protections for passwords. You can safeguard default database accounts and passwords, and use various ways to manage database accounts.
Oracle Database 2 Day DBA describes the fundamentals of creating and administering user accounts, including how to manage user roles, what the administrative accounts are, and how to use profiles to establish a password policy.
After you create user accounts, you can use the procedures in this section to further secure these accounts by following these methods:
-
Safeguarding predefined database accounts. When you install Oracle Database, it creates a set of predefined accounts. You should secure these accounts as soon as possible by changing their passwords. You can use the same method to change all passwords, whether they are with regular user accounts, administrative accounts, or predefined accounts. This guide also provides guidelines on how to create the most secure passwords.
-
Managing database accounts. You can expire and lock database accounts.
-
Managing passwords. You can manage and protect passwords by setting initialization parameters. Oracle Database Reference describes the initialization parameters in detail.
Predefined User Accounts Provided by Oracle Database
When you install Oracle Database, the installation process creates a set of predefined administrative, non-administrative, and sample schema user accounts in the database.
Topics:
Predefined Administrative Accounts
A default Oracle Database installation provides a set of predefined administrative accounts.
These are accounts that have special privileges required to administer areas of the database, such as the CREATE ANY TABLE or ALTER SESSION privilege, or EXECUTE privileges on packages owned by the SYS schema. The default tablespace for administrative accounts is either SYSTEM or SYSAUX. In a multitenant environment, the predefined administrative accounts reside in the root database.
To protect these accounts from unauthorized access, the installation process expires and locks most of these accounts, except where noted in Table 2-4. As the database administrator, you are responsible for unlocking and resetting these accounts, as described in "Expiring and Locking Database Accounts".
Table 2-4 lists the administrative user accounts provided by Oracle Database.
Table 2-4 Predefined Oracle Database Administrative User Accounts
| User Account | Description | Status After Installation |
|---|---|---|
|
|
An account that allows HTTP access to Oracle XML DB. It is used in place of the EPG is a Web server that can be used with Oracle Database. It provides the necessary infrastructure to create dynamic applications. |
Expired and locked |
|
|
The internal account used by the unified audit feature to store unified audit trail records. |
Expired and locked |
|
|
The account used to administer Oracle Text. Oracle Text enables you to build text query applications and document classification applications. It provides indexing, word and theme searching, and viewing capabilities for text. |
Expired and locked |
|
|
The account used by the Management Agent component of Oracle Enterprise Manager to monitor and manage the database. See Oracle Enterprise Manager Grid Control Installation and Basic Configuration. |
Open Password is created at installation or database creation time. |
|
|
The account used to administer Oracle Label Security (OLS). It is created only when you install the Label Security custom option. See Enforcing Row-Level Security with Oracle Label Security, and Oracle Label Security Administrator's Guide. |
Expired and locked |
|
|
The Oracle Spatial and Oracle Multimedia Locator administrator account. |
Expired and locked |
|
|
The account that owns the OLAP Catalog (CWMLite). This account has been deprecated, but is retained for backward compatibility. |
Expired and locked |
|
|
This account contains the Oracle Multimedia DICOM data model. See Oracle Multimedia DICOM Developer's Guide for more information. |
Expired and locked |
|
|
The Oracle Multimedia user. Plug-ins supplied by Oracle and third-party, format plug-ins are installed in this schema. Oracle Multimedia enables Oracle Database to store, manage, and retrieve images, audio, video, DICOM format medical images and other objects, or other heterogeneous media data integrated with other enterprise information. See Oracle Multimedia User's Guide and Oracle Multimedia Reference. |
Expired and locked |
|
|
The Oracle Multimedia administrator account. See Oracle Multimedia User's Guide, Oracle Multimedia Reference, and Oracle Multimedia DICOM Developer's Guide. |
Expired and locked |
|
|
The account that stores the information views for the SQL/MM Still Image Standard. See Oracle Multimedia User's Guide and Oracle Multimedia Reference. |
Expired and locked |
|
|
An account used to perform database administration tasks. |
Open Password is created at installation or database creation time. |
|
|
The account used to perform Oracle Recovery Manager recovery and backup operations. |
Expired and locked |
|
|
The account used to perform Oracle Data Guard operations. |
Expired and locked |
|
|
The account used to manage Transparent Data Encryption. |
Expired and locked |
|
|
A default generic database administrator account for Oracle databases. For production systems, Oracle recommends creating individual database administrator accounts and not using the generic |
Open Password is created at installation or database creation time. |
|
|
The account used to store the metadata information for Oracle Workspace Manager. |
Expired and locked |
|
|
The account used for storing Oracle XML DB data and metadata. For better security, never unlock the Oracle XML DB provides high-performance XML storage and retrieval for Oracle Database data. |
Expired and locked |
If you create an Oracle Automatic Storage Management (Oracle ASM) instance, then the ASMSNMP account is created. Oracle Enterprise Manager uses this account to monitor ASM instances to retrieve data from ASM-related data dictionary views. The ASMSNMP account status is set to OPEN upon creation, and it is granted the SYSDBA administrative privilege. For more information, see Oracle Automatic Storage Management Administrator's Guide.
Predefined Non-Administrative User Accounts
A default Oracle Database installation provides a set of non-administrative user accounts.
Table 2-5 lists default non-administrative user accounts that are created when you install Oracle Database. .
Non-administrative user accounts only have the minimum privileges needed to perform their jobs. Their default tablespace is USERS. In a multitenant environment, the predefined non-administrative accounts reside in the root database
To protect these accounts from unauthorized access, the installation process locks and expires these accounts immediately after installation, except where noted in Table 2-5. As the database administrator, you are responsible for unlocking and resetting these accounts, as described in "Expiring and Locking Database Accounts".
Table 2-5 Predefined Oracle Database Non-Administrative User Accounts
Predefined Sample Schema User Accounts
If you install the sample schemas, then Oracle Database creates a set of sample user accounts. The sample schema user accounts are all non-administrative accounts, and their tablespace is USERS.
To protect these accounts from unauthorized access, the installation process locks and expires these accounts immediately after installation. As the database administrator, you are responsible for unlocking and resetting these accounts, as described in "Expiring and Locking Database Accounts". For more information about the sample schema accounts, see Oracle Database Sample Schemas.
Table 2-6 lists the sample schema user accounts, which represent different divisions of a fictional company that manufactures various products.
Table 2-6 Default Sample Schema User Accounts
| User Account | Description | Status After Installation |
|---|---|---|
|
|
The account used to manage the |
Expired and locked |
|
|
The account used to manage the |
Expired and locked |
|
|
The account used to manage the |
Expired and locked |
|
|
The account used to manage the |
Expired and locked |
|
|
The account used to manage the |
Expired and locked |
In addition to the sample schema accounts, Oracle Database provides another sample schema account, SCOTT. The SCOTT schema contains the tables EMP, DEPT, SALGRADE, and BONUS. The SCOTT account is used in examples throughout the Oracle Database documentation set. When you install Oracle Database, the SCOTT account is locked and expired.
Expiring and Locking Database Accounts
When you expire the password of a user, that password no longer exists. If you want to unexpire the password, you change the password of that account.
Locking an account preserves the user password and other account information, but makes the account unavailable to anyone who tries to log in to the database using that account. Unlocking it makes the account available again.
Oracle Database 2 Day DBA explains how you can use Enterprise Manager to unlock database accounts. You also can use Enterprise Manager to expire or lock database accounts.
To expire and lock a database account:
-
Access the Database home page.
See Oracle Database 2 Day DBA for more information.
-
From the Administration menu, select Security, then Users.
If the Database Login page appears, then log in as an administrative user, such as
SYSTEM.The Users page lists the user accounts created for the current database instance. The Account Status column indicates whether an account is expired, locked, or open.
-
In the Select column, select the account you want to expire, and then click Edit.
-
In the Edit User page, do one of the following:
-
To expire a password, click Expire Password now.
To unexpire the password, enter a new password in the Enter Password and Confirm Password fields. See "Requirements for Creating Passwords" for password requirements.
-
To lock the account, select Locked.
-
-
Click Apply.
Requirements for Creating Passwords
For greater security, Oracle provides a set of requirements for creating passwords.
When you create a user account, Oracle Database assigns a default password policy for that user. The password policy defines rules for how the password should be created, such as a minimum number of characters, when it expires, and so on. You can strengthen passwords by using password policies.
For greater security, follow these guidelines when you create passwords:
-
Make the password between 12 and 30 characters and numbers.
-
Use mixed case letters and special characters in the password. (See Oracle Database Security Guide for more information.)
-
Use the database character set for the password characters, which can include the underscore (
_), dollar ($), and number sign (#) characters. -
Do not use an actual word for the entire password.
Oracle Database Security Guide describes more ways that you can further secure passwords.
Finding and Changing Default Passwords
You can find and change default passwords that may have come from earlier releases of Oracle Database.
Topics:
About Finding and Changing Default Passwords
When you install Oracle Database, the default database user accounts, including administrative accounts, are created without default passwords.
Except for the administrative accounts whose passwords you create during installation (such as user SYS), the default user accounts arrive locked with their passwords expired. If you have upgraded from a previous release of Oracle Database, you may have database accounts that still have default passwords. These are default accounts that are created when you create a database, such as the HR, OE, and SCOTT accounts.
Security is most easily compromised when a default database user account still has a default password after installation. This is particularly true for the user account SCOTT, which is a well known account that may be vulnerable to intruders. Find accounts that use default passwords and then change their passwords.
-
Oracle Database Security Guide for additional methods of configuring password protection
Finding and Changing Default Passwords from SQL*Plus
You can use SQL*Plus to find and change default passwords.
To find and change default passwords:
-
Log into the database instance with administrative privileges.
sqlplus system Enter password: password -
Select from the
DBA_USERS_WITH_DEFPWDdata dictionary view.SELECT * FROM DBA_USERS_WITH_DEFPWD;
The
DBA_USERS_WITH_DEFPWDlists the accounts that still have user default passwords. For example:USERNAME ------------ SCOTT
-
Change the password for the accounts the
DBA_USERS_WITH_DEFPWDdata dictionary view lists.For example, to change the password for user
SCOTT, enter the following:PASSWORD SCOTT Changing password for SCOTT New password: password Retype new password: password Password changed
Replace
passwordwith a password that is secure, according to the guidelines listed in "Requirements for Creating Passwords". For greater security, do not reuse the same password that was used in previous releases of Oracle Database.Alternatively, you can use the
ALTER USERSQL statement to change the password:ALTER USER SCOTT IDENTIFIED BY password;
Finding and Changing Default Passwords from Enterprise Manager
You can use Enterprise Manager to change a user account passwords (not just the default user account passwords) if you have administrative privileges. Individual users can also use Enterprise Manager to change their own passwords.
To use Enterprise Manager to change the password of a database account:
-
Access the Database home page.
See Oracle Database 2 Day DBA for more information.
-
From the Administration menu, select Security, then Users.
If the Database Login page appears, then log in as an administrative user, such as
SYS. UserSYSmust log in with the SYSDBA role selected.The Users page lists the user accounts created for the current database instance. The Account Status column indicates whether an account is expired, locked, or open.
-
In the Select column, select the account you want to change, and then click Edit.
-
In the Edit User page, enter a new password in the Enter Password and Confirm Password fields.
-
Click Apply.
Parameters Used to Secure User Accounts
Oracle Database provides a set of parameters for securing user accounts.
Table 2-7 lists initialization and profile parameters that you can set to better secure user accounts.
Table 2-7 Initialization and Profile Parameters Used for User Account Security
| Parameter | Default Setting | Description |
|---|---|---|
|
|
|
Controls case sensitivity in passwords. |
|
|
|
Sets the maximum number of times a user is allowed to fail when connecting to an Oracle Call Interface (OCI) application. |
|
|
|
Sets the maximum times a user login is allowed to fail before locking the account. Note: You also can set limits on the number of times an unauthorized user (possibly an intruder) attempts to log in to Oracle Call Interface applications by using the |
|
|
No default setting |
Sets the number of days that a user has to change his or her password before it expires. |
|
|
No default setting |
Sets the number of days the user can use his or her current password. |
|
|
No default setting |
Sets the number of days an account will be locked after the specified number of consecutive failed login attempts. |
|
|
No default setting |
Specifies the number of password changes required before the current password can be reused. |
|
|
No default setting |
Specifies the number of days before which a password cannot be reused. |
You can use most of these parameters to create a user profile. See Oracle Database Security Guide for more information about user profile settings.
To modify an initialization parameter, see "Modifying the Value of an Initialization Parameter". For detailed information about initialization parameters, see Oracle Database Reference andOracle Database Administrator's Guide.